How to Use ThreatCast’s Intelligence to Improve Your Mobile App Security
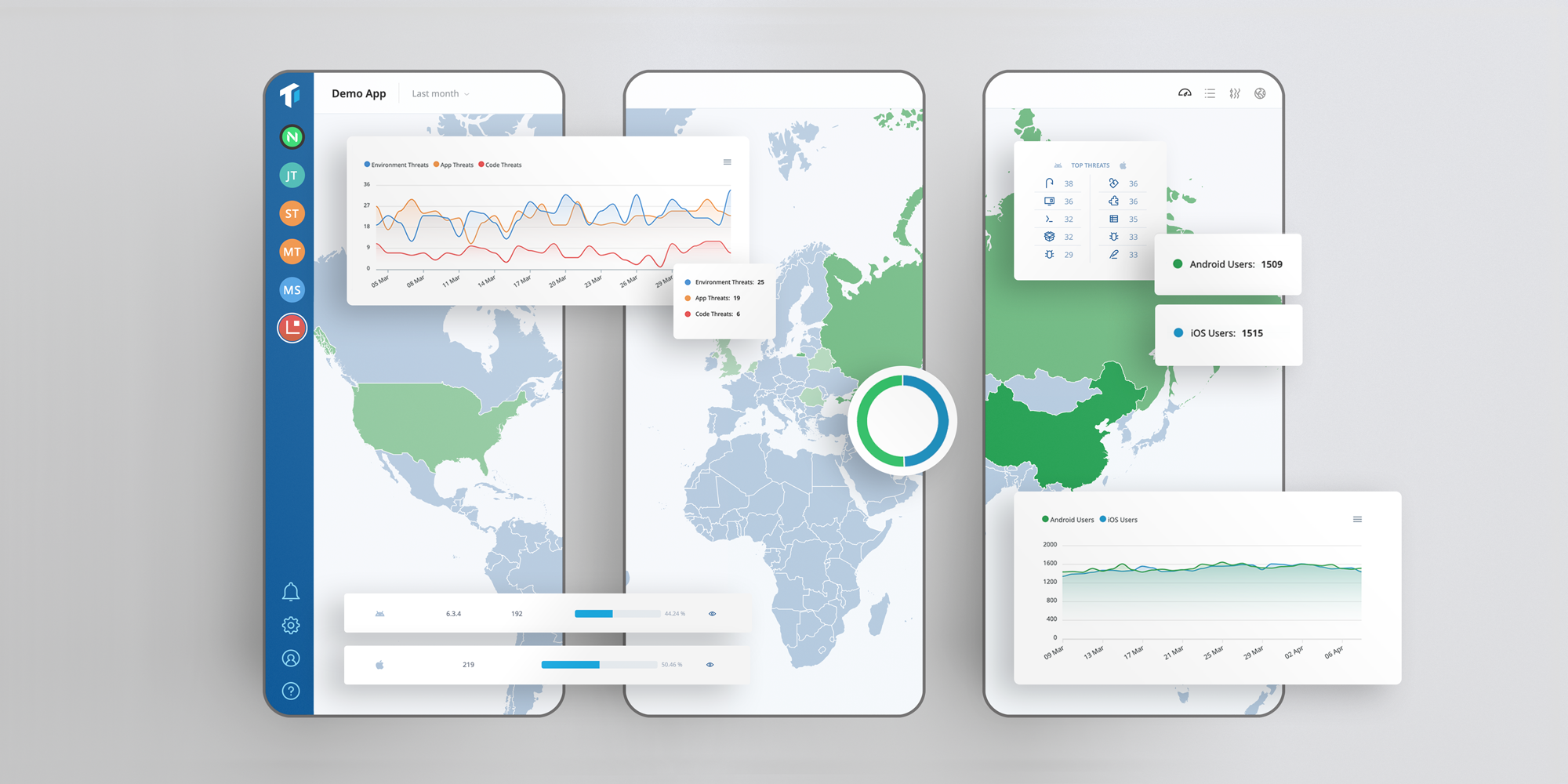
With the introduction of ThreatCast, Guardsquare’s new mobile app security console, Guardsquare enhances its offering in the mobile app security market. Combined with our app shielding solutions DexGuard (Android) and iXGuard (iOS), ThreatCast allows development and security teams to close the app security loop.
What does this mean? Most app developers lack reliable information about the actual threats facing their applications once they are released “into the wild.” Teams are left guessing about the effectiveness of their app security measures. ThreatCast allows both developers and security professionals to access information about detected application threats in real time, analyze attack vectors and implement new or improved app security measures based on objective data.
