-
Products
-
Solutions
-
Resources
-
Company
- Pricing
Products
Solutions
Resources
Company

RASP (runtime application self-protection) security enables iOS and Android mobile apps to monitor for suspicious behavior at runtime. When a runtime threat is detected, the RASP features help defend against threat actors attempting to tamper with your app or perform a dynamic analysis.

RASP solutions are security tools designed to protect applications at runtime by identifying and allowing you to take action against security threats and attacks. Unlike traditional security measures that focus on network or perimeter defense, RASP operates directly within the application itself.
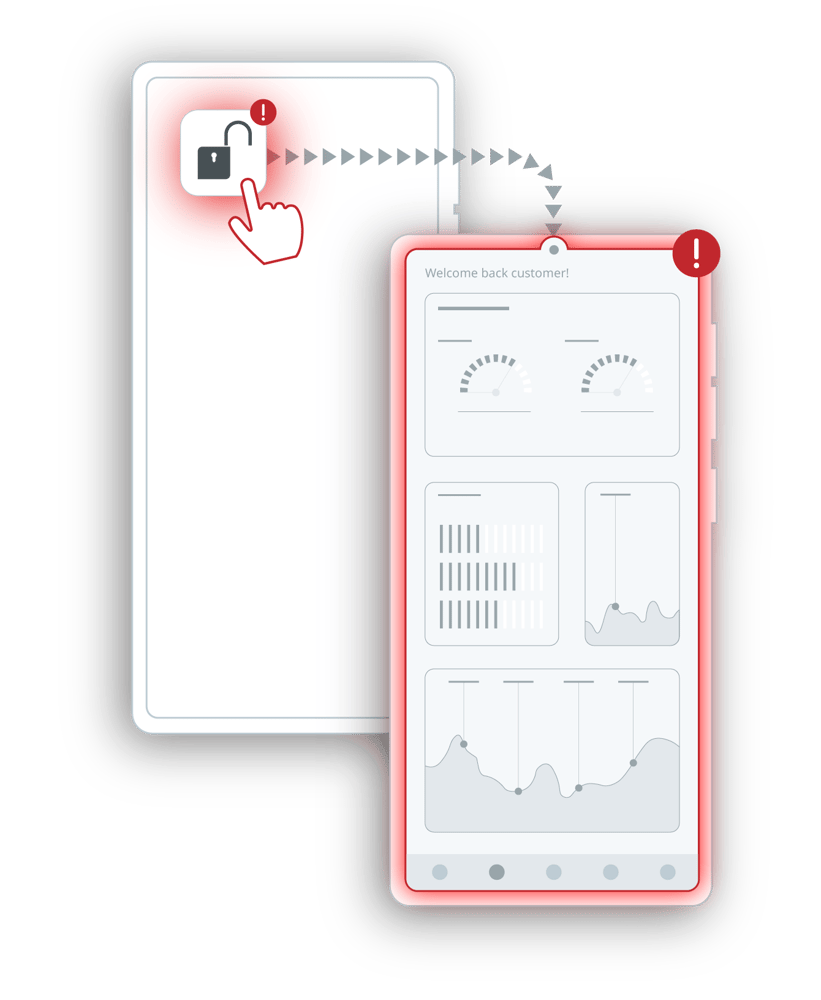
At runtime, threat actors can employ a variety of techniques to analyze and modify the app. Today, it is easier than ever before for a malicious user to deploy various techniques like jailbreaking, rooting, hooking, and more in order to steal decryption keys, intercept communication to servers, and more.
Threat actors tamper with mobile apps for a variety of ends, such as to unlock hidden or premium functions, repackage apps to steal confidential data or learn more about the application at runtime to support reverse engineering attempts. Protection against runtime attacks helps to prevent these outcomes, preserving your app’s integrity and your brand’s reputation.

iPhone Runtime Application Self Protection (RASP) is a crucial security measure that helps safeguard iOS applications against runtime threats, such as code injection, reverse engineering, and tampering. Unlike traditional security measures that focus on perimeter defenses, iOS runtime application self protection operates within the app itself, continuously monitoring and responding to suspicious activity in real-time.
