A lack of even the most basic security protections can leave Android apps vulnerable to reverse engineering and tampering by bad actors. These compromised apps can pose a major threat to consumers’ sensitive data if left unchecked. That’s why Google has recently taken some big steps to help consumers decide which mobile apps are trustworthy. The App Defense Alliance for Android’s Google Play store established the Mobile Application Security Assessment (MASA) earlier in 2023.
This optional assessment ensures that mobile applications are compliant with the industry standard for mobile app security, OWASP MASVS. After completing a third-party assessment, a mobile application can get a verification badge from Google.
Badges are starting to roll out with VPN apps, but are expected to expand to other app categories in 2024. For developers, these badges provide third-party validation that their apps meet the security baseline established by OWASP MASVS. The badge also gives app users peace of mind that certified apps are working to protect their data security and privacy. However, developers can (and should) go much further than the MASA certification to protect their applications and users from bad actors.
Not to mention,gaining certification may become costly, especially if your team isn’t prepared to solve baseline mobile app security issues on your own. Let’s learn more about MASA, and explore some ways developers can be more proactive about their security posture — moving beyond the basics and making their path to certification much simpler.
What does it take to become MASA certified?
Through MASA, Google will recognize developers who have had their applications independently validated against a set of MASVS Level 1 (L1) requirements. L1 is the broader baseline for mobile app security, in general. It’s important to note that since MASA was created, OWASP MASVS was updated. In MASVS 2.0, levels are removed and moved to the Mobile App Security Testing Guide (MASTG) to make them relevant and applicable to more application scenarios and security profiles.
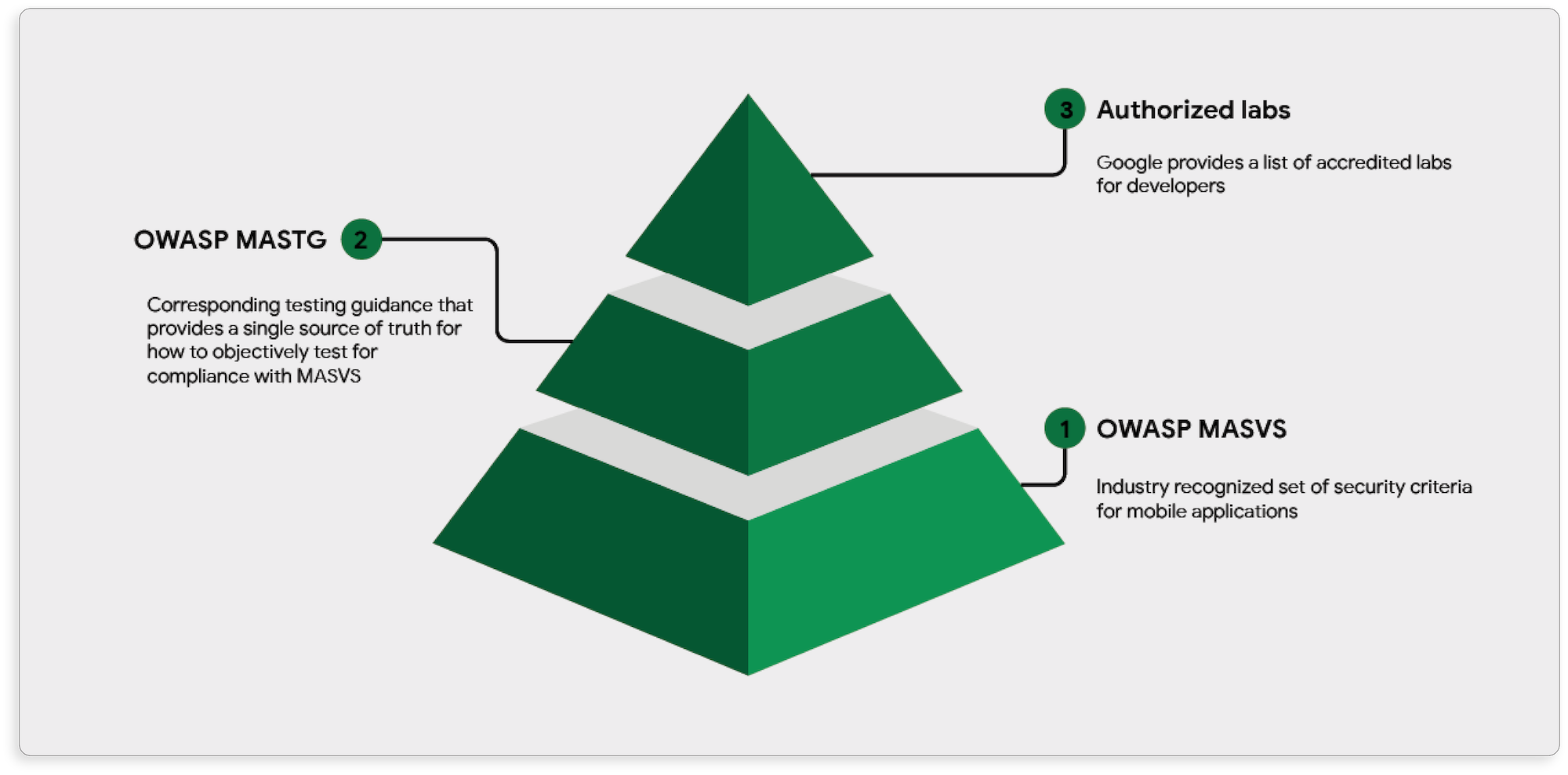 MASA framework
MASA framework
To receive a badge, apps need to be independently tested and verified by MASA lab partners. The verification process for MASA follows the MASTG, where lab partners use the guide’s objective security testing procedures to validate an app’s security. Mobile apps that pass all of the requirements gain MASA validation and get an independent security review badge, which is displayed in the Data Safety section of Google Play. However, mobile apps that do not pass will not receive a MASA badge. These developers can take the guidance from the evaluation and try again after they’ve enhanced their security practices.
Progressing security beyond MASA
While MASA is a good start toward providing app users with more comprehensive security guidelines, it may not be enough for certain types of apps that process sensitive data, such as financial services apps. Beyond L1 requirements, the OWASP MASVS model defined a far more robust set of standards as L2 (defense in depth) and L3 (resiliency against reverse engineering and tampering). Developers should still think beyond the baseline to protect their apps.
