Webinar Recap: Accessibility Features and Overlays on Android

Guardsquare security researcher and pentester, Jan Seredynski, recently discussed how attackers leverage accessibility features and overlays to exploit vulnerabilities in apps. The webinar, “Uncovering the Dark Side of Accessibility Features and Overlays on Android Apps,” began with a brief overview of the two common ways that attackers infect devices via an app:
- Exploits: Attackers search for vulnerabilities in messaging apps like Facebook Messenger, WhatsApp, or Telegram and send “malicious payloads” to users via the app. Once the user opens the app and interacts with the payload, the attacker is able to exploit the system, take control of the app, and infect the user’s device.
- App permissions abuse: When users download apps from the Google Play Store, the apps often ask for permissions. These govern what an app is allowed to do or access on the user’s device. These permissions, especially accessibility features and overlays, are sensitive and can be targeted by threat actors to gain access to and control of an app, ultimately infecting the device.
The focus of the webinar was permissions abuse, specifically accessibility features and overlays, so we’ll examine security concerns surrounding these services.
Seamlessly protect against malware with DexGuard’s built-in malware protection feature >
What are accessibility and overlay services?
Accessibility features are tools used by individuals with disabilities that enable them to interact with an app. This could look like an individual with visual impairment using accessibility tools to read the text on their phone’s screen, assist them in filling out forms, and make selections in an app.
Overlay services include permissions that allow one app to draw over another by creating an extra view layer over the host view. This is convenient for helping users interact with multiple apps at the same time. For example, a user may be searching for directions in Google Maps and receive an overlay message from Facebook Messenger. The Facebook Messenger overlay will appear on top of the Google Maps screen. Other overlay service examples can include a countdown or timer app that remains on your phone’s screen regardless of the app activity happening underneath.
Overlays have four general properties. While they have innocuous uses like the examples above, the following four properties can also be used by threat actors:
- Pass-through overlay: Touch events are forwarded through the overlay to the keyboard underneath. These are used as keyloggers to collect sensitive information.
- Non pass-through overlay: Touch events occur in the overlay and not on the screen underneath. These are made to model a login screen and effectively trick the user.
- Any-size overlay: The opposite of a full screen overlay, an any-size overlay does not fill the entire screen of a mobile device. A harmless example of this overlay could look like a small popup notification from your phone’s scheduling app, but also includes strategic use by threat actors such as covering portions of an app’s login screen to capture sensitive information.
- Full screen overlay: This type of overlay fills the entire screen of the mobile device. It can be used by threat actors for malicious purposes, like mimicking a banking app’s transaction page.
