iPhone runtime application self protection
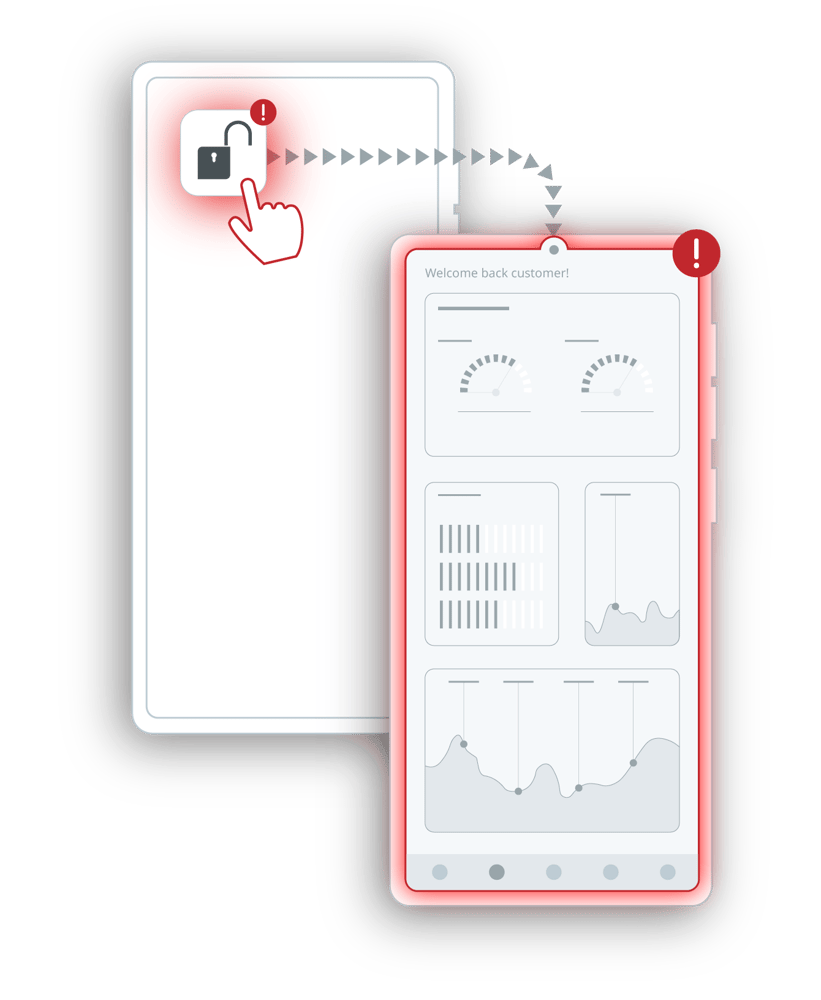
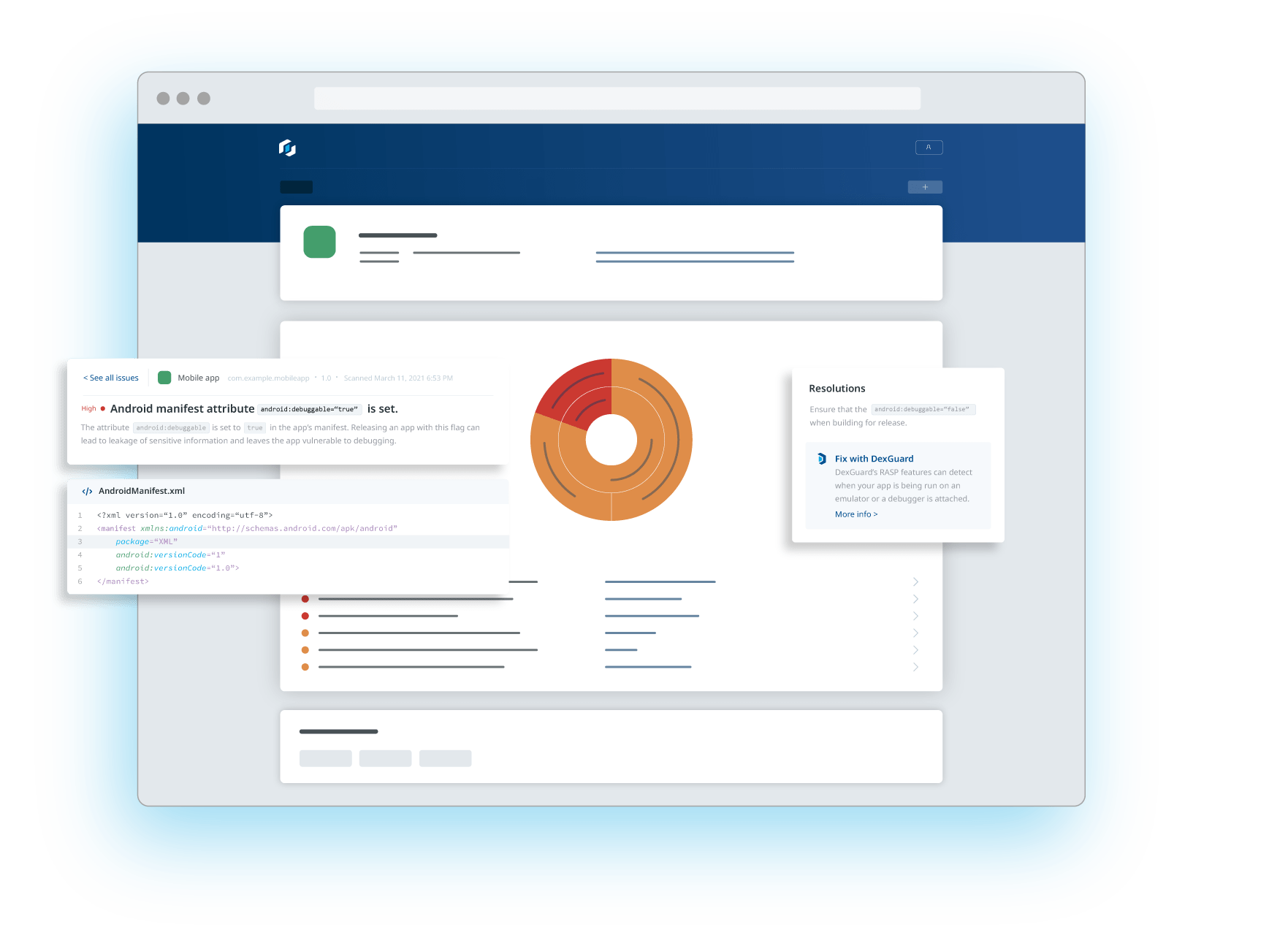
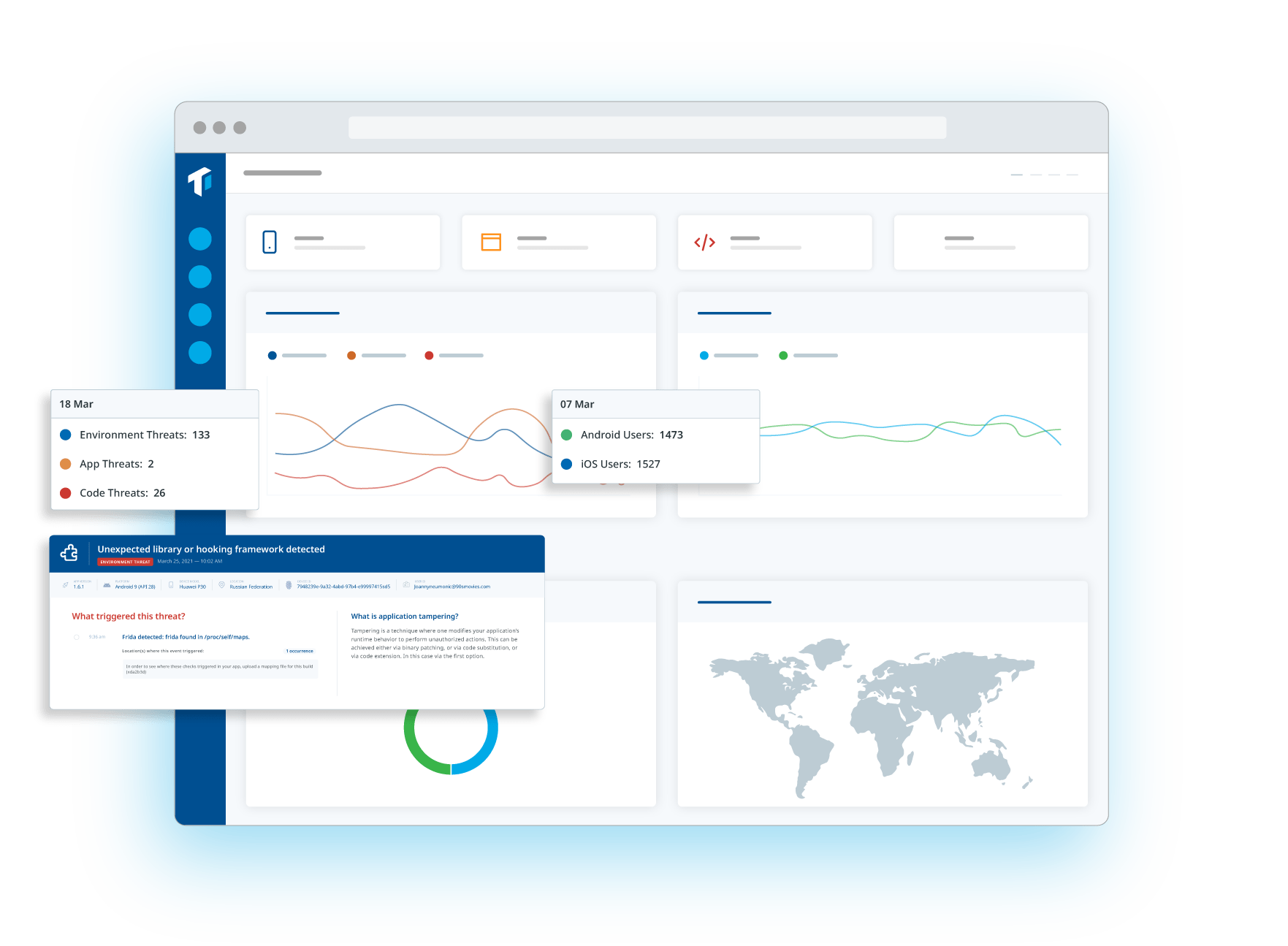
iPhone Runtime Application Self Protection (RASP) is a crucial security measure that helps safeguard iOS applications against runtime threats, such as code injection, reverse engineering, and tampering. Unlike traditional