In iOS app development, integrating iPhone runtime application self protection ensures that applications can detect and mitigate threats dynamically, preventing attackers from exploiting vulnerabilities while the app is running. Key techniques include jailbreak detection, runtime integrity checks, obfuscation, and real-time threat analytics. These measures help developers enhance app security, protect sensitive data, and comply with industry regulations, making RASP an essential component of modern iOS security strategies.

Android Runtime Application Self Protection (RASP) is a critical security mechanism designed to safeguard Android applications against real-time threats such as reverse engineering, tampering, and malware injection. Unlike traditional security approaches that rely on external defenses, RASP Android operates within the app, actively monitoring and responding to potential attacks during runtime.
In Android app development, implementing Android runtime protection helps ensure app integrity by leveraging techniques such as root detection, code obfuscation, runtime integrity checks, and behavioral analysis. These security measures prevent unauthorized modifications, data breaches, and other malicious activities, making RASP Android a vital component in building secure and resilient applications.
Research shows that despite developers' priorities, mobile apps still aren't secure enough.
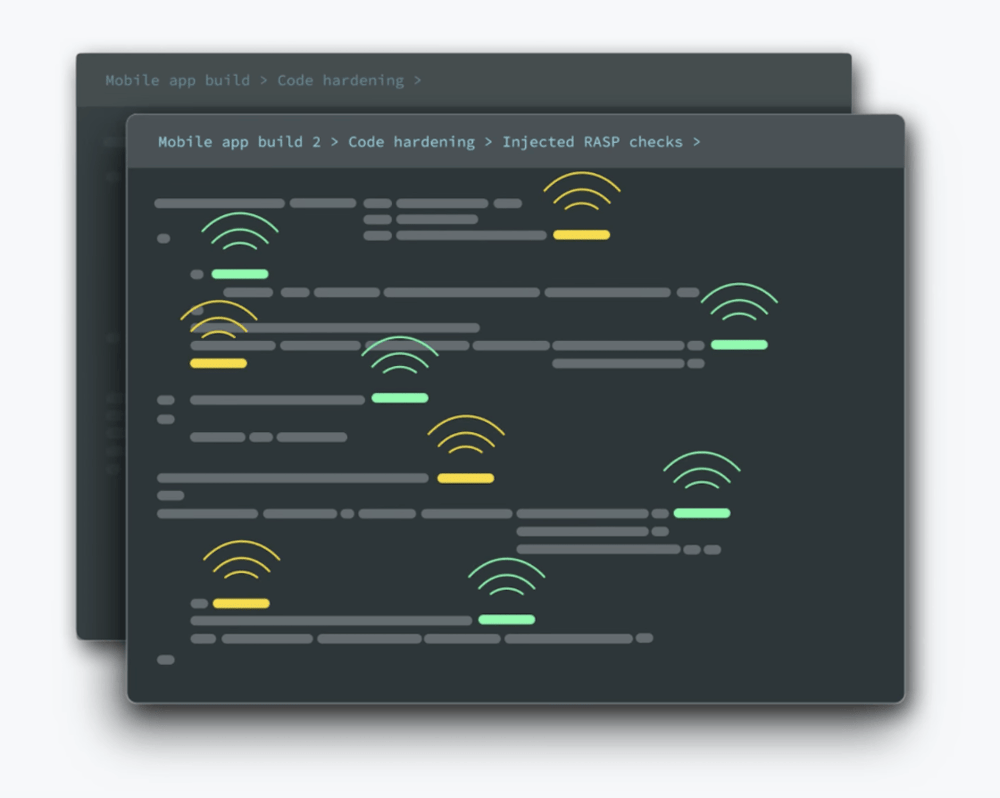
Runtime application self-protection implementations monitor both the app and the environment it runs within to detect threats like jailbroken or rooted devices, function hooking attempts and more. When these threats are detected, RASP mobile security implementations respond with pre-programmed actions, like terminating the user’s session, displaying a warning message or limiting functionality.