In this blog, we take a closer look at how organizations can leverage the threat intelligence collected by ThreatCast to adapt to the constantly evolving mobile threat landscape and respond to emerging attack vectors.
Analyzing Mobile Application Threats with ThreatCast
ThreatCast segments application threats into three categories:
- Environment threats
- App threats
- Code threats.
This categorization allows users to quickly and easily assess their level of risk, filter detected threat events, and set priorities to ensure maximum app security. For all of the detected threats in any of these three categories, ThreatCast displays a wealth of information enabling in-depth analysis based on:
- Type of attack
- Incidence rate
- Affected platform(s) and app version(s)
- Device(s)
- Geolocation
- And more.
Environment threats are threats related to the environment in which an application is executed, mostly (but not exclusively) the end-user’s device. This type of threat is logged whenever your DexGuard or iXGuard protected application detects that it is being run in a potentially harmful environment—such as a rooted or jailbroken device. The detected threats in this category are general security threats. They do not directly target mobile applications, but are often the basis for targeted attacks. In other words, when an environment threat appears in the ThreatCast dashboard, it does not necessarily mean your application has been compromised, but rather that there is potential for abuse. Related threats in the app or code threat categories should be carefully monitored.
Threats in this category include, but are not limited to:
- An application is executed on a rooted (Android) or jailbroken (iOS) device. Malicious users could make use of escalated privileges like access to root folders on these devices to bypass the system and security restrictions imposed by the respective operating systems.
- An application detects the presence of a debugger or another reverse engineering tool (such as a hooking framework). The presence of these tools may indicate that a malicious user is preparing to reverse engineer your app.
- An application is running in a mobile device emulator on a personal computer, instead of a mobile device. This may signal a malicious user is trying to understand the internal logic of your app.
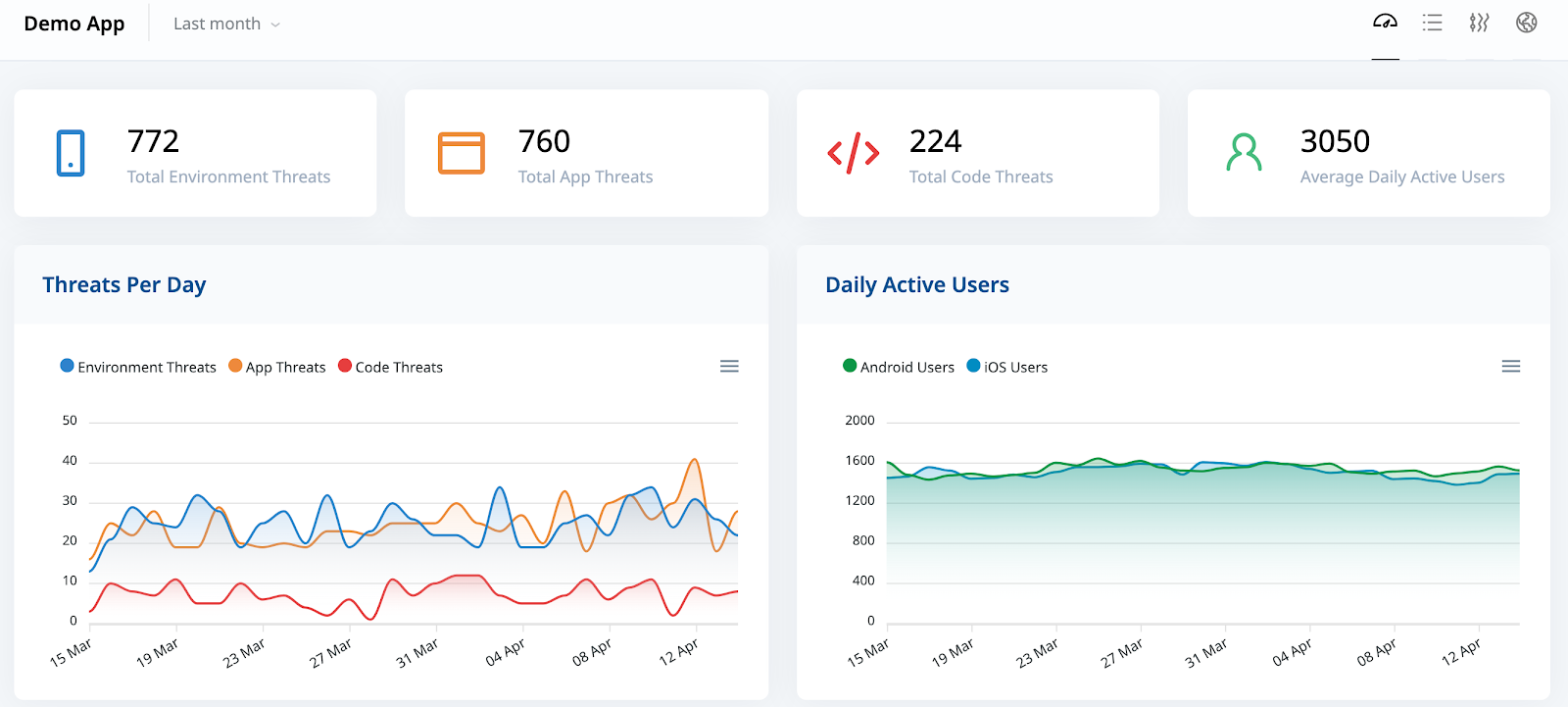
Figure 1 - ThreatCast dashboard, with overviews of environment threats (blue), app threats (orange), and code threats (red)
Application threats are threats related to the integrity of the application. An app threat is registered whenever the application package is modified. If this happens, DexGuard’s and iXGuard’s runtime application self-protection (RASP) functionality is automatically triggered to respond to the detected threat. Application threats are more acute than environment threats, because they indicate that there was an attempt to tamper with the application itself and possibly modify its behavior (see code threats).