The good news? It doesn’t have to be difficult to maintain a proactive security posture. And, in doing so, it can make approvals for security reviews like MASA faster and far less costly.
Here are some tips on how to get proactive about your mobile app security:
-
Scan your application using free tools aligned with the full OWASP MASVS, such as Guardsquare’s AppSweep. These tools enable developers to efficiently understand the vulnerabilities associated with OWASP MASVS categories, and get recommendations for mitigation. Developers and security professionals benefit from a targeted, at-a-glance analysis and gain confidence in embedding security best practices in their mobile apps.
Moving beyond basic security protections, AppSweep users can also quickly evaluate their findings to determine if their applications meet deeper security criteria, including additional measures for apps that deal with highly sensitive data, and protection against client-side threats by setting reverse engineering resiliency requirements.
-
Deploy multiple layers of protection to meet OWASP requirements. Multiple layers of security protections reinforce one another, making it much more difficult for a bad actor to exploit an application. This approach redundantly protects the application, even if an attacker cracks one layer. These protections should include:
- Code hardening: Code hardening is the process of strengthening software to protect it against tampering, reverse engineering, and exploitation of vulnerabilities. By making the code more complex and less readable, hardening reduces the risk of malicious actors understanding and manipulating the app's functionality. Hardened code is more resilient to unauthorized modifications, ensuring the integrity of the app's operation and safeguarding against the insertion of harmful code.
- Runtime application self-protection (RASP): RASP integrates with an application to control its execution and detect and respond to attacks in real-time. RASP identifies and mitigates threats as they occur, offering immediate protection against attacks. RASP monitors both the app and the environment in which it runs, enabling more accurate threat detection and reducing false positives.
To sum up, independent security testing and badges like MASA are great tools for ensuring mobile apps meet baseline OWASP security standards. These types of standards give app users a way to determine that apps are secure, and that developers are serious about mobile app security best practices.
However, organizations should look beyond MASA and basic OWASP MASVS requirements. Technology like Guardsquare’s DexGuard can help development teams easily implement multiple layers of security protections, including code hardening and RASP, helping apps achieve full compliance with OWASP MASVS 2.0.





