Supporting the Refactored OWASP Mobile Application Security Verification Standard (MASVS)

In July 2021, members of the OWASP foundation announced a plan to refactor and update the OWASP Mobile Application Security Verification Standard (Big MASVS Refactoring). There were a number of driving factors, primarily around challenges related to controls and removing redundancies. We couldn’t agree more.
OWASP & Guardsquare, alignment in philosophy
In August 2021, we launched AppSweep, a free, developer-oriented mobile application security testing tool. Our philosophy on findings in AppSweep is to ensure they are relevant, actionable, and presented with clear recommendations on how to fix them.
Our philosophy aligns with some of the stated goals of the MASVS v2 refactoring effort, in particular, the concept of ensuring actionability.
“Make controls more specific so that they can be linked to very concrete and actionable MSTG test cases.”
Announcing Built-In Support for OWASP MASVS Control Groups
We recently made some updates to AppSweep to add support for additional findings that provide coverage for the OWASP MSTG (Mobile Security Testing Guide) security requirements. We also added a new filterable view of findings to make it easier for users to identify how the findings we report relate to the OWASP MASVS Control Groups.
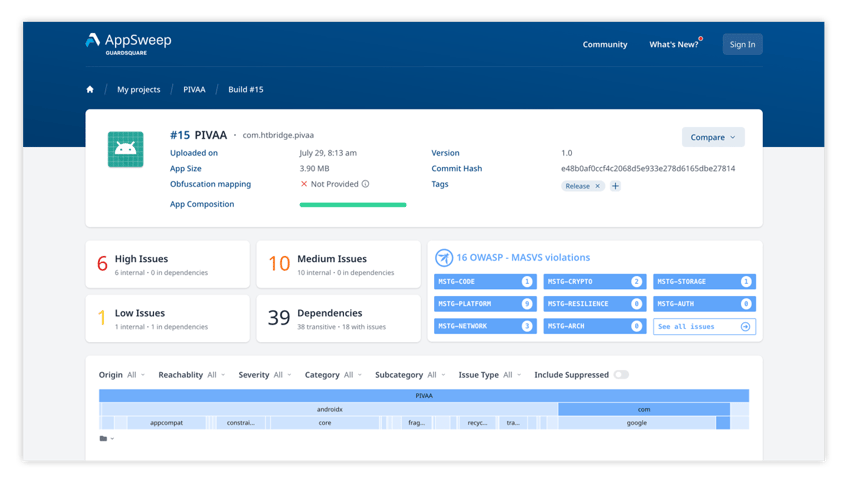
All eight of the MASVS Control Groups are represented within AppSweep, and you can easily drill down to see the relevant findings within each Control Group. These include:
- MASVS-STORAGE: Secure storage of sensitive data on a device (data-at-rest)
- MASVS-CRYPTO: Cryptographic functionality used to protect sensitive data.
- MASVS-AUTH: Authentication and authorization mechanisms used by the mobile app.
- MASVS-NETWORK: Secure network communication between the mobile app and remote endpoints (data-in-transit).
- MASVS-PLATFORM: Secure interaction with the underlying mobile platform and other installed apps.
- MASVS-CODE: Security best practices for data processing and keeping the app up-to-date.
- MASVS-RESILIENCE: Resilience to reverse engineering and tampering attempts.
To ensure AppSweep meets your needs, we implemented explicit tests that cover many of the OWASP MSTG security requirements. This also provides you with greater insight into what findings you can expect to see. There are several examples that can be seen in our PIVAA demo app.
We will continue to update AppSweep as the MASVS refactoring goes on, so you can be sure it’s up to date with the latest efforts of OWASP.
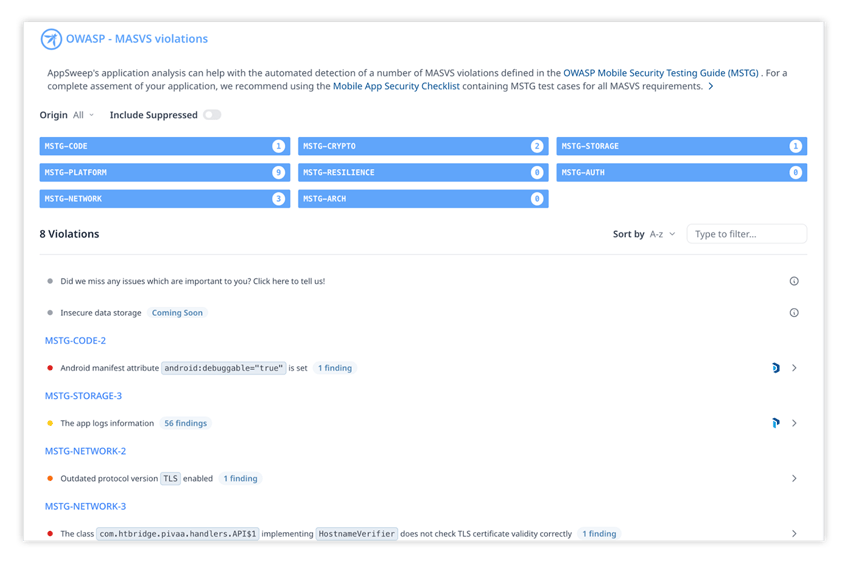
Automate your OWASP Mobile App Testing
When implementing the OWASP MSTG testing requirements, you can choose between in-house testing or using a third party. Additionally, testing can be performed manually or can be automated using specialized tools. We strongly believe that robust mobile app security testing is most beneficial when it is performed in-house and leverages as much repeatable automation as possible.
We built AppSweep with frequent automated testing in mind. Not only are the results actionable and developer-friendly, but we ensured that scans can be performed quickly as part of every CI/CD build. We also developed key integrations to popular CI/CD tools so you can automate scans for your entire team.
Additionally, as part of your scans, you can track the commit hash associated with a particular build to more easily identify when new security issues were introduced into your app.
Though there are certainly benefits to supplementing your testing strategy with external assessments and pen testing, using automation to ensure you're prepared for those assessments will significantly reduce the discovery of late breaking issues.




