-
Products
-
Solutions
-
Resources
-
Company
- Pricing
Products
Solutions
Resources
Company

Use ProGuard®, Guardsquare’s open-source shrinker for Java bytecode, to enhance and optimize your code.
The original Java optimizer for Android apps.

Use ProGuard to shrink any Java or Kotlin app, whether on mobile, embedded or on desktop.
ProGuard optimizes apps by reducing their size and improving performance, ensuring a more efficient and seamless user experience.
ProGuard is a command-line tool that reduces app size by shrinking bytecode; it obfuscates the names of classes, fields and methods. It’s an ideal fit for developers working with Java or Kotlin who are primarily interested in an Android optimizer.
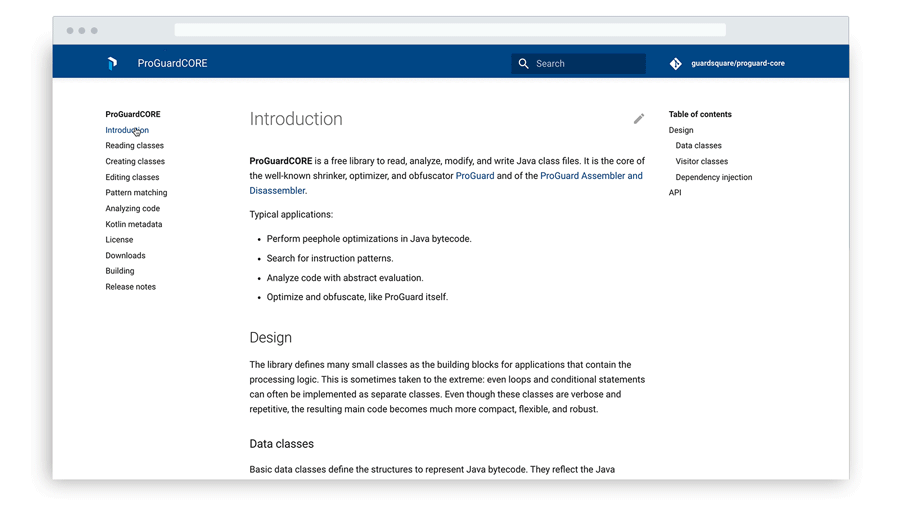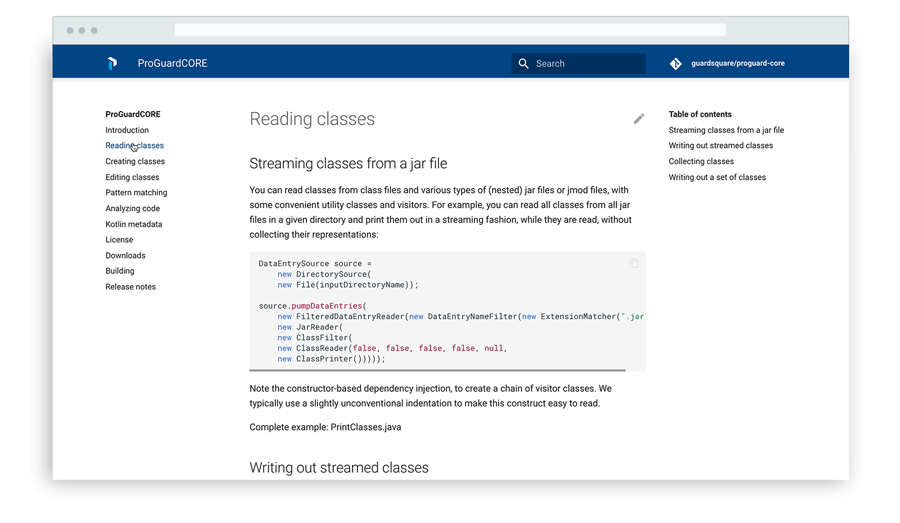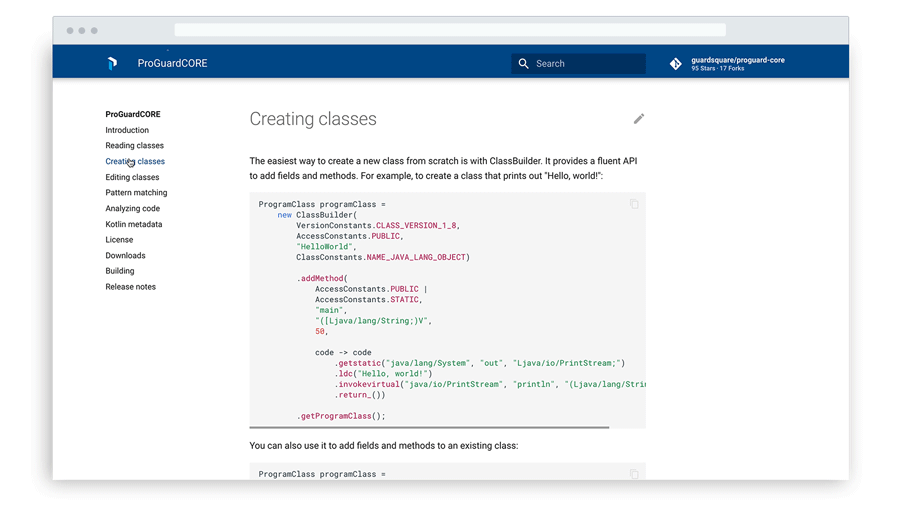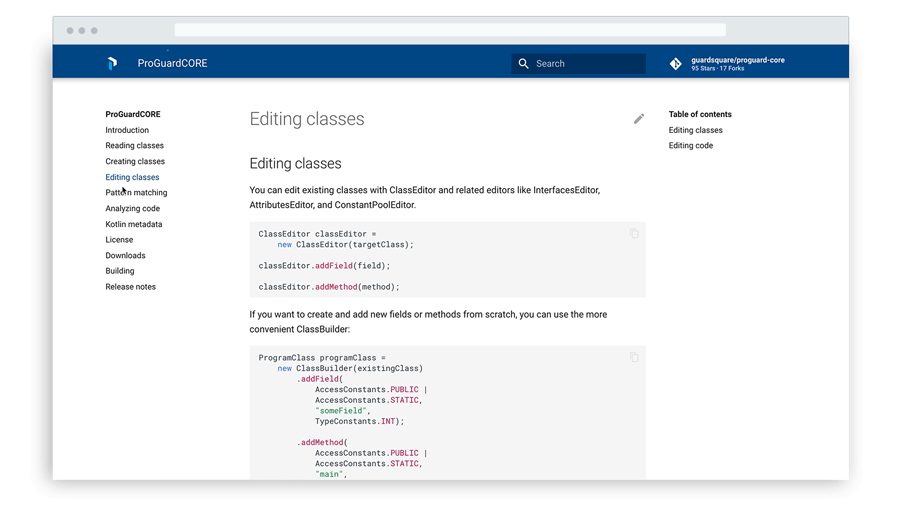
ProGuardCORE is a free and open-source library that serves as the core of ProGuard. What’s more, it was used as the basis for the ProGuard Assembler/Disassembler and the Kotlin Metadata Printer. Developers can use ProGuardCORE to integrate ProGuard’s code parsing capabilities into their own Java bytecode projects.