In the images below, you can see an example of both accessibility features and overlays. While both are considered to be convenient, and in the case of accessibility, vital for those with impairments, they’ve also been the source of global security incidents across industries like the examples below.
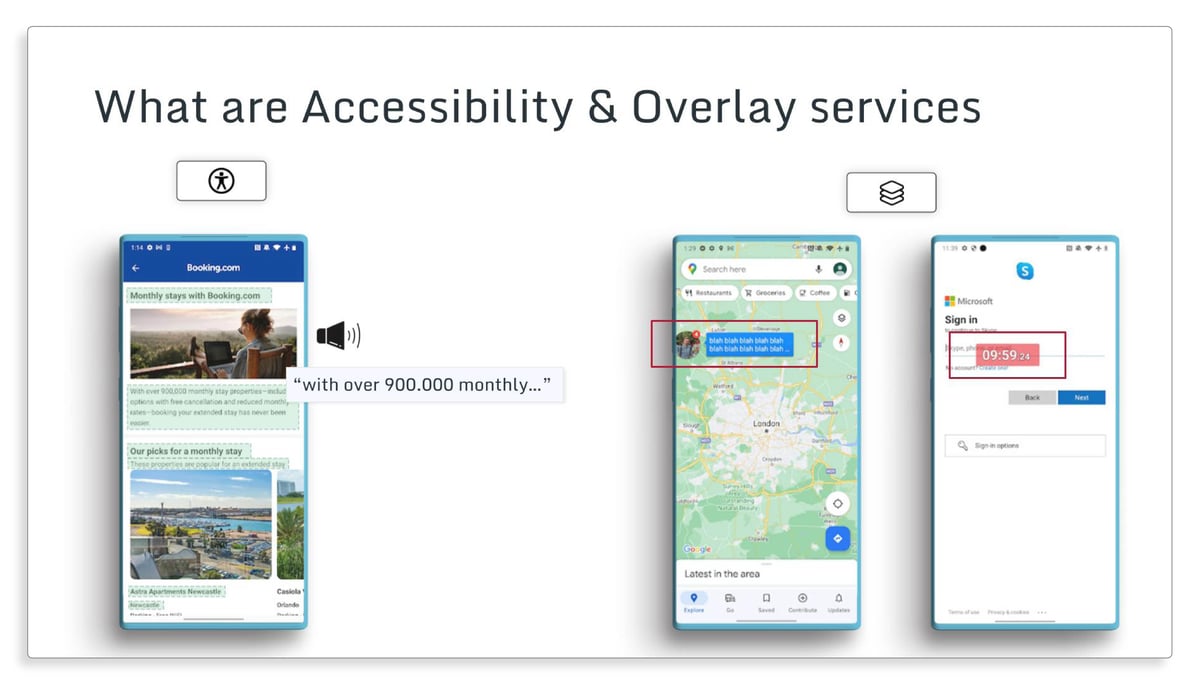
Examples of overlay and accessibility malware
When thinking about how threat actors leverage overlays and accessibility features to target user’s sensitive information, it can be helpful to review recent, real-world examples.
- BrasDex is a banking malware that targets Android operating systems and has been used to specifically target Brazilian banks. Once it has infiltrated the device, BrasDex searches for targeted apps (e.g., a banking app) and abuses Android Accessibility Services to read the device screen, manipulate the touchscreen, interact with the keyboard, and perform other malicious actions. The malware uses keylogging to record login credentials for users interacting with the banking app and make unauthorized transactions within the app.
- ERMAC 2.0 is an Android trojan used to steal login credentials from users and send them to threat actors. The credentials are used to take control of victims’ banking and cryptocurrency accounts and conduct various forms of fraud. The most widespread example of this is a fake app download found on a legitimate European food delivery service website. The fake app uses 43 permissions including access to accessibility services and overlays to steal users’ credentials.
- Xenomorph is still in use and operating under a new variant in 2023, though it first appeared a little over two years ago. In its earliest versions, the malware was distributed through the Google Play Store in the form of performance boosting apps. Users would download the app to improve their Android’s performance, and the malware would infect the device through the app’s permissions. The fake app can intercept text messages, which allows it to gather login credentials from banks. It also creates subtle overlays through the accessibility services permissions.
These are just a few of the examples of overlay and accessibility services malware in action. In the webinar, Jan demonstrated on his device how quickly accessibilities services could be used to navigate an unauthorized transaction — from start to finish, his example took mere seconds.
How are victims targeted?
If you’re looking to avoid falling prey to overlay and accessibility services malware, it’s best to avoid downloading an untrustworthy app from the Google Play Store or a third-party app source. Reading app reviews carefully, evaluating the app’s developers or providers, and avoiding apps that promise to bypass paywalls or offer free access to premium features are a few ways to avoid shady apps. When targeting victims with these types of apps, threat actors utilize two main approaches: creating a new malicious app or sideloading.
Example 1: Creating a new malicious app
Threat actors create malicious apps with “generic purposes.” An example of this is a simple flashlight or camera lens app. These apps ask for permissions to perform various actions on a device. For a few months, the apps perform as promised with no issues. Users are able to give honest feedback on the app’s performance, which boosts their profiles and encourages more users to download. After some time, threat actors will adjust the app and add malicious code or update permissions to infect the device. Waiting to add malicious code to the app allows threat actors to successfully pass the Google Play Store’s review process.
