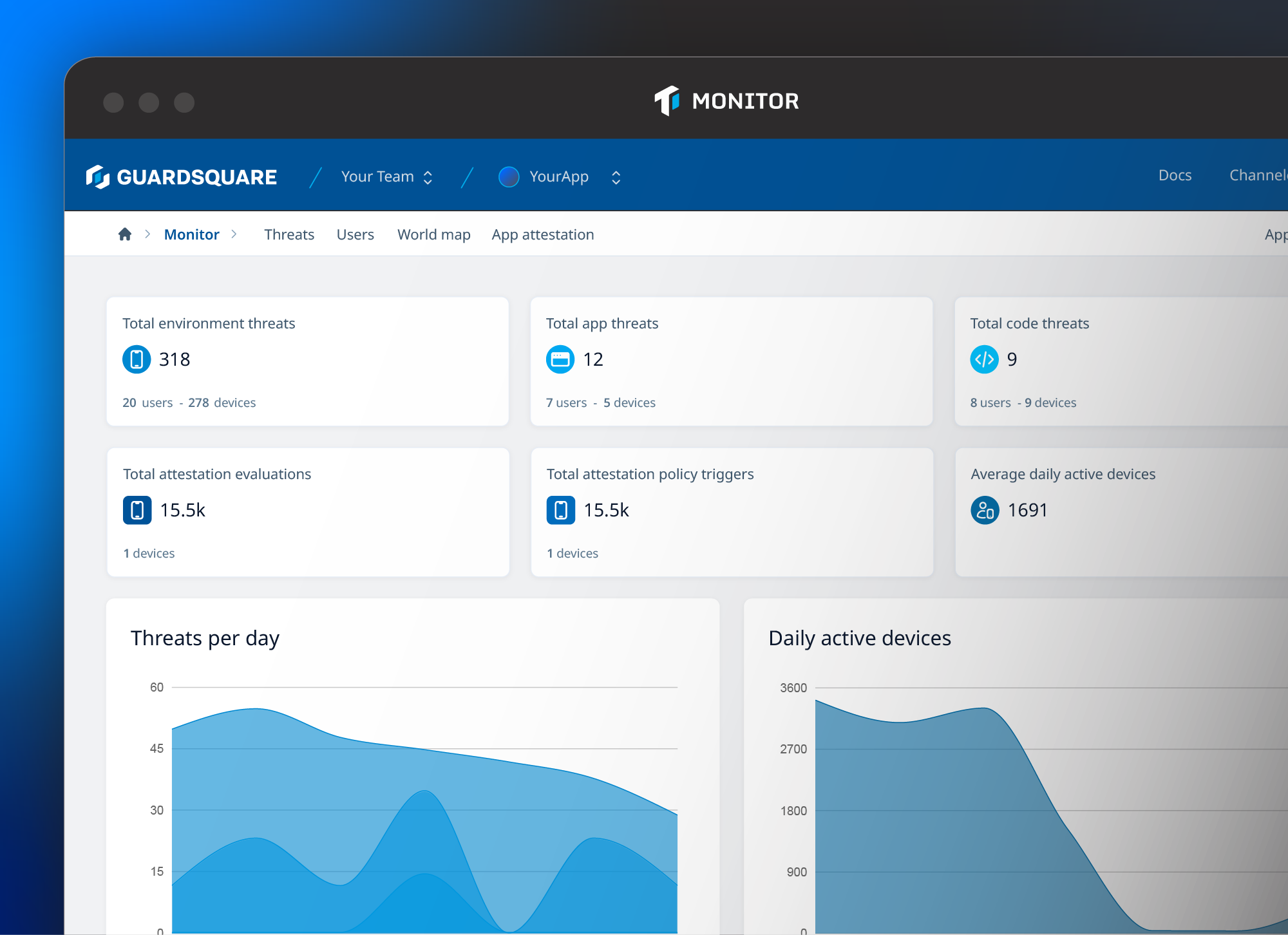
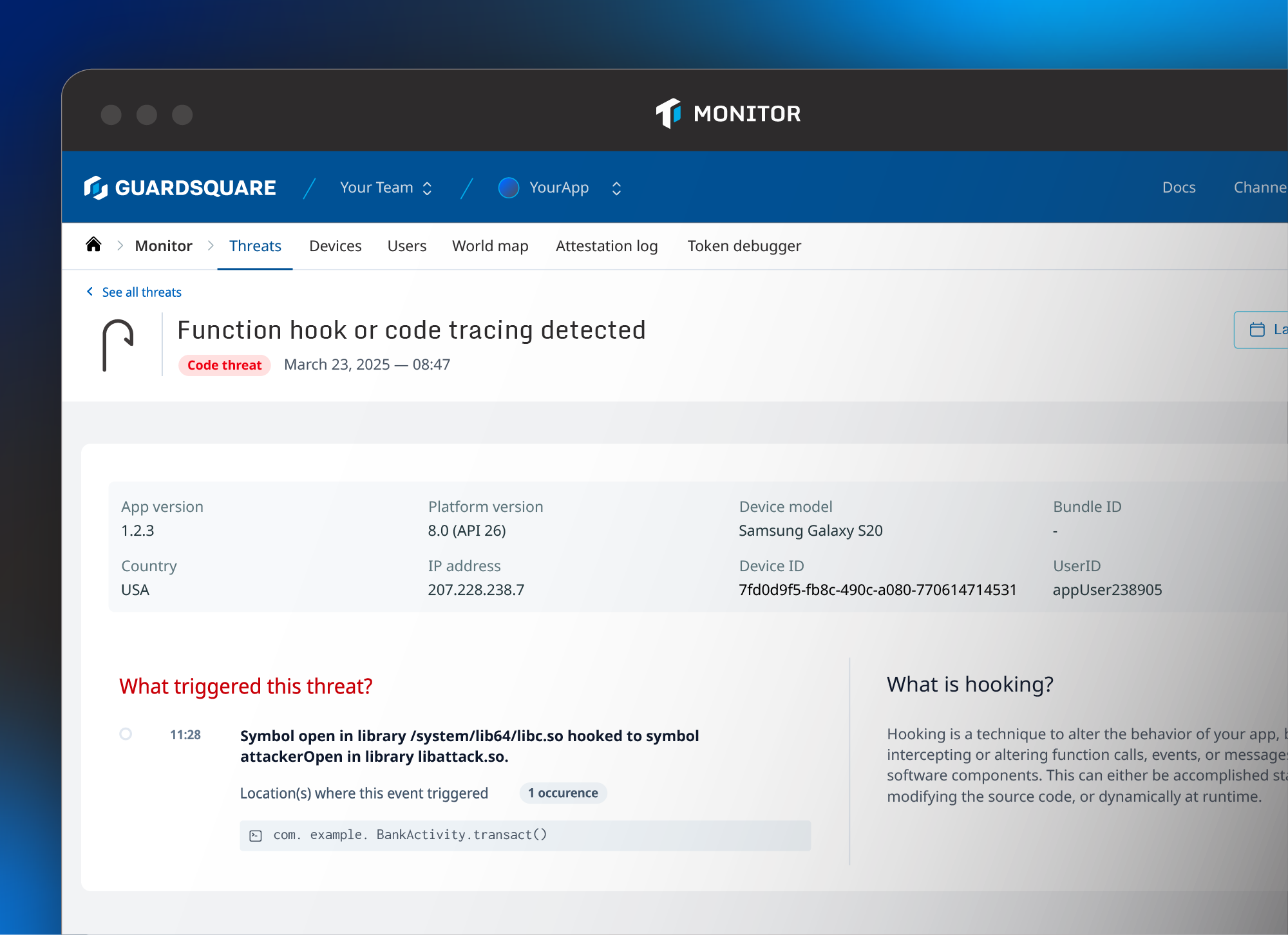
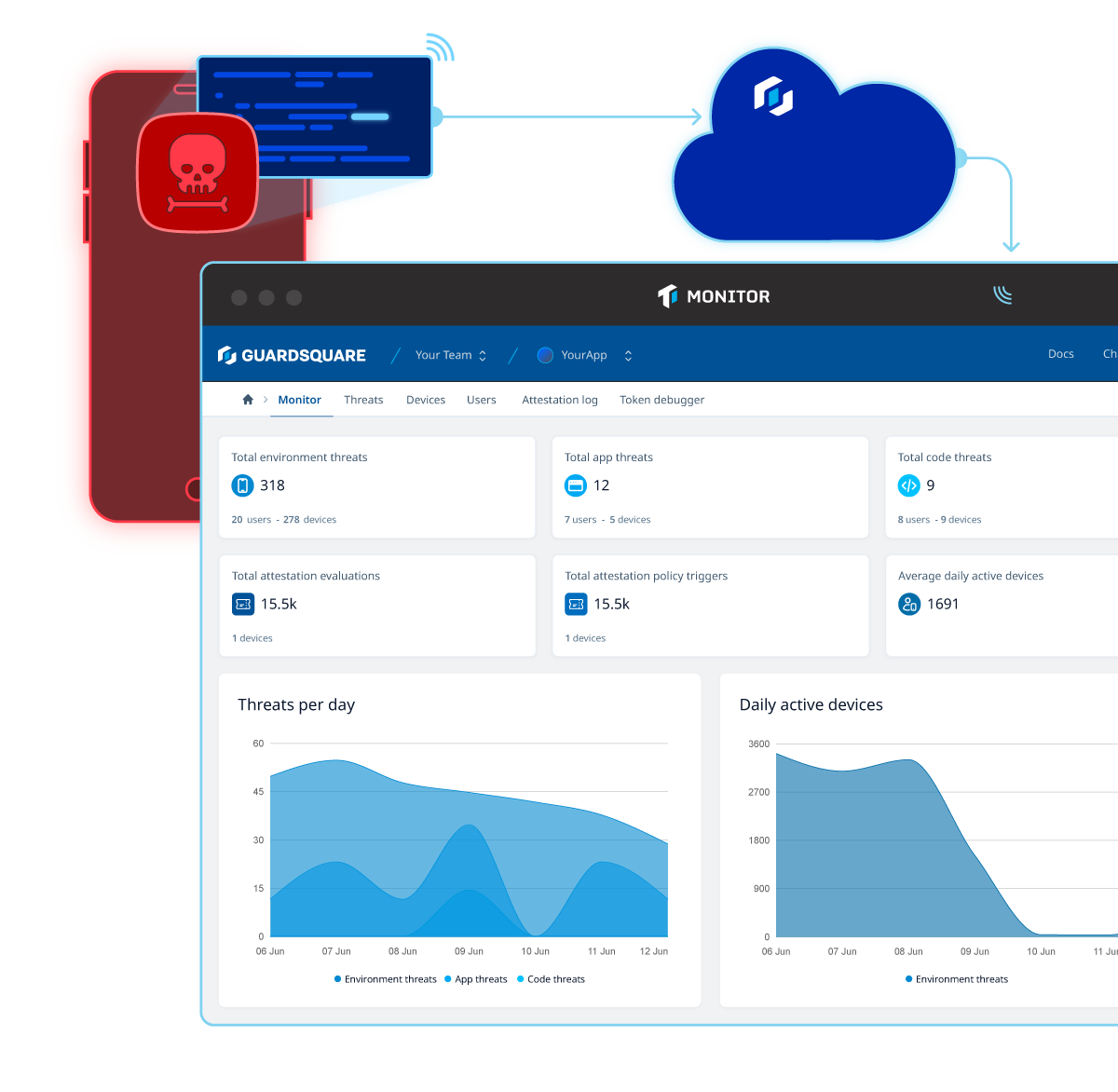
