-
Products
-
Solutions
-
Resources
-
Company
- Pricing
Products
Solutions
Resources
Company
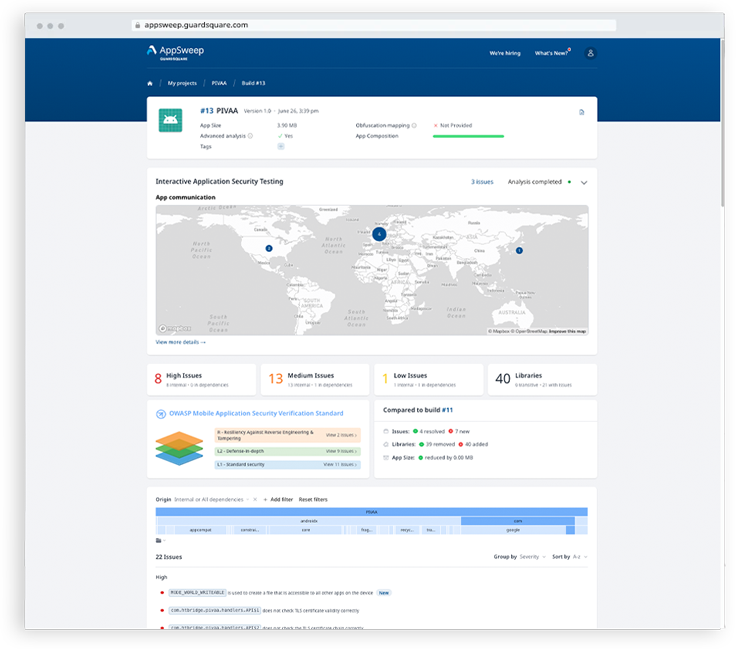
Globally, individuals spent more than 500 hours using mobile devices engaging with an average of 7 unique apps per day in 2024. In-app purchases increased 12.5% from 2023 reaching $150 billion.
With increased use, in addition to mobile apps processing and storing financial, medical and personal information, customers expect a high level of security and great UX to be delivered by the app.
To meet these expectations, developers cannot afford to wait and address security at the end of the software development lifecycle. Application security testing needs to be a priority throughout the development process.
Mobile Application Security Testing (MAST) covers the processes and tools used to identify potential security issues in mobile applications. Some tools also provide input to remediate identified issues to reduce risk. Mobile Application Security Testing can be performed manually or through the use of automated tools which use a variety of techniques.

Automated mobile application security testing typically uses software tools that employ one or more techniques to analyze the software to detect potential vulnerabilities. They are cost-effective and can be run easily and frequently by the development team to detect security issues so they can be remediated as quickly as possible. Automated tools have minimal impact on the software development life cycle (SDLC) and are easily integrated into the CI/CD process. Automated testing tends to have a broader coverage of the application code and the number of findings its tests for.

Penetration testing, or pentesting, is a combination of manual and software techniques typically executed by a 3rd party, at specific points in the SDLC, usually at the end. Pentesting may be used to meet regulatory requirements and is often focused with very specific goals. It can be expensive, time consuming, and tends to be run infrequently.

Crowd-sourced mobile app security testing, such as bug bounty programs, can also be used for mobile application security testing. These third-party programs can be used to supplement other security practices but should not replace them.

Automated mobile application security testing typically uses software tools that employ one or more techniques to analyze the software to detect potential vulnerabilities. They are cost-effective and can be run easily and frequently by the development team to detect security issues so they can be remediated as quickly as possible. Automated tools have minimal impact on the software development life cycle (SDLC) and are easily integrated into the CI/CD process. Automated testing tends to have a broader coverage of the application code and the number of findings its tests for.

Penetration testing, or pentesting, is a combination of manual and software techniques typically executed by a 3rd party, at specific points in the SDLC, usually at the end. Pentesting may be used to meet regulatory requirements and is often focused with very specific goals. It can be expensive, time consuming, and tends to be run infrequently.

Crowd-sourced mobile app security testing, such as bug bounty programs, can also be used for mobile application security testing. These third-party programs can be used to supplement other security practices but should not replace them.

Mobile application security testing can use different techniques, typically classified as static analysis, dynamic analysis, or interactive analysis. The techniques are not mutually exclusive and there can be overlap between them.
is a testing approach that analyzes the source code, the binary and other resources of the app for specific security issues. This is done by means of different analysis techniques that can analyze the app in an automated way, without executing the apps’ code.
is a testing approach that analyzes the application from the exterior while it is executed in an environment, for example a real phone or an emulator. This can be especially useful for identifying vulnerabilities that are only visible when the app is running, for example if the app communicates with a server.
is a form of Dynamic Analysis that tests the application while the app is run by an automated test, human tester, or any activity “interacting” with the application functionality. An application is instrumented, allowing more detailed assessment of the application during dynamic testing.

General-purpose app testing tools may already be in use by your organization, and part of the security process.
These tools tend to be optimized for web applications. Hence, they often lack the depth of analysis and tailored findings specific to mobile application threats. Mobile developers should evaluate their application security testing tool to ensure it has a strong focus on mobile application threats, including consideration of the OWASP Mobile Top 10 and the OWASP mobile security testing guide.

Open source tools can provide a good option for getting started with application security testing. When evaluating these tools, some important considerations include:
Can they be easily integrated into your development process; do they support cross team collaboration; how much effort is required to use them; how easy is it to understand their results; what is their rate of false positives; how complete is their coverage; are they updated to address new and evolving threats; what risk does their use pose to your project; and how well these tools are maintained by the community?

