Enhance Mobile AppSec Resilience with 4 OWASP MASVS Recommendations
What MASVS is all about
MASVS, or the Mobile Application Security Verification Standard, is a framework created by OWASP, a global community of experts dedicated to improving the security of mobile applications. The standard assists developers in evaluating the security posture of iOS and Android applications and helps organizations identify and mitigate security risks.
Specifically, MASVS covers 7 security areas:
- MASVS-STORAGE aims to ensure the app securely stores sensitive data.
- MASVS-CRYPTO checks if the app employs strong cryptography and uses it according to industry best practices. Furthermore, this category checks that the app performs key management functions according to industry best practices.
- MASVS-AUTH ensures the app uses secure authentication and authorization protocols and follows the relevant best practices.
- MASVS-NETWORK requirements focus on ensuring the confidentiality and integrity of information exchanged between the mobile app and remote service endpoints.
- MASVS-PLATFORM lists requirements pertaining to the architecture and design of the app.
- MASVS-CODE aims to ensure basic security coding practices are followed in developing the app, such as appropriate app signing, removal of debugging symbols, and other measures.
- MASVS-RESILIENCE requirements are intended to help evaluate the level of mobile app protection against reverse engineering and tampering.
In this blog, we focus on the MASVS-RESILIENCE category by describing four strategies to enhance the resilience of your mobile apps against reverse engineering and tampering. These threats are particularly relevant for apps that handle or provide access to sensitive data or functionality, such as financial or medical apps. Threat actors aim to attack these types of mobile apps to steal money, intellectual property, or to harvest credential data that can be used in more targeted attacks.
4 ways to comply with MASV-RESILIENCE requirements
1. Runtime Application Self-Protection (RASP)
RASP involves integrating security checks directly into the application so it can detect and respond to potential attacks when the app is running. This can include monitoring for suspicious behavior, such as an attempt to repackage the app and violating code integrity by injecting malicious code or running the app in a compromised environment such as a rooted or jailbroken phone. When a threat is detected, RASP checks take proper measures to mitigate it such as crashing the app or reporting the attempt to a threat monitoring system for logging purposes.
2. Polymorphism
Polymorphism refers to the practice of changing the implementation of the resilience techniques used in the application on a regular basis. By doing this, mobile app developers make it more difficult for attackers to implement a successful attack as they must constantly adapt to the changing security measures. For instance, attackers may try to reverse engineer the code of a mobile app to understand how it works and exploit vulnerabilities. With polymorphism, developers make it significantly more challenging and time consuming for attackers to reverse engineer the app's code by frequently changing the implementation of the security measures in place. This could include changing the order in which security controls are applied, the location where the security controls are placed in the app, or the parameters used in an encryption algorithm.
3. Unpredictability
Unpredictability is a crucial aspect of mobile app security that involves making it difficult for attackers to anticipate and bypass the security measures in place. By making the implementation of resilience techniques random, the app developers can throw off the attackers and increase the app's overall security. For example, if an attacker knows the exact order in which the security controls are applied, they can more easily develop an attack that targets the vulnerabilities in the app and automate it to make the attack larger in scale. However, if the order is changed regularly, the attacker will have a much harder time identifying and exploiting vulnerabilities. Similarly, if the location of security controls is changed or rotated periodically, the attacker will have a much harder time locating and bypassing them.
4. Multi-layered protection
Using multiple layers of security controls is an effective strategy for mobile app security because it adds several different hurdles for attackers to overcome. This means that even if one security control is breached, other controls remain in place to protect the app. This multi-layered approach can include multiple code-hardening techniques like name obfuscation, control flow obfuscation, and mathematical obfuscation. Name obfuscation is when variable and function names are changed to obscure their meaning, making it harder for an attacker to understand the code. Control flow obfuscation makes the control flow of the code more difficult to follow, again making it harder for an attacker to understand the app's functionality. Mathematical obfuscation involves using mathematical operations to hide data, making it harder for an attacker to extract information from the app's memory.
