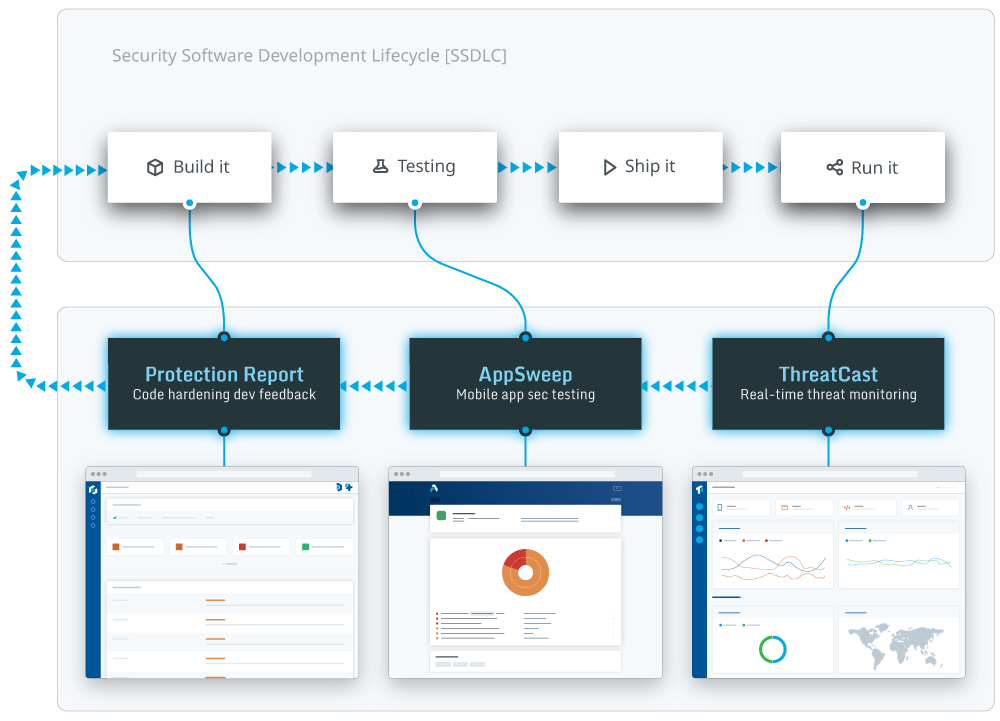
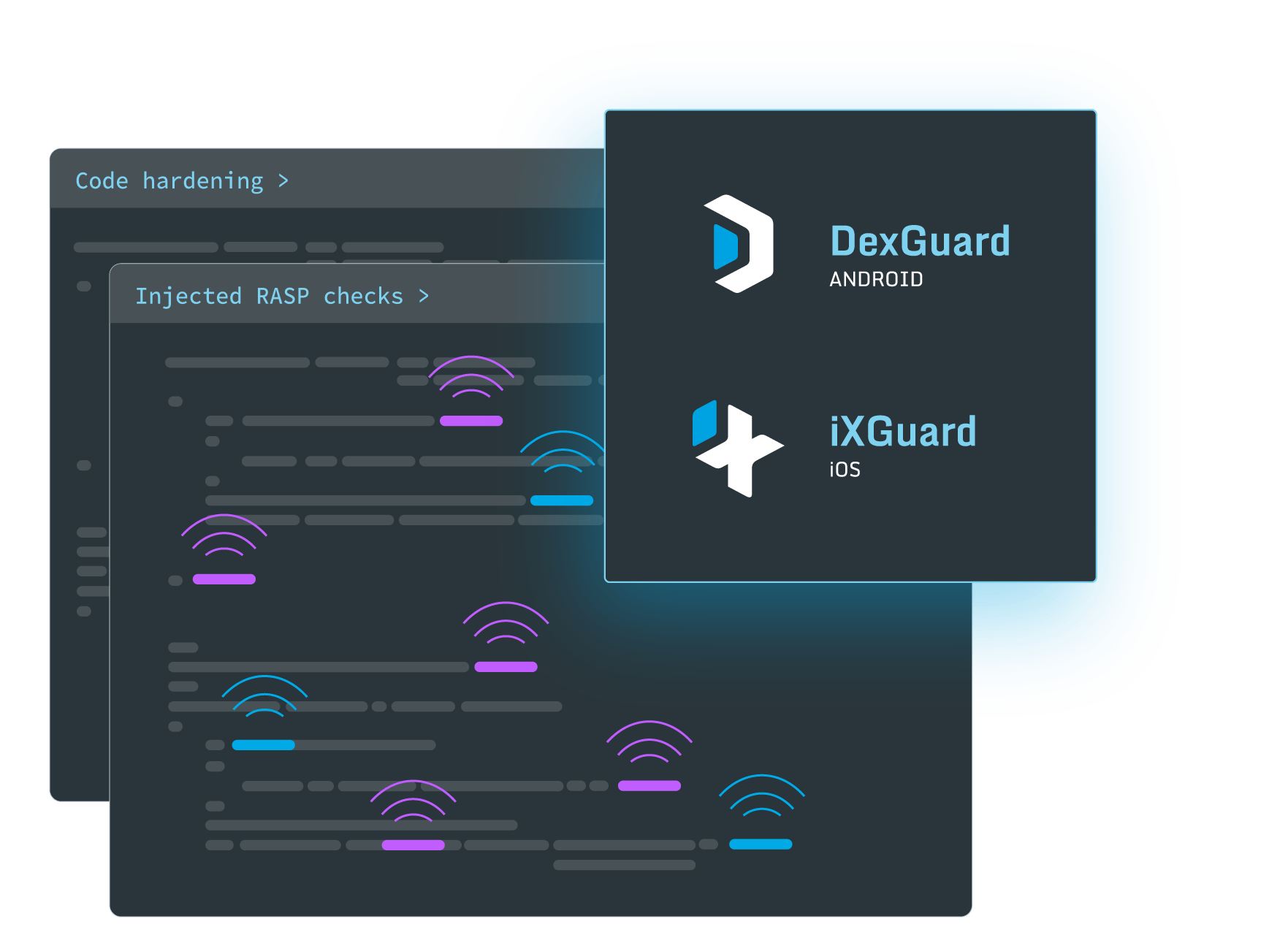
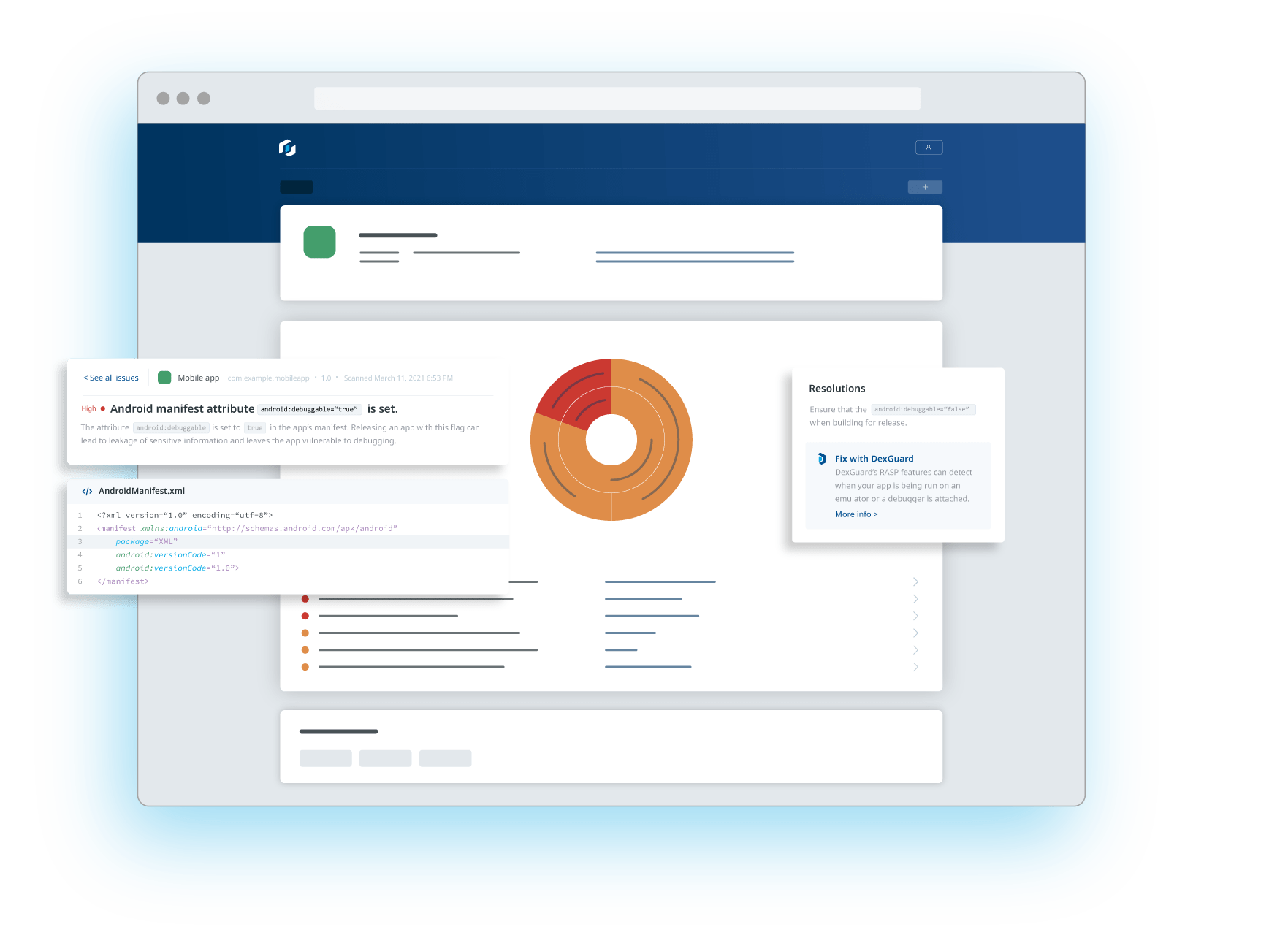
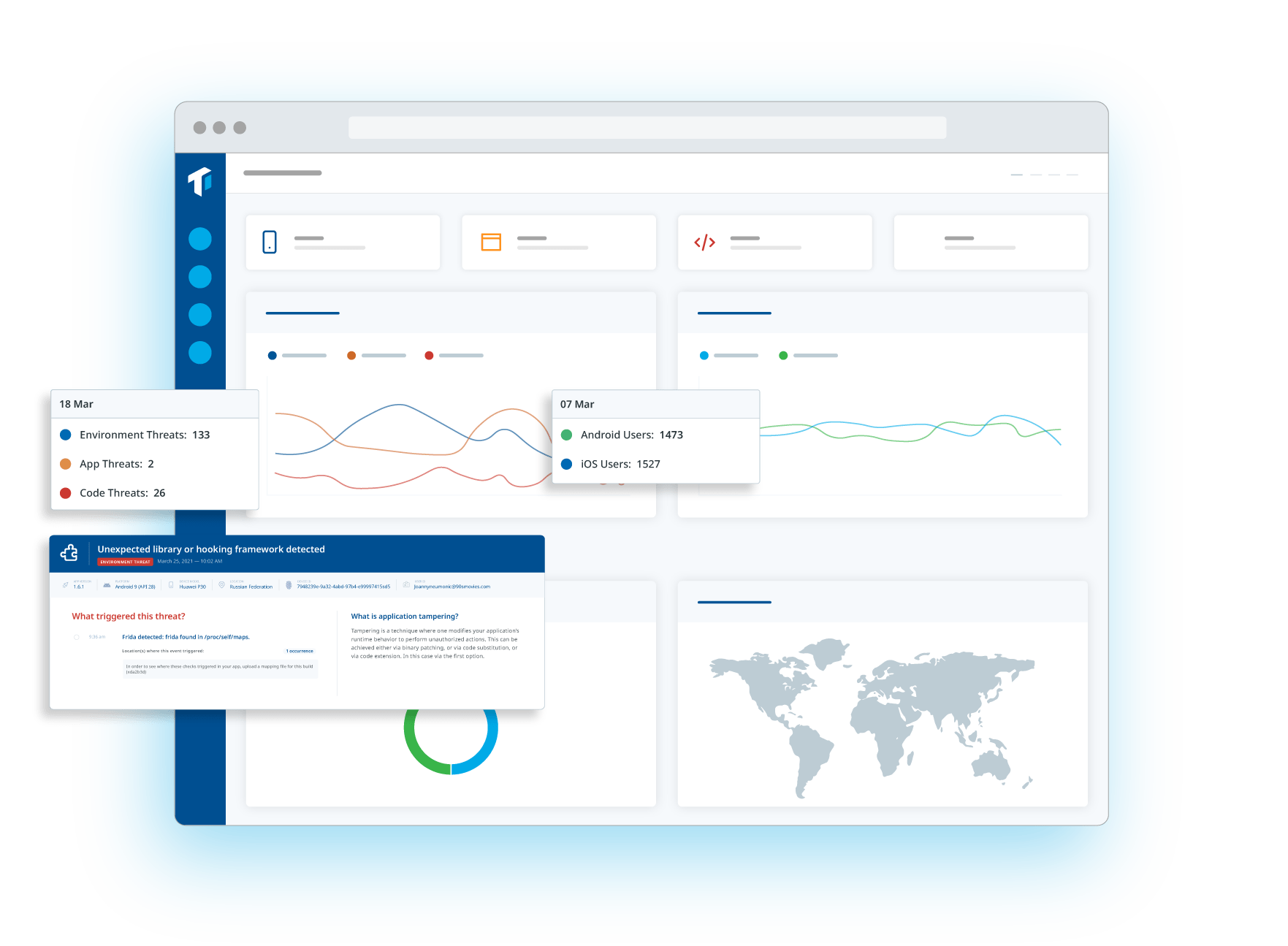
Mobile app security refers to the strategies, technologies, and best practices used to protect applications from cyber threats such as hacking, reverse engineering, and malware attacks. With mobile threats evolving rapidly, security is essential to prevent data breaches, protect intellectual property, and ensure regulatory compliance (e.g., GDPR, HIPAA). Guardsquare provides advanced code hardening, runtime application self-protection (RASP), and threat monitoring to safeguard apps from real-world attacks.
-
Products
-
Solutions
-
Resources
-
Company
- Pricing