-
Products
-
Solutions
-
Resources
-
Company
- Pricing
Products
Solutions
Resources
Company

Mobile app publishers adopt Flutter to lower development efforts, standardize Android/iOS UXs, and maintain native performance. But this comes with additional security risks.
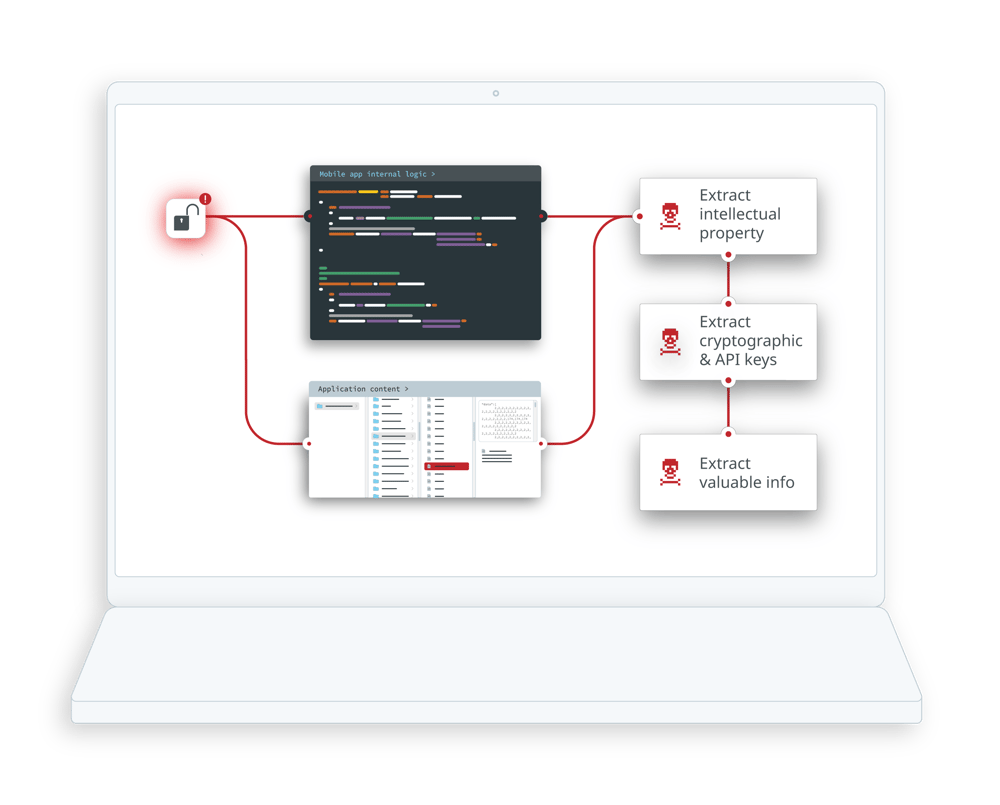
Despite the fact that Flutter mobile apps are compiled into native code, they still have similar attack surfaces, and the same inherent risks, as with other mobile technologies. Failure to implement app hardening measures, therefore, opens the door to intellectual property theft, credential harvesting, tampering and cloning.
A couple Flutter-specific risks include:
The Flutter engine - which takes care of GUI rendering, I/O, and more - is embedded in the same way with every published Flutter app. This opens the door for malicious actors to swap the Flutter engine out or modify it to target multiple apps with the same attack. In order to avoid this, you will need to protect your Flutter app from static analysis, and implement runtime detections which detect modifications or tampering.
Dart, being an emerging and dynamic programming language, exposes a lot of metadata. As a result, compiled Flutter apps leak a lot of information with their generated metadata; preventing the leaking of sensitive data requires additional app protection.
FLUTTER
“It’s hard to imagine how a couple lines could bring such huge confidence in securing national projects. The ease of use of Flutter protection overshadows the solid security features of DexGuard and iXGuard.”
Mobile Development Manager | Software company

