This blog explores:
- mHealth app usage is on the rise, but the rise in market profitability is shadowed by a concurrent rise in new and evolving security threats.
- Many mHealth app developers lack the experience and expertise to properly ensure mHealth app security, but the FDA’s STRIDE framework is a good place to start.
- Guardsquare’s products: AppSweep, DexGuard, iXGuard, and ThreatCast, can help developers build the strong security posture their mHealth apps need.
In our piece on mHealth apps and FDA approval, we defined mHealth apps as, “mobile technology that allows the user to monitor and share health information, including apps that allow physicians to diagnose and deliver care.” Determining whether or not an mHealth app requires FDA approval can be tricky. If you’re in doubt about your app’s need for FDA approval, make sure to visit our FDA approval post for a full breakdown on FDA approval criteria and a checklist to help you decide if this is necessary for your app.
Are mHealth applications secure?
In defining mHealth apps, we also touched briefly on the exponential growth of this market and found that the updated figures are even more impressive. In a recent study published by Global Industry Analysts, Inc., the organization estimated that the global market for mHealth apps will reach $16.6B by the end of 2026.
However, while mHealth apps are rising in popularity and profitability, we’re also seeing a concurrent rise in healthcare attacks. Thanks to the surge of cyberattacks in 2021, the cost of a typical healthcare security incident has risen 30% to $9.4 million in 2021 compared to the previous year. These incidents impacted more than 1.3 million people in the US alone, with more expected to take place in 2022.
Current state of mHealth app security
As more healthcare organizations and other businesses develop apps, there needs to be a synchronous focus on mHealth application protection. In 2021, researchers analyzed 20,000 mHealth apps in the Google Play store. They found that 45% of the apps relied on unencrypted communication, 23.0% sent personal data on unsecured traffic, and 1.8% contained suspicious code. These findings indicate significant security deficiencies in mHealth apps. Without stronger mobile app security for healthcare, organizations risk irreparable damage to their reputation, revenue, and most importantly, patients’ well-being.
Are mHealth apps secure?
The security of mHealth apps can vary widely depending on a developers' practices, the implementation of security measures, and adherence to relevant regulations. While many mHealth apps prioritize security to protect sensitive health information, there are also potential risks and challenges.
By incorporating security practices such as encryption, authentication, and secure APIs into the development lifecycle, developers can create mHealth apps that prioritize the confidentiality, integrity, and availability of health information. Additionally, ongoing monitoring and continuous improvement are crucial to adapting to emerging security threats and maintaining a high level of security over time.
The biggest barriers to mHealth app security development
A thorough understanding of the biggest risks affecting security in mHealth apps is crucial when developing a strategy to protect against both emerging and evolving threats.
In 2021 researchers reviewed data from studies published between 2008-2020 to isolate the main challenges developers face when securing mHealth apps. The results were surprising. 63% developers demonstrated a lack of knowledge and expertise needed for secure app development, and 19% paid little to no attention to security during the mHealth app development process. This study indicates that there is an urgent need for organizations to start prioritizing protection for mHealth applications.
So, where do we start? Let’s start by looking at what the FDA has to say about security risks most pressing to mHealth apps. Even if your mHealth app doesn’t require FDA approval, the regulatory body offers a solid strategy for addressing the most prevalent security risks threatening this particular type of app.
Security Risks for mHealth Apps
Some of the top security risks for mHealth apps include weak authentication and authorization processes, storing health data on mobile devices without proper encryption, insecure coding practices, and users who unintentionally compromise security through poor privacy decisions.
To address these security risks, mHealth app developers must adopt a comprehensive approach that includes regular security assessments, adherence to best practices, and ongoing monitoring for emerging threats. Proper protection for mHealth applications must include:
- Strong user authentication methods (e.g., biometrics, multi-factor authentication) and ensure that users have appropriate access levels based on their roles
- Secure storage mechanisms, such as encrypted databases, and avoid storing sensitive data on the device unless necessary
- Dependable encryption methods for data at rest and in transit
- Adherence to data protection regulations such as HIPAA (Health Insurance Portability and Accountability Act) or GDPR
Utilizing application security software is also an essential component of a robust security strategy for mHealth applications.