security measures that focus on perimeter defenses, iOS runtime application self protection operates within the app itself, continuously monitoring and responding to suspicious activity in real-time.
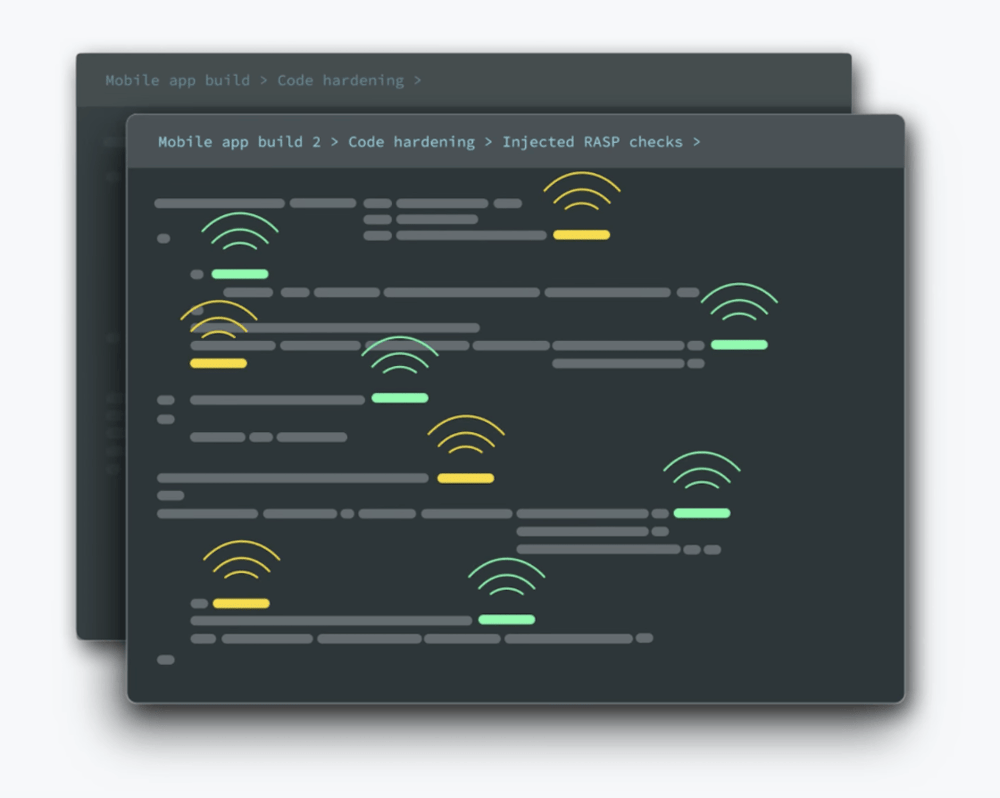
In iOS app development, integrating iPhone runtime application self protection ensures that applications can detect and mitigate threats dynamically, preventing attackers from exploiting vulnerabilities while the app is running. Key techniques include jailbreak detection, runtime integrity checks, obfuscation, and real-time threat analytics. These measures help developers enhance app security, protect sensitive data, and comply with industry regulations, making RASP an essential component of modern iOS security strategies.