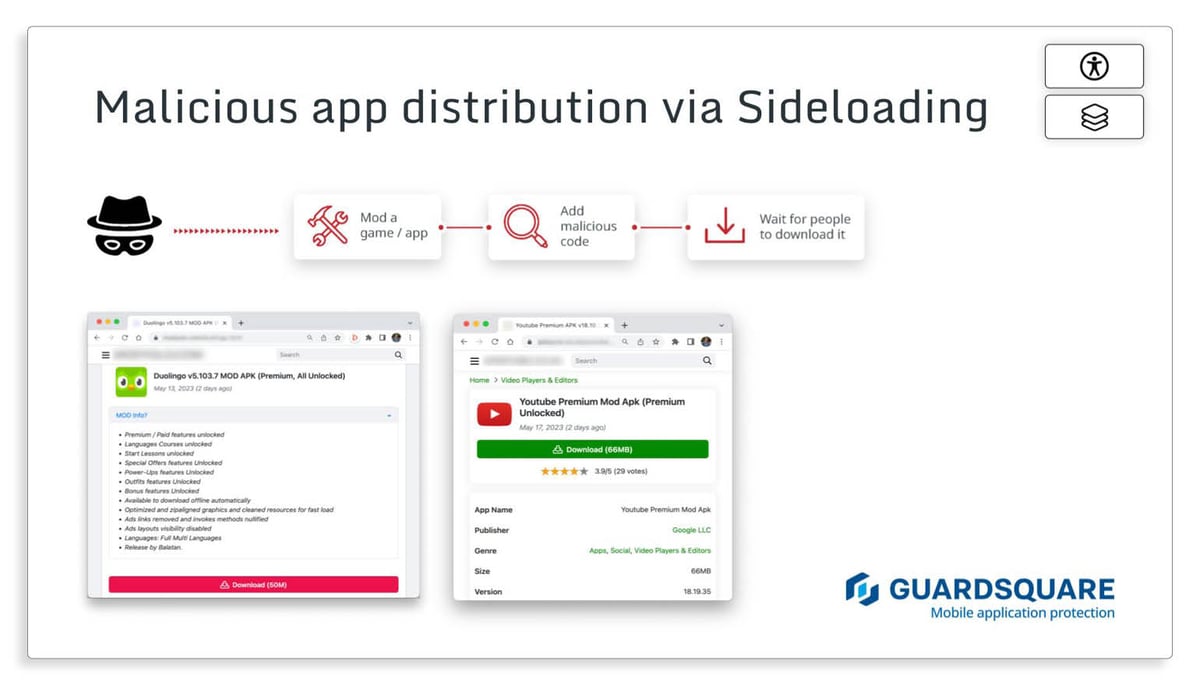
Example 2: Sideloading
Sideloading occurs when users looking to access restricted/elevated privileges on an app download an app outside of the Google Play Store. Examples of this include downloading a modified version of the popular language learning app Duolingo to access unlimited courses or a free version of YouTube Premium. Threat actors cleverly disguise permission requests to appear reasonable and necessary for the app to run properly. This could include enabling accessibility services to allow the free version of Youtube Premium to operate in the background or using overlays to remain in use while accessing other apps.
Defense against overlay and accessibility malware
Developers can also help protect against these types of malware with some simple steps to secure apps and devices.
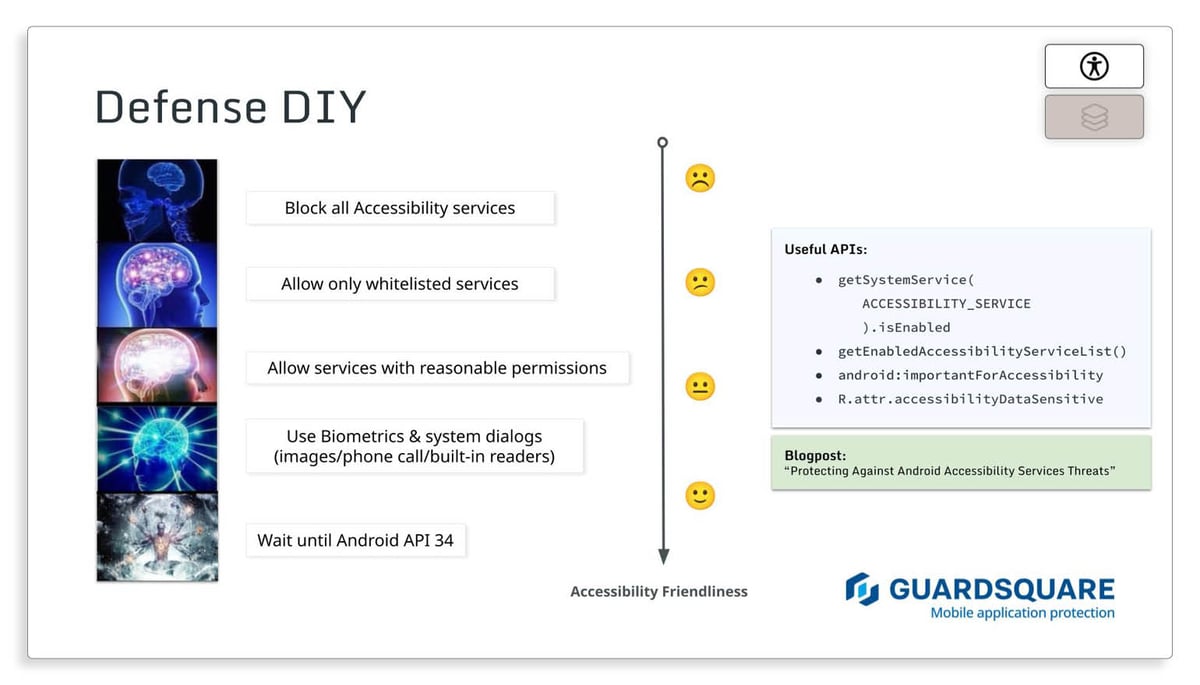
Accessibility defense tips
- Block all accessibility services: This option is the least friendly in terms of accessibility for impaired/differently abled users, but it’s one of the simplest ways to avoid permissions abuse.
- Allow only whitelisted services: With a friendlier approach to accessibility, this option uses the API to list all accessibility services, identifies the package IDs, and uses those to only allow certain trusted services to run through the app. However, sideloaded apps can impersonate any package ID, so this defense would protect only against threats coming from the Google Play Store.
- Allow services with reasonable permissions: You can take advantage of a flag (android:importantForAccessibility) that identifies important UI elements for accessibility services. Set it to “false” for all sensitive fields in your app and restrict accessibility services that declare interest in reading unimportant fields. You can do this by looking up the flags’ property of a service and verifying FLAG_INCLUDE_NOT_IMPORTANT_VIEWS.
- Use biometrics and system dialogs: Requiring and using biometric authentication for important transactions can help keep threat actors from using accessibility services to carry out unauthorized transactions in a user’s app. Also requiring the app to carry out transactions via system dialogs can effectively block overlays. Recent Android versions don’t allow overlays to operate on top of a system’s windows.
- Wait until Android API 34: Anticipated to drop later this year, this update ensures that only verified accessibility services can see and access sensitive information in an app.