When it comes to the most common types of security risks mHealth app developers should protect against, the FDA segments threats based on a threat modeling framework called STRIDE. STRIDE stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privileges.
The FDA also offers a helpful playbook for threat modeling in medical devices, which contains a table that provides a description and example of each threat represented in the STRIDE acronym.
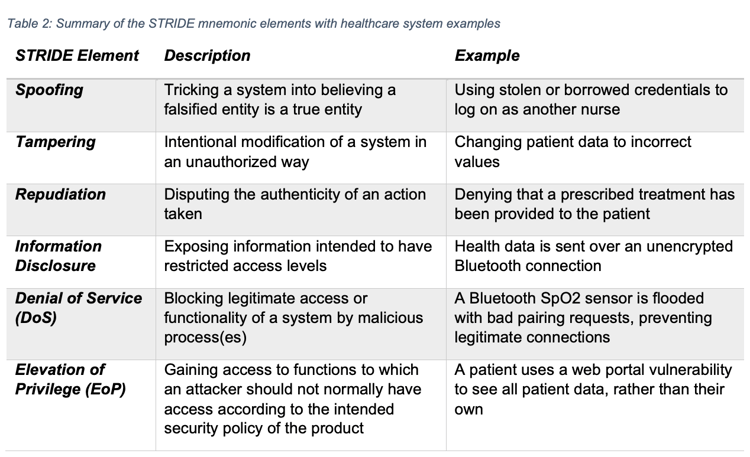 Image Credit: Playbook for Threat Modeling Medical Devices
Image Credit: Playbook for Threat Modeling Medical Devices
In addition to this playbook, the FDA also shares guidance on how to mitigate cybersecurity risks to stay in compliance with their regulations. Some of the more high-level guidance from these assets include:
- Remain vigilant about identifying risks and hazards associated with medical devices, including risks related to cybersecurity.
- Evaluate network security and protect your systems.
- Put appropriate mitigations in place to address patient safety risks and ensure proper device performance.
Although this guidance is helpful, you’ll need the right tools and support to ensure you are fully equipped to act on this advice.
How Guardsquare can help with security in mHealth applications
AppSweep
Leveraging a mobile app security testing platform like AppSweep, helps mobile app developers improve their mHealth app’s security posture. This free, developer-centric tool enables them to gain actionable insights into their app code’s security risks and dependencies. Moreover, AppSweep has built-in support that provides coverage for the OWASP MSTG (Mobile Security Testing Guide) security requirements. The platform’s results can be filtered, which makes it easier to identify how the findings relate to the OWASP MASVS (Mobile Application Security Verification Standard) categories. Finally, AppSweep can also be easily integrated into popular CI/CD tools such as Bitrise, Github, and Jenkins.
DexGuard and iXGuard
Similarly, mobile application protection solutions, DexGuard and iXGuard, help mobile app developers to mitigate the risks represented in the STRIDE framework. These solutions provide the most comprehensive, full-spectrum mobile app protection available with extensive code hardening techniques such as code virtualization, call hiding, and code obfuscation for classes, fields, arithmetic instructions, and more. Each of these work together to protect against static analysis. Additionally, these solutions automatically inject runtime application self-protection (RASP) checks, preventing threat actors from tampering with apps at runtime. RASP injects checks like jailbreak detection, debugger detection, repackaging detection, code tracing detection, hook detection, and more.
Both DexGuard and iXGuard are equipped with polymorphic protection — a mechanism that permits each app build to have different code hardening and RASP configurations. Additionally, the RASP checks are applied in different locations, ensuring threat actors can’t reuse their prior knowledge.
ThreatCast
When it comes to real-time visibility into your iOS and Android apps, Guardsquare’s ThreatCast enables developers to view attacks and suspicious activity as they occur once the app is released. You can set custom alerts and actions to become aware of threat events as they occur and to respond to them before a breach occurs. This continuous monitoring and evaluation allows you to remain vigilant and evolve your security posture to minimize the risks and hazards that might be associated with your mHealth apps.
To learn more about how Guardsquare can help you identify and protect against the most common mHealth app risks, connect with one of our experts now!