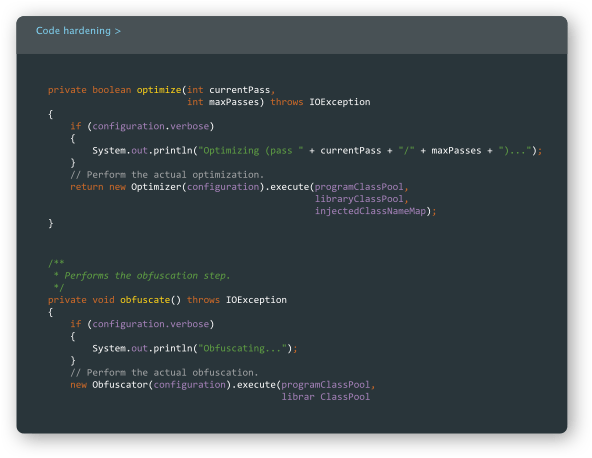
Guardsquare’s polymorphic approach ensures that every app’s build comes with a unique combination of check locations and exact checks, as every RASP integrity can be validated with a diverse palette of specific checks. And as an app developer you have full control over which parts of your app not to touch, or to touch more aggressively. For additional protection, code hardening is automatically applied to all inject locations.
Too often delayed to the end of the development lifecycle, security needs to be considered right from the start. As your app development progresses, testing, feedback and monitoring helps you to ensure the highest possible level of security.








Mobile app security is most effective when it’s considered from the outset of the development lifecycle, which includes making informed design choices, following best practices as well as early rounds of testing and refinement. Ultimately, engaging in secure software development practices identifies security risks early, when they’re quick and cheap to fix, rather than after deployment.
 Mobile app security is most effective when it’s considered from the outset of the development lifecycle, which includes making informed design choices, following best practices as well as early rounds of testing and refinement. Ultimately, engaging in secure software development practices identifies security risks early, when they’re quick and cheap to fix, rather than after deployment.