Mobile apps have unique risks. For example, a MATE (man-at-the-end) attack vector, where an attacker will load the application on their local device which gives them access to specialized tools, time, and resources to inspect and reverse engineer the application, giving them access to the hardware and mobile software.
These threats that are unique to mobile apps are often not covered by generic application security testing tools. Selecting a security testing tool that is specialized in mobile apps and built for mobile app developers can be critical in obtaining relevant, actionable findings.
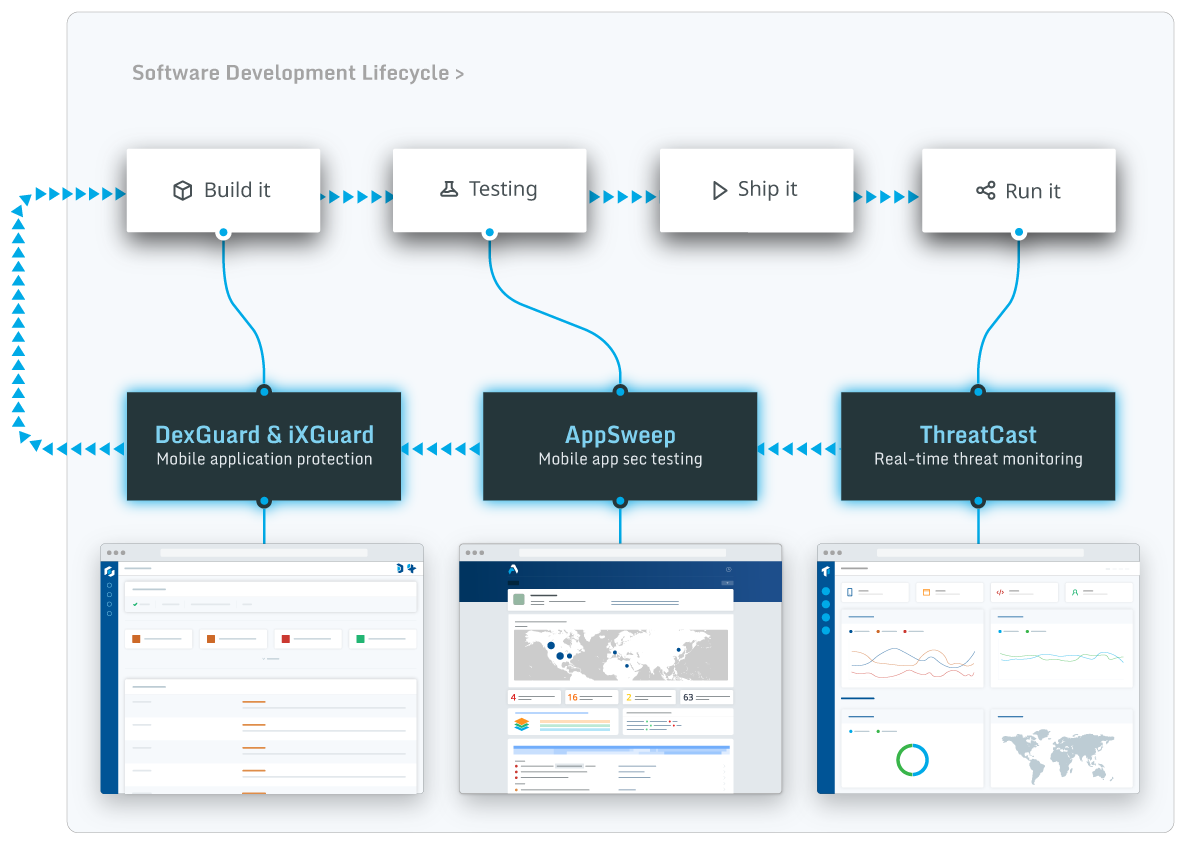
With development teams being consistently overcommitted and under-resourced, to truly improve the security controls around building mobile apps, organizations must ensure that automated mobile app security testing tools don’t add an additional workload and fit into their developers’ existing workflows. Tools should be fast, provide actionable results or recommendations, and integrate directly into the SDLC.
The key criteria is ensuring the analysis can be automated. This enables teams to consistently monitor the status of the code’s security profile and quickly see changes from one build to the next. Commits and releases that introduce new vulnerabilities can be quickly discovered, localized and remediated.

General-purpose app testing tools may already be in use by your organization, and part of the security process.
These tools tend to be optimized for web applications. Hence, they often lack the depth of analysis and tailored findings specific to mobile application threats. Mobile developers should evaluate their application security testing tool to ensure it has a strong focus on mobile application threats, including consideration of the OWASP Mobile Top 10 and the OWASP mobile security testing guide.

Open source tools can provide a good option for getting started with application security testing. When evaluating these tools, some important considerations include:
Can they be easily integrated into your development process; do they support cross team collaboration; how much effort is required to use them; how easy is it to understand their results; what is their rate of false positives; how complete is their coverage; are they updated to address new and evolving threats; what risk does their use pose to your project; and how well these tools are maintained by the community?

Mobile apps have unique risks. For example, a MATE (man-at-the-end) attack vector, where an attacker will load the application on their local device which gives them access to specialized tools, time, and resources to inspect and reverse engineer the application, giving them access to the hardware and mobile software.
These threats that are unique to mobile apps are often not covered by generic application security testing tools. Selecting a security testing tool that is specialized in mobile apps and built for mobile app developers can be critical in obtaining relevant, actionable findings.

With development teams being consistently overcommitted and under-resourced, to truly improve the security controls around building mobile apps, organizations must ensure that automated mobile app security testing tools don’t add an additional workload and fit into their developers’ existing workflows. Tools should be fast, provide actionable results or recommendations, and integrate directly into the SDLC.
The key criteria is ensuring the analysis can be automated. This enables teams to consistently monitor the status of the code’s security profile and quickly see changes from one build to the next. Commits and releases that introduce new vulnerabilities can be quickly discovered, localized and remediated.