Check your mobile app compliance with OWASP MASVS-RESILIENCE and fix security gaps
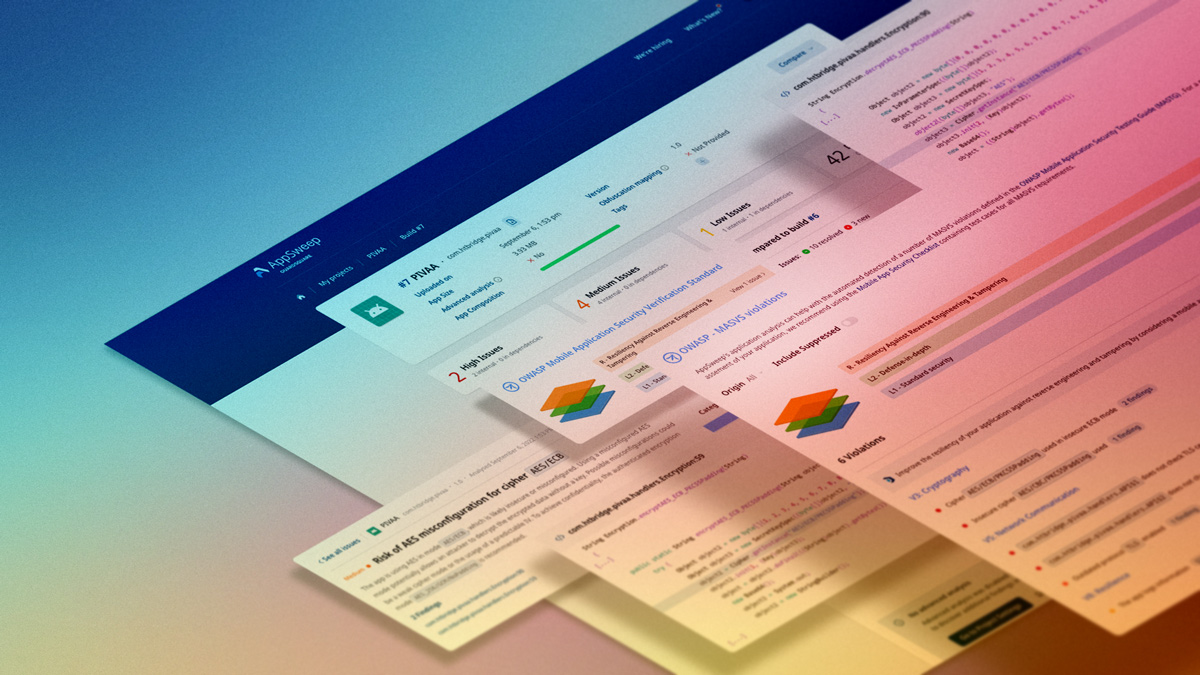
AppSweep, Guardsquare’s free mobile application security testing tool, helps developers check the overall security posture of their app. Specifically, it allows developers to continuously scan their app’s code and dependencies during the development process to quickly find security issues. Furthermore, it provides actionable recommendations to address the identified issues before they are exploited in the wild. AppSweep verifies apps against the requirements of MASVS v.2.0 by grouping the findings according to 3 OWASP security profiles, namely L1 - standard security, L2 - Defense-in-depth and R - Resiliency Against Reverse Engineering & Tampering.
