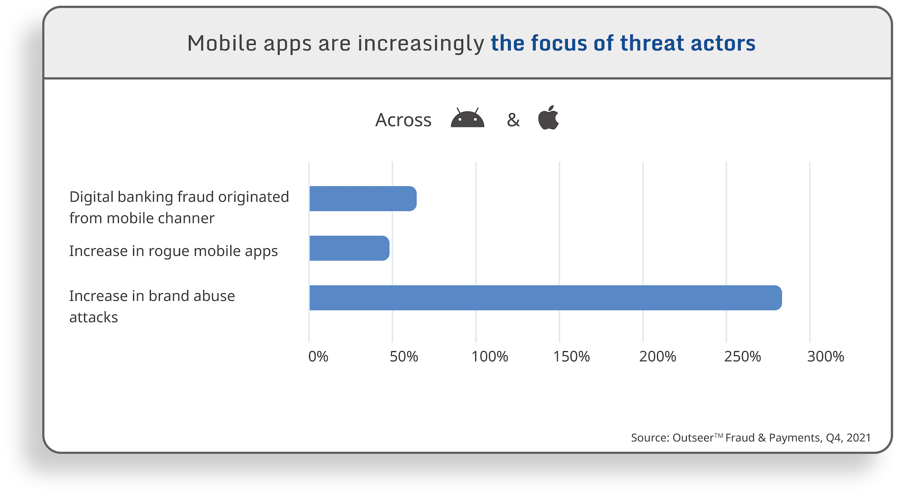
Cyberattacks increased by nearly 40% in 2022, further cementing cybersecurity’s place at the top of IT priority lists. The growth of mobile deserves particular focus. Mobile has seen 50% growth in screen time in the past 2 years, with 90% of that time spent on a mobile app versus a mobile browser. With the growth in mobile use, we have also seen significant growth in mobile attacks. 68% of digital banking fraud comes from a mobile channel and a 49% increase in rogue mobile apps. What might be most alarming is the 274% increase in brand abuse attacks. That is, attacks for the purpose of causing harm to the company, rather than for financial or personal gain.
This has driven the need in the mobile app industry for developers to continue educating themselves on all aspects of security, including understanding the threat landscape, implementing secure development best practices, selecting the appropriate protection mechanisms, and more. It’s a tall order, especially when developers are also racing to deliver a great UX on tight release schedules.
As they increase their focus on establishing a robust security posture, it’s important that developers place equal emphasis on addressing each of the three pillars of the mobile app security trifecta: protect, test, and monitor.
Three pillars of mobile app security
Mobile application protection
Most developers would agree that mobile apps need some level of protection, but the what, when, and how are another story. To answer these questions, developers need to perform threat modeling, a strategic information-gathering process to identify any vulnerabilities an attacker might seek to exploit and what methods they would use to do so.
With this information, developers can make informed choices about the right protections for their mobile applications, such as code hardening and RASP checks. But not all solutions are equally effective. Based on their threat model, developers should prioritize solutions that provide the level of protection their apps need, as well as being both customizable and robust.
Mobile application security testing [MAST]
There is a broad spectrum of approaches to mobile application security testing. Some developers opt out entirely, relying on the mobile device’s operating system to prevent attacks. Others prioritize testing, but wait until later in the development lifecycle when they submit their mobile application to thorough, but often costly, third-party pentesting.
Instead, developers can take security into their own hands by implementing testing best practices and security frameworks, like those proposed by OWASP, the Open Web Application Security Project. They should also consider integrating a testing solution that automatically scans their mobile app for vulnerabilities with each build. This testing solution serves as a great complement to pentesting, empowering developers to remediate vulnerabilities earlier in the process and allowing pentesters to focus on more advanced issues.
Mobile application threat monitoring
A developer’s work isn’t done when a mobile app goes live. The process of releasing new features, incorporating end user feedback, and patching vulnerabilities is a never-ending one.
After a mobile app has been released to the market, threat monitoring comes into play. A monitoring solution works to detect suspicious activity and usage patterns, providing a wealth of real-time information about threat actors, their devices, and methods of attack. It can also provide context around common threats, risk levels, and frequently targeted access points, all of which is useful for informing overall security strategy and future releases.
How to achieve defense in depth
At the end of the day, the most effective mobile app security strategy or tooling is irrelevant if developers are resistant to using it. To combat potential initial reluctance, organizations can select tools that integrate seamlessly into current workflows, are customizable to fit the unique needs of each mobile app, and provide actionable insights. However, it is important to also vet solutions carefully and be wary of any that prioritize simplicity over effectiveness.
For more on the mobile app security trifecta, use cases, and suggested tooling, check out our recent guide: Defense in Depth: A Layered Approach to Mobile App Security Architecture.