The Flutter SDK offers an initial layer of protection by natively obfuscating the names of variables, classes and functions when a mobile app is released, but that is not enough to protect apps; for instance, basic Flutter obfuscation can’t protect against dynamic attacks, meaning your apps are still vulnerable to tampering when running in hostile environments.
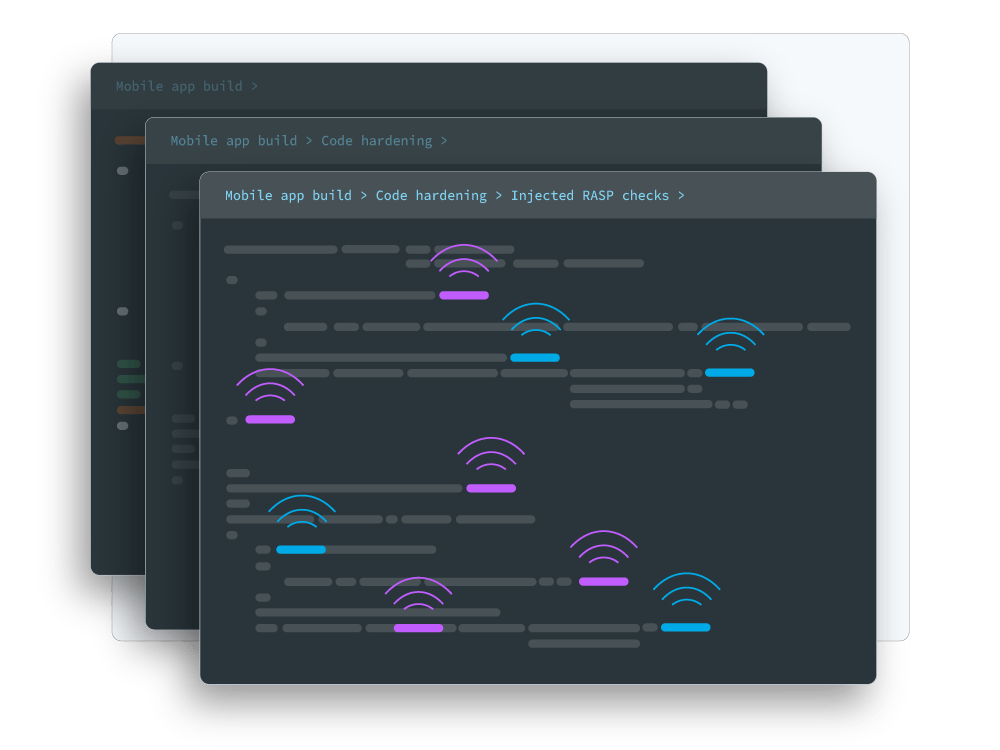
Guardsquare's security solutions incorporate the full spectrum of mobile app hardening, including:
Multiple layers of protection that reinforce one another and protect your app from reverse engineering and tampering.
Automatically injected RASP checks that are inserted into random locations in your code and at a higher volume than is possible with manual injection.
Applying these protections differently with each new build, which ensures that your mobile app security defenses reset the clock on attackers.
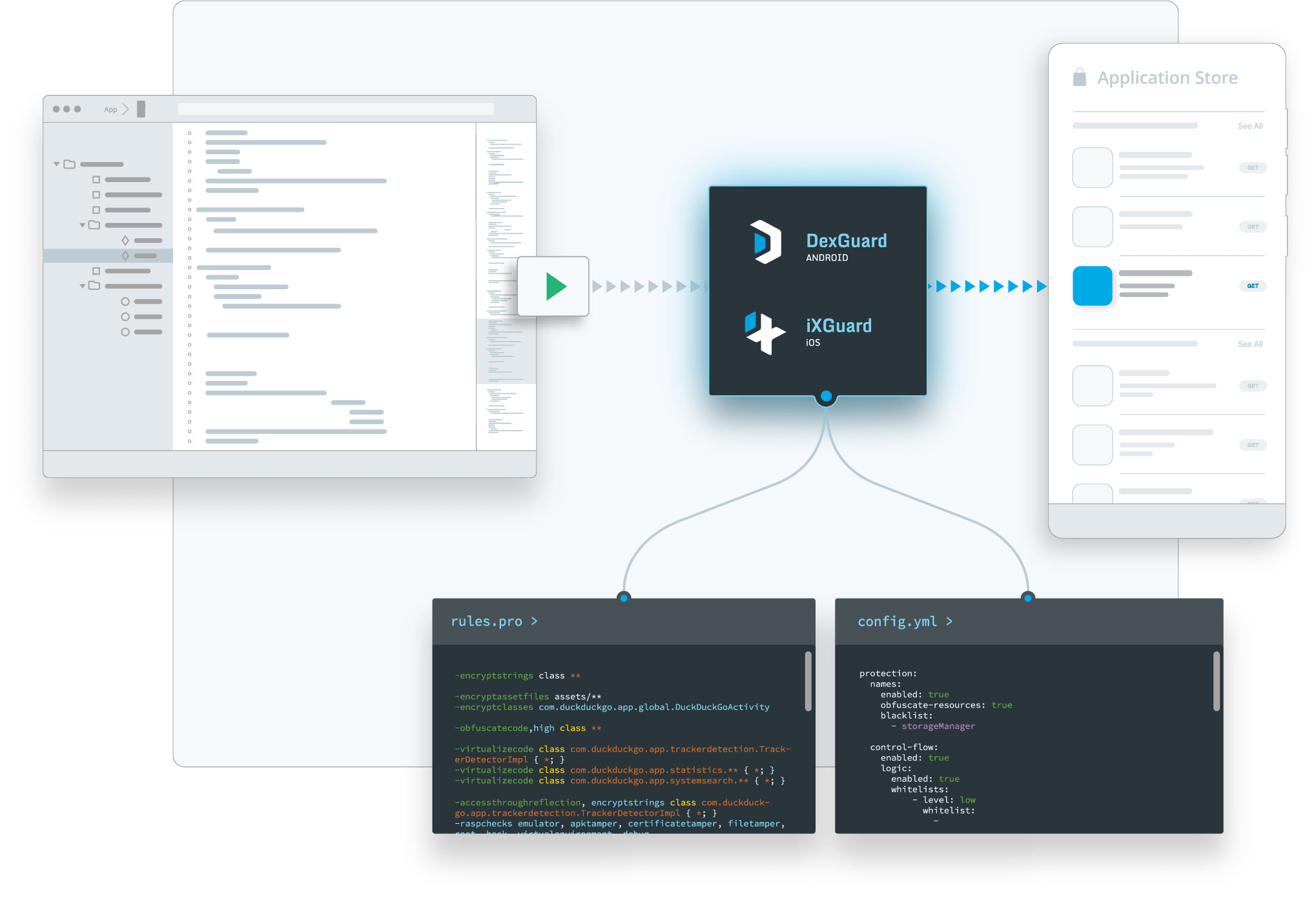
Tight development timelines and pressure to be first in the market can force mobile app publishers to cut corners when implementing security solutions. That’s why we developed our solutions to be as easy to integrate as possible:
No code changes are required in your app or SDK. Our hardening and runtime protections will be automatically applied during the build based on your selected configuration.
Our post-processing approach ensures Guardsquare’s solutions aren’t tightly coupled with other tools in the build chain.

The Flutter SDK offers an initial layer of protection by natively obfuscating the names of variables, classes and functions when a mobile app is released, but that is not enough to protect apps; for instance, basic Flutter obfuscation can’t protect against dynamic attacks, meaning your apps are still vulnerable to tampering when running in hostile environments.

Guardsquare's security solutions incorporate the full spectrum of mobile app hardening, including:
Multiple layers of protection that reinforce one another and protect your app from reverse engineering and tampering.
Automatically injected RASP checks that are inserted into random locations in your code and at a higher volume than is possible with manual injection.
Applying these protections differently with each new build, which ensures that your mobile app security defenses reset the clock on attackers.

Tight development timelines and pressure to be first in the market can force mobile app publishers to cut corners when implementing security solutions. That’s why we developed our solutions to be as easy to integrate as possible:
No code changes are required in your app or SDK. Our hardening and runtime protections will be automatically applied during the build based on your selected configuration.
Our post-processing approach ensures Guardsquare’s solutions aren’t tightly coupled with other tools in the build chain.