Mobile app security is most effective when it’s considered from the outset of the development lifecycle, which includes making informed design choices, following best practices as well as early rounds of testing and refinement. Ultimately, engaging in secure software development practices identifies security risks early, when they’re quick and cheap to fix, rather than after deployment.
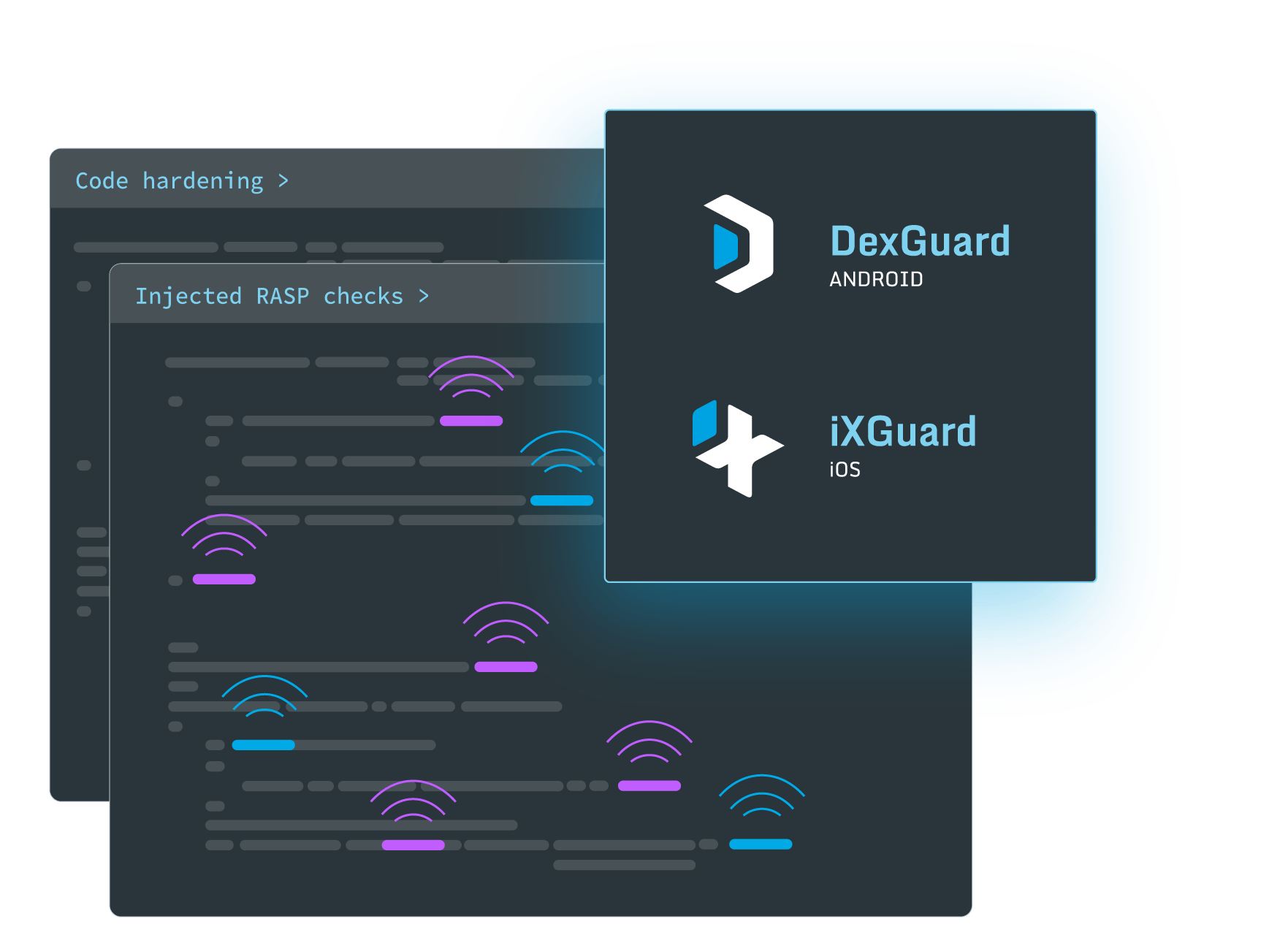
Now that your app is implemented, it’s crucial that you incorporate defenses against reverse engineers in order to protect your intellectual property, prevent counterfeits and secure your data and your brand’s reputation. App shielding techniques like code hardening and runtime application self-protection (RASP) ensure that your mobile app can’t be easily reverse-engineered or tampered with.
 Now that your app is implemented, it’s crucial that you incorporate defenses against reverse engineers in order to protect your intellectual property, prevent counterfeits and secure your data and your brand’s reputation. App shielding techniques like code hardening and runtime application self-protection (RASP) ensure that your mobile app can’t be easily reverse-engineered or tampered with.
Now that your app is implemented, it’s crucial that you incorporate defenses against reverse engineers in order to protect your intellectual property, prevent counterfeits and secure your data and your brand’s reputation. App shielding techniques like code hardening and runtime application self-protection (RASP) ensure that your mobile app can’t be easily reverse-engineered or tampered with.