Some examples of application threats:
- An application has been repackaged. The APK (Android) or IPA (iOS) on the end-users device is not identical to the one initially uploaded to the App Store or Play Store.
- An app was resigned. The certificates of the APK or IPA on the end-user’s device do not match the ones it was originally signed with. This is a clear indication that there was an attempt to tamper with your application.
- An app loads libraries that are different from the ones included by the app developer. This potentially alters the behavior of the application as library calls might result in a different system library response. Modifying or replacing libraries can be used among other things to pass incorrect location data to the app.
Code threats occur when someone attempts to statically or dynamically alter the internal logic of mobile applications and modify their intended behavior. Code threats are the most explicit indicators that malicious users are targeting specific mobile apps.
This category includes following threats and more:
- A function hook was detected. A dedicated function prologue has been rewritten to modify the behavior of your app at runtime.
- Symbol table rebinding was detected. Function table pointers are modified, potentially calling functions not included in original source code.
- Injected code was found. An application contains code that was not present when it was released.
How to Leverage the Data ThreatCast Collects
ThreatCast provides a wealth of information to help development teams and security professionals to make informed decisions about their mobile security strategies. Here are some ways to leverage the threat intelligence delivered by ThreatCast:
Strengthen Your App Protection to Defend Against Primary Attack vectors
ThreatCast shows you which of your app’s libraries or functions are primary targets for attacks, enabling you to reinforce the protection of these libraries and functions.This can be achieved by locally increasing the aggressiveness of the runtime self-protection (RASP) checks or by tweaking your code hardening configuration to add additional protection to specific parts of the application’s source code. In other words, DexGuard and iXGuard help you implement security best practices, while ThreatCast allows you to fine-tune your exact security protocols based on real threats.
Optimize Your App’s Response to Runtime Analysis and Live Attacks
DexGuard and iXGuard’s runtime application self-protection (RASP) functionality allows you to determine how your applications respond to detected runtime threats. The data provided by ThreatCast allow you to optimize your response strategy and decide based on objective data whether an application should terminate, limit the available functionality, or display a notification when a particular subcategory of threats is detected.