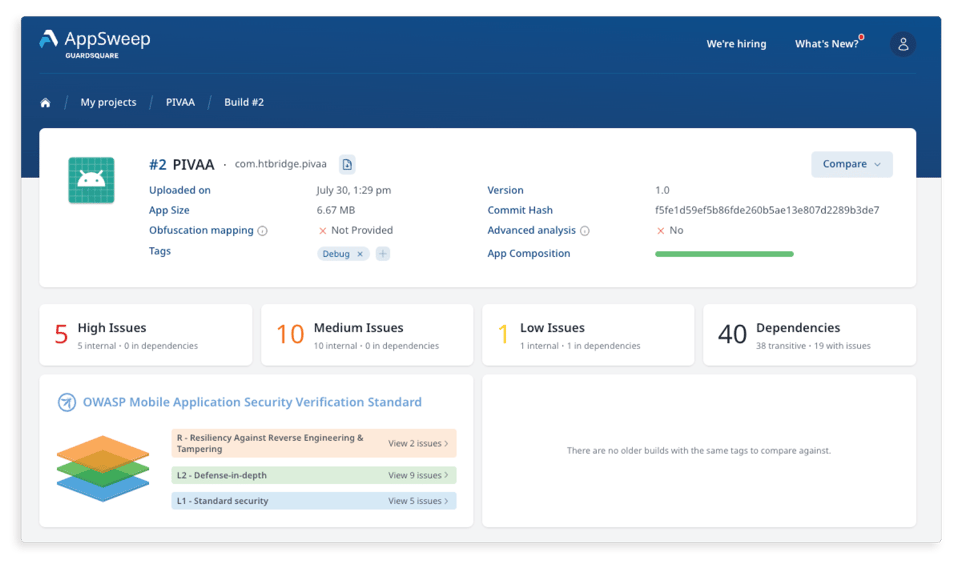
When developers work with apps that require high resilience against reverse engineering and tampering, such as banking, medical, E-commerce and retail apps that handle financial and personal data, AppSweep allows them to highlight specific findings that violate the OWASP MASVS-RESILIENCE controls by selecting the 'R' layer in the user interface.
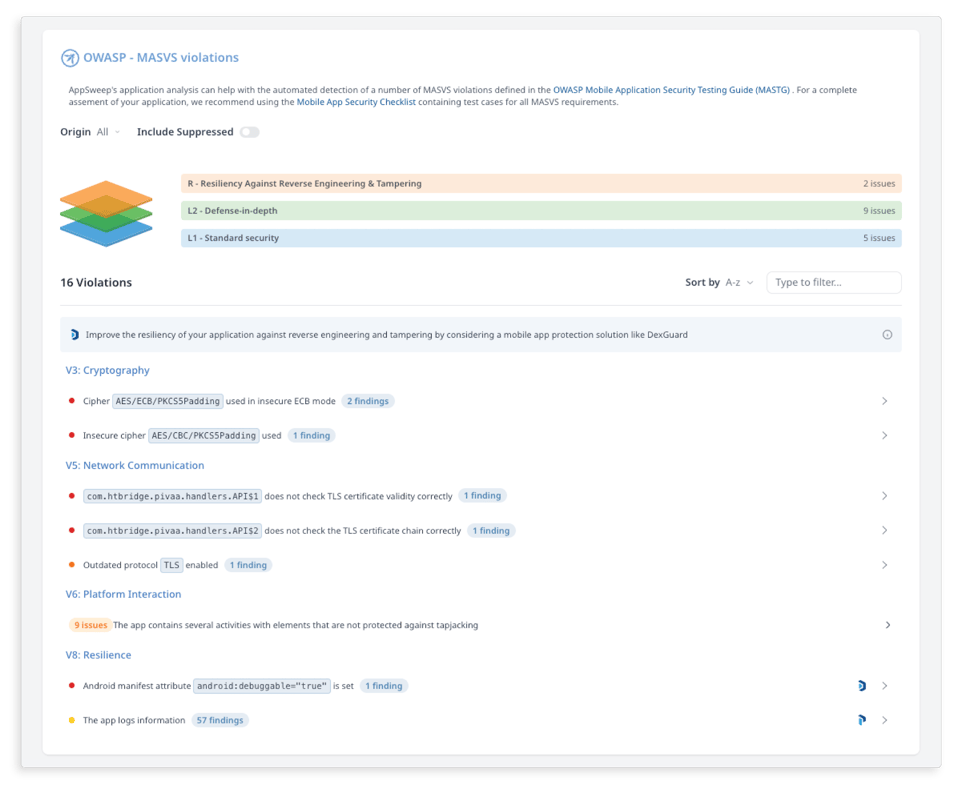
If AppSweep identifies OWASP MASVS-RESILIENCE security issues, it also provides actionable recommendations on how to fix them. For example, developers can use Guardsquare's android app protection tool, DexGuard, to automatically implement the four OWASP strategies mentioned earlier, which include code hardening and real-time protection against tampering. DexGuard also adds security layers and makes apps more resilient to threats by changing security check configuration with each release. This effectively resets the clock for a threat actor who needs to restart the attack.