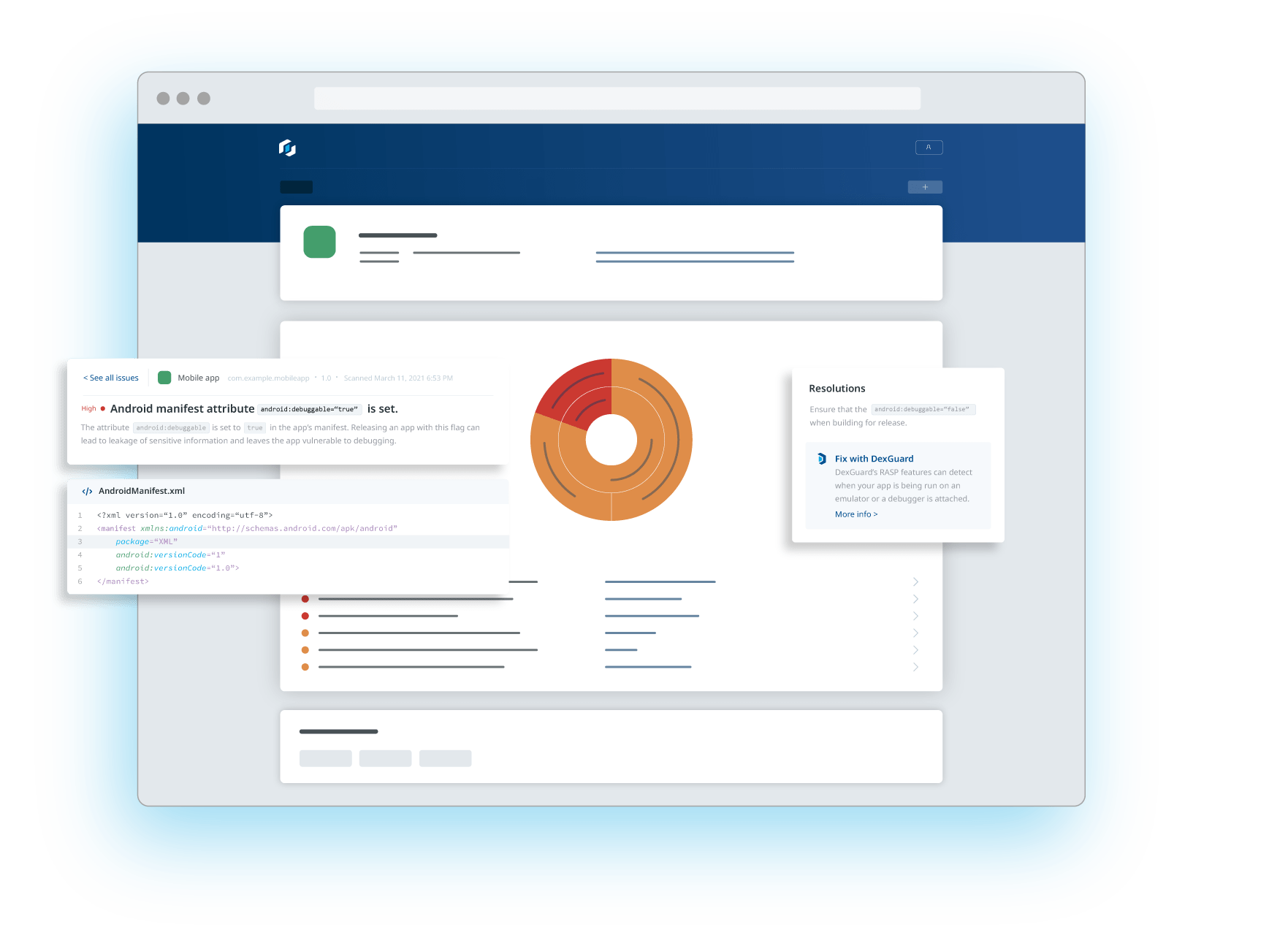
You wouldn’t release your app without testing its functionality; nor should you without testing its security. Pentesting, or penetration testing, is often performed by third-party experts to attempt to identify security gaps in your app and gain insight into its internal logic, just as a threat actor would. A complement to pentesting is AppSweep, Guardsquare's automated mobile application security testing (MAST) tool.
 You wouldn’t release your app without testing its functionality; nor should you without testing its security. Pentesting, or penetration testing, is often performed by third-party experts to attempt to identify security gaps in your app and gain insight into its internal logic, just as a threat actor would. A complement to pentesting is AppSweep, Guardsquare's automated mobile application security testing (MAST) tool.
You wouldn’t release your app without testing its functionality; nor should you without testing its security. Pentesting, or penetration testing, is often performed by third-party experts to attempt to identify security gaps in your app and gain insight into its internal logic, just as a threat actor would. A complement to pentesting is AppSweep, Guardsquare's automated mobile application security testing (MAST) tool.