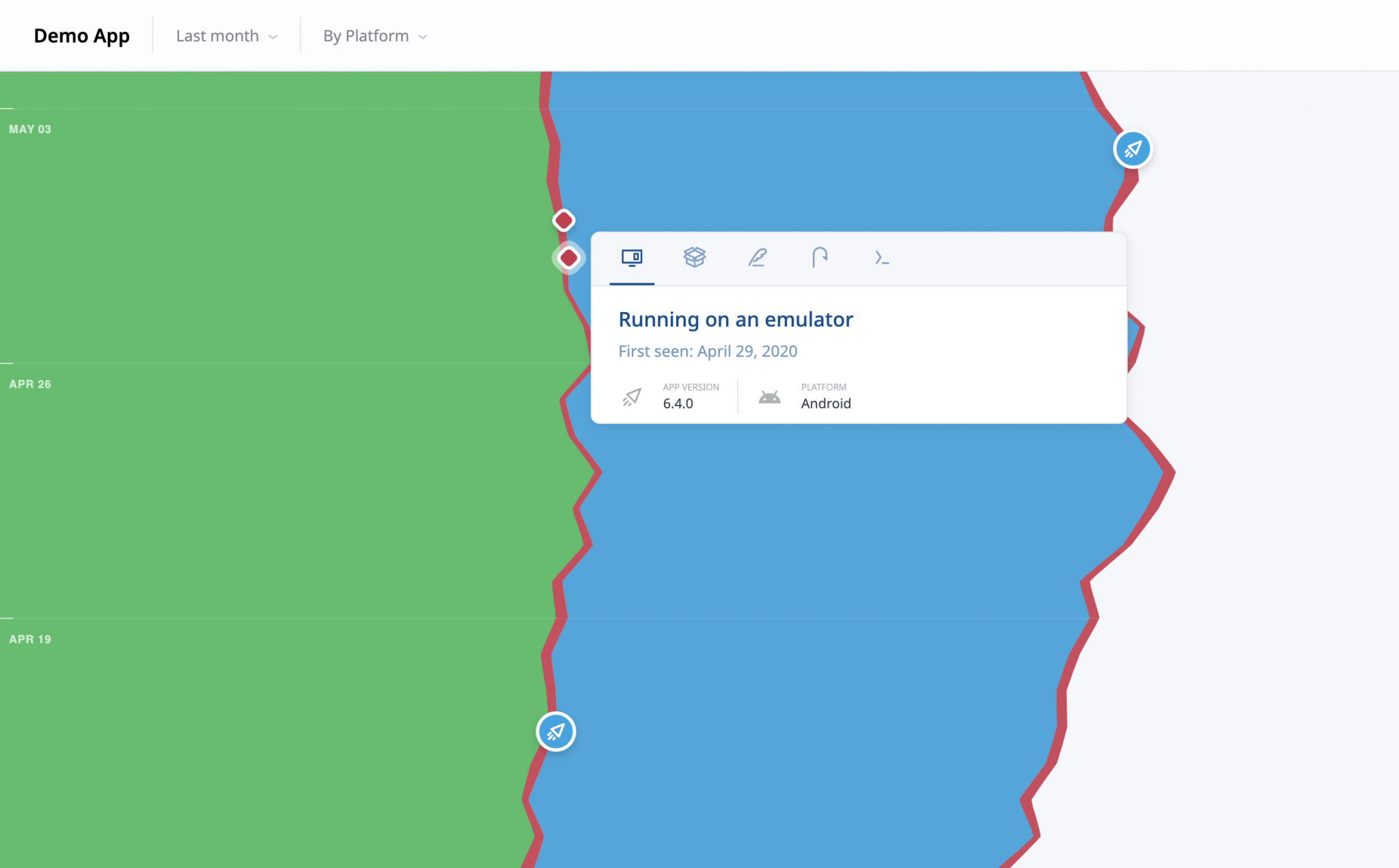
Figure 2 - ThreatCast Timeflow View: Allows teams to analyze app upgrade adoption (the green and blue bands), threats per app version (the red bands), and time-to-first-threat-detection (red milestones), all in one single view.
Adjust Release Frequency to Make Optimal use of DexGuard and iXGuard
The code hardening applied by DexGuard and iXGuard is polymorphic. In other words, the applied code protection is different in every single build, obliging malicious actors targeting applications to restart from zero after every new release. ThreatCast shows you the time it takes, on average, for attackers to compromise a new version of your application. This knowledge allows you to adjust your release frequency to optimally benefit from the polymorphic nature of the protection DexGuard and iXGuard provide and discourage malicious actors. The effectiveness of an optimized release cycle for security can be further improved by forcing all users to upgrade every time a new version is available.
A new level of visibility
After a mobile app is released to the app store, security teams and developers have historically lacked visibility into the most common attack vectors and vulnerable parts of their code. As this blog post illustrates, while DexGuard and iXGuard provide important and necessary layered security protections for Android and iOS mobile apps, ThreatCast brings a new level of visibility and clarity to the table. ThreatCast lets organizations identify specific threats in the wild, in real time, and enables teams to take action and shift their strategies to best respond to suspicious activity and malicious actors.