Read and write class files, including any Kotlin metadata
Search for instruction patterns
Create byte code instrumentation tools
Analyze code with abstract evaluation
Build static code analysis tools
Optimize and obfuscate, just like ProGuard itself
And more
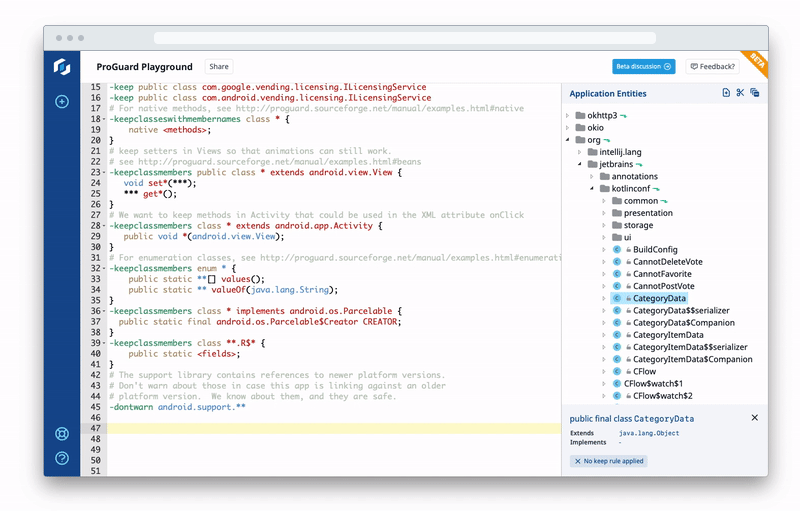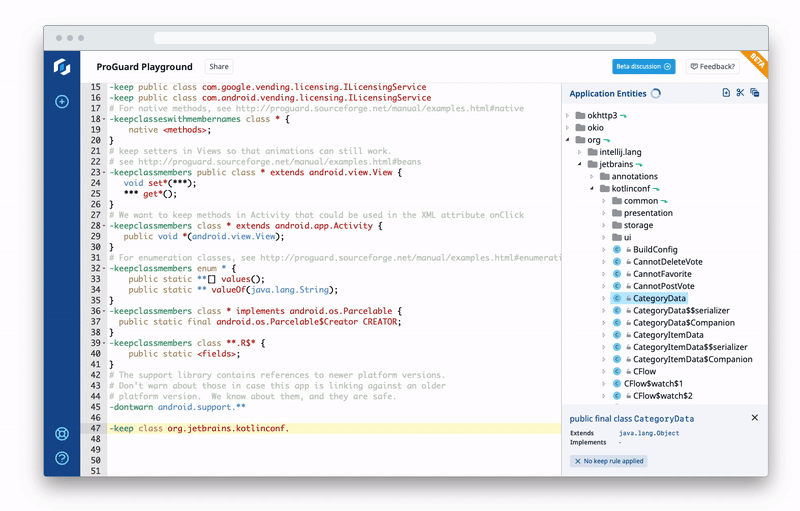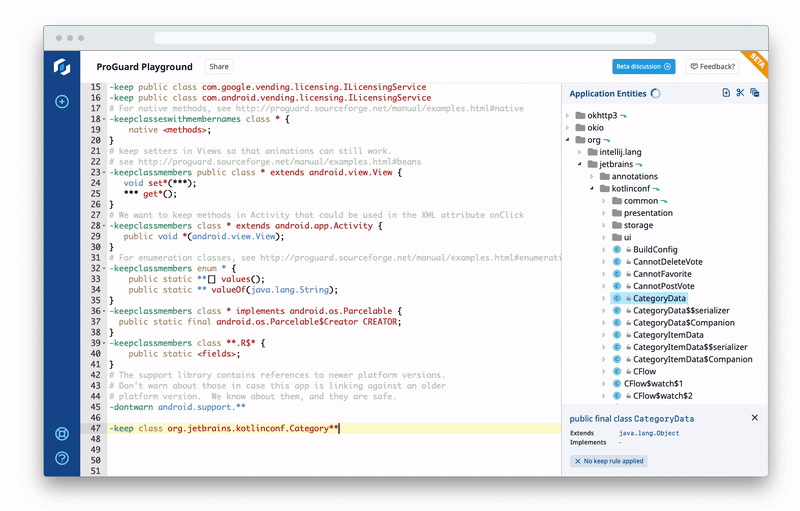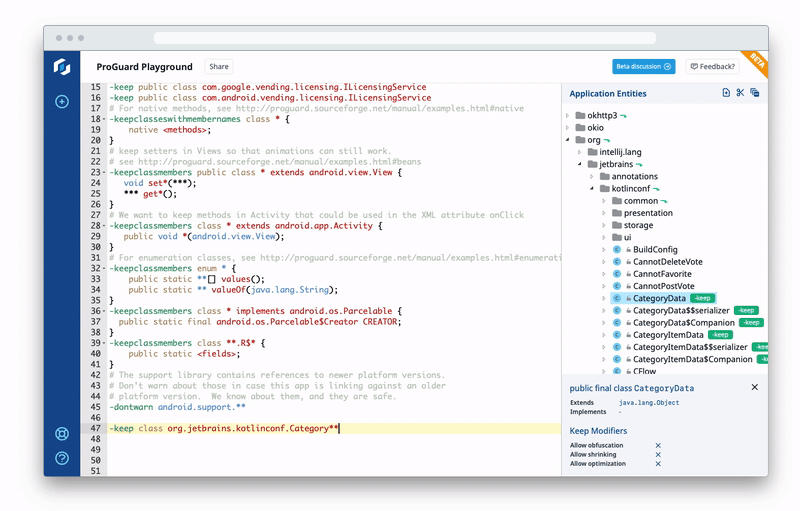
Using ProGuard Playground, you can experiment with and share your keep rules — that is, the rules that preserve your app’s libraries, resources, resource files and assets after ProGuard shrinks your mobile app — without needing to rebuild your app.

ProGuardCORE is a free and open-source library that serves as the core of ProGuard. What’s more, it was used as the basis for the ProGuard Assembler/Disassembler and the Kotlin Metadata Printer. Developers can use ProGuardCORE to integrate ProGuard’s code parsing capabilities into their own Java bytecode projects.
Read and write class files, including any Kotlin metadata
Search for instruction patterns
Create byte code instrumentation tools
Analyze code with abstract evaluation
Build static code analysis tools
Optimize and obfuscate, just like ProGuard itself
And more

Using ProGuard Playground, you can experiment with and share your keep rules — that is, the rules that preserve your app’s libraries, resources, resource files and assets after ProGuard shrinks your mobile app — without needing to rebuild your app.
Although ProGuard is a great start to mobile app optimization, its primary purpose is to shrink Java/Kotlin apps. DexGuard, our comprehensive Android mobile application security product provides protection from static and dynamic analysis through layered obfuscation and encryption techniques complemented by automated RASP checks and built-in malware defenses. DexGuard, integrates seamlessly with your existing ProGuard (or R8) configuration.