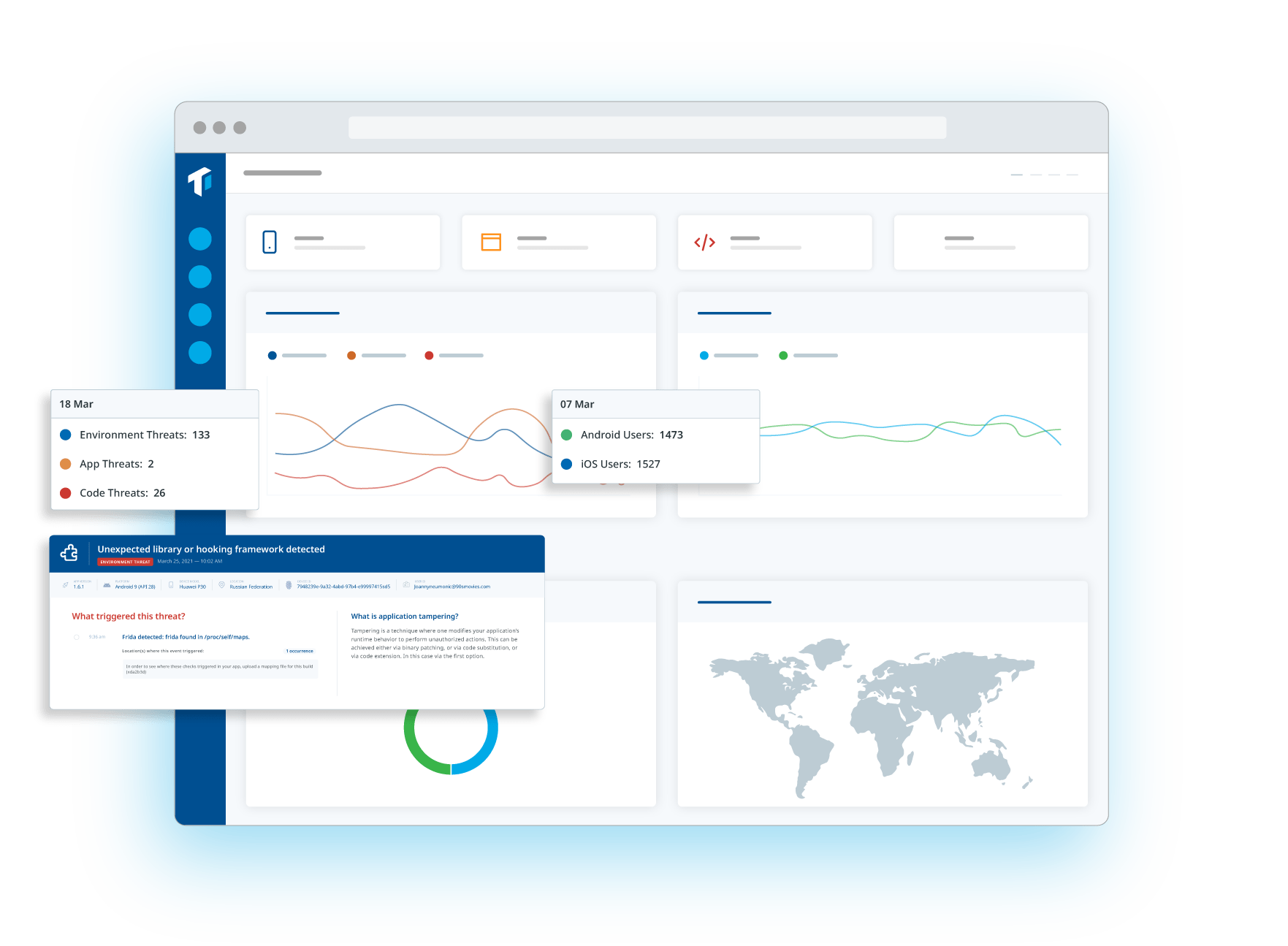
Now it’s time to monitor your apps usage after its release, and track related threats in real-time. What are threat actors’ preferred attack vectors? How can you evolve to improve your defenses? Real-time threat monitoring can provide the answers.
 Now it’s time to monitor your apps usage after its release, and track related threats in real-time. What are threat actors’ preferred attack vectors? How can you evolve to improve your defenses? Real-time threat monitoring can provide the answers.
Now it’s time to monitor your apps usage after its release, and track related threats in real-time. What are threat actors’ preferred attack vectors? How can you evolve to improve your defenses? Real-time threat monitoring can provide the answers.