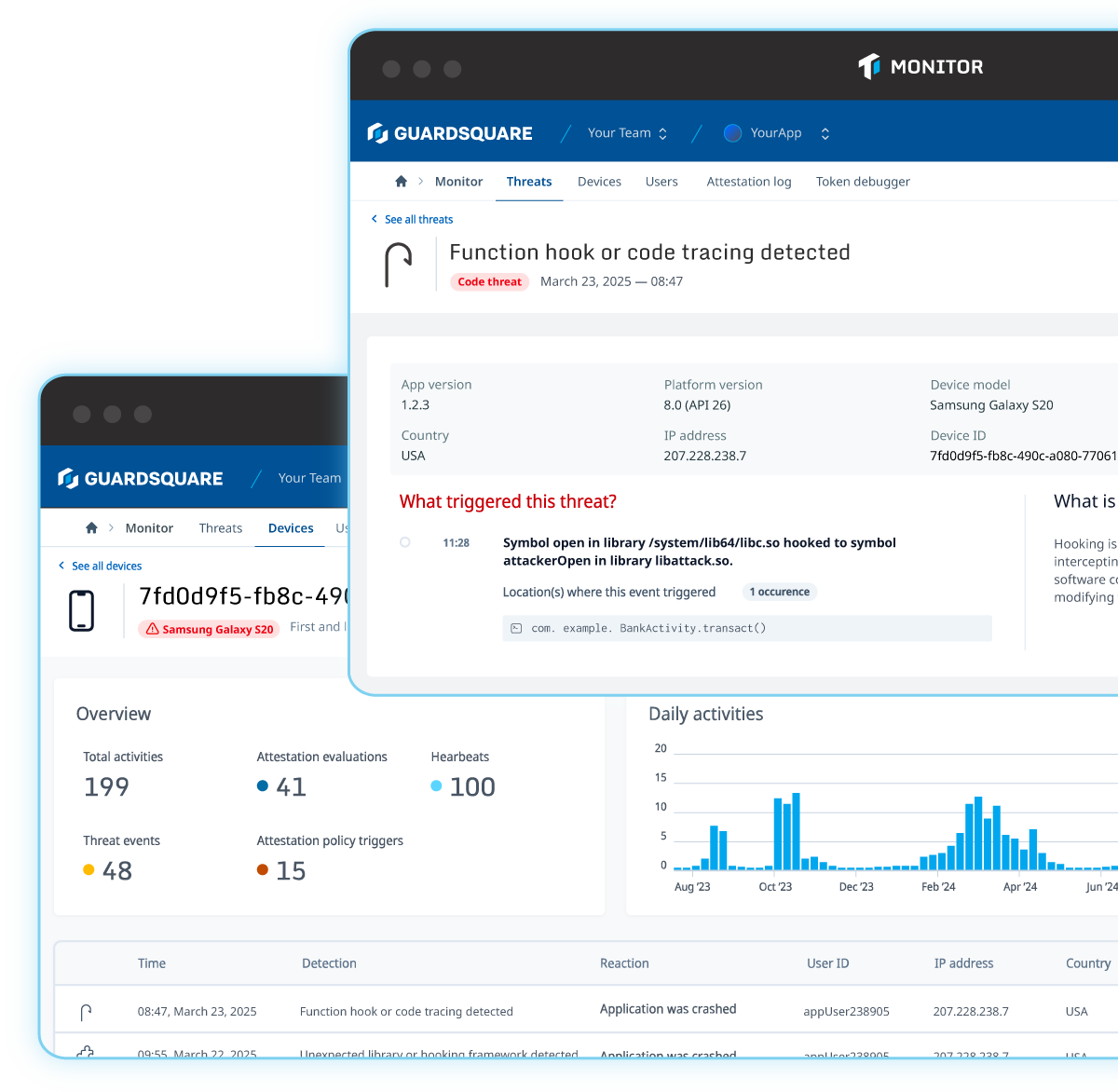
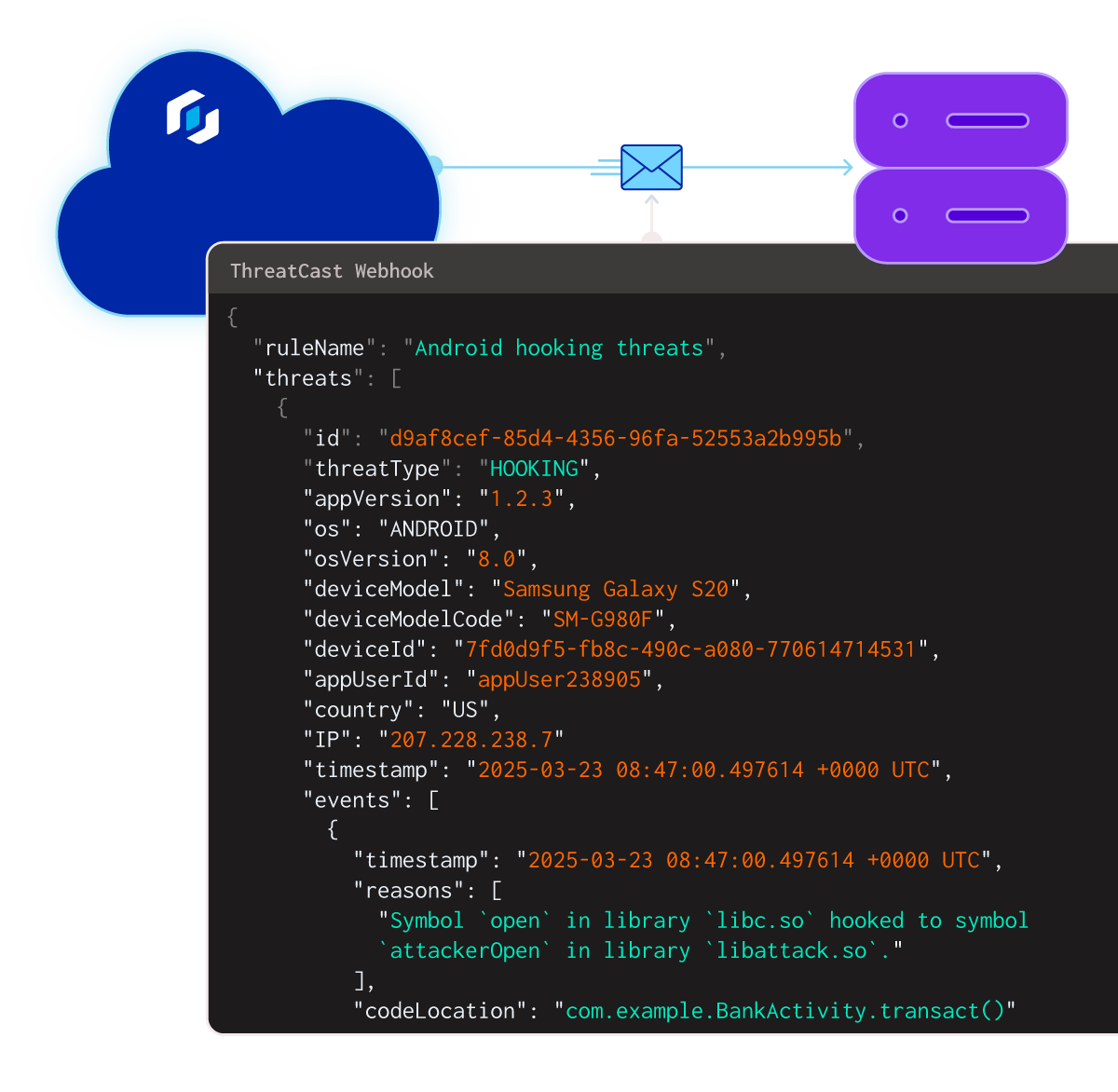
Threatcast is a mobile application threat monitoring solution that provides real-time visibility into threats from devices running your application so organizations can understand where reverse engineering efforts are coming from and the intended attack targets. By integrating custom webhooks, teams can consume insights by integrating them into a SIEM tool, or as part of a fraud or anti-cheat system.
-
Products
-
Solutions
-
Resources
-
Company
- Pricing