*Updated 2021 OWASP Top 10 Blog
The OWASP Mobile Top Ten 2016 is one of the go-to guidelines for making a solid mobile security plan. The list of the most critical security vulnerabilities for mobile applications will help you set priorities and make the right decisions in a world in which the words ‘mobile first’ and ‘security by design’ are on everyone’s lips. In this blog, we will take a closer look at the Mobile Top Ten and outline how an application shielding solution like DexGuard can mitigate some of the most pressing issues.
OWASP Mobile Top 10 2016
The 2016 edition of OWASP's Mobile Top lists ten risk categories you should check off your list when you are evaluating the security of your mobile applications. It looks as follows:
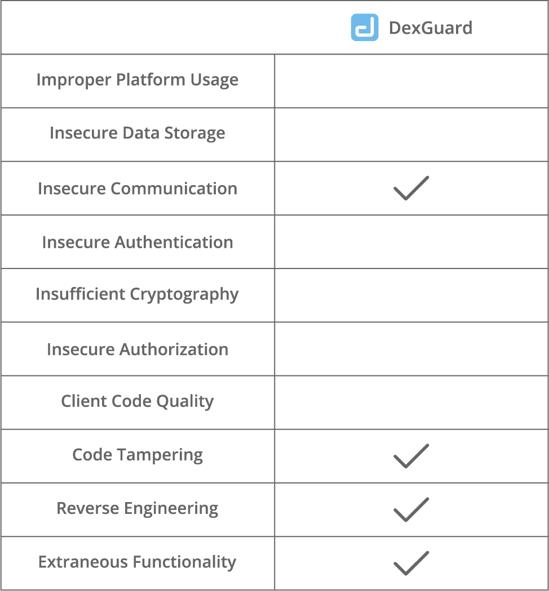
- Improper Platform Usage
Improper Platform Usage includes the misuse of a mobile operating system feature and the failure to use platform security controls. - Insecure Data Storage
This category covers insecure data storage and unintended data leakage. - Insecure Communication
This category encompasses any failure to ensure the security of data in transit, such as poor handshaking and incorrect SSL versions. - Insecure Authentication
Insecure Authentication refers to the absence or improper implementation of authentication mechanisms and to bad session management. - Insufficient Cryptography
This category covers failures to properly encrypt sensitive information assets. - Insecure Authorization
This category refers to the failure of a server to correctly enforce identity and permissions as defined by the mobile app. - Client Code Quality
Client Code Quality is an umbrella category for code-level implementation problems in the mobile app. - Code Tampering
Code Tampering covers the unauthorized modification of an application for personal or monetary gain. - Reverse Engineering
This category includes analysis of the final core binary to determine its source code, libraries, algorithms and other assets with the aim of exploiting vulnerabilities, harvesting sensitive data or stealing intellectual property. - Extraneous Functionality
This category covers the inclusion of hidden backdoor functionality or other internal development security controls that are not intended to be released into a production environment.
Reverse engineering and code tampering
Compared to the edition of 2014, OWASP’s 2016 Top 10 contains a couple of new categories. The most striking additions probably are the categories ‘Reverse Engineering’ and ‘Code Tampering’. Their inclusion in the Mobile Top 10 indicates both the increasing occurrence of these relatively simple attacks and the seriousness of their consequences.
To prevent mobile applications from being reverse engineered and/or tampered with, it is advisable to use an advanced app shielding solution like DexGuard during development. DexGuard hardens the code of Android applications (with obfuscation and encryption) to make it close to impossible to decompile the applications and analyze their source code. It also adds runtime application self-protection (RASP) functionality to shield applications from dynamic analysis. In addition, DexGuard allows you to realize gains on other security levels: it makes sure mobile applications connect to the intended server (SSL pinning) and removes logging, debugging and testing code to avert unintended information leaks.