Overlay detection recommendations
Google released a few useful APIs to help detect and deflect overlay malware attacks:
- API 9: When touch filtering is enabled with setFilterTouchesWhenObscured(boolean), the framework discards a user’s touches when the view’s window is obscured by an overlay. In this case, it’s another visible window (or toast/dialog) at the touched location.
- API 29: This update provides more precise detection of partially obscured touches by using a flag (FLAG_WINDOW_IS_PARTIALLY_OBSCURED) to indicate when a window receives a motion event that is partially or wholly obscured by another visible window. In this case, it’s important to note that the event is flagged if the motion does not directly pass through the overlay.
- API 31: This update provides developers with the setHideOverlayWindows(true) option to hide and automatically remove non-system overlays. It is currently the most powerful and effective approach.
For additional information on these defense tactics and how to implement them using the APIs mentioned above, check out our blog, “Protecting Against Android Accessibility Services Threats.”
Conclusion: Protection is a shared responsibility
The operating system, developers, and users all share responsibility in securing apps and devices against accessibility and overlay malware attacks. It is the operating system’s (Apple/Google) responsibility to provide a secure API. We see this in Android’s systematic API improvements over the years. The development team must mitigate known risks in their apps. This includes considering how threat actors may seek to modify their apps. Finally, users should be mindful of the type of apps they download, which includes avoiding sideloading apps and shady apps.
Want to learn more about permissions abuse? Access the full webinar here.
Executive Summary (TL;DR)
- Threat actors abuse mobile app permissions, which include overlays and accessibility services for impaired/differently abled users, to infect devices and steal user information.
- Threat actors target victims via new malicious apps uploaded to the Google Play Store or by modifying an existing app and sideloading it.
- Development teams can use Google-generated APIs for detection and defense against overlay and accessibility abuses, but the responsibility for security falls equally on the development team, user, and operating system.





