Code Checksumming: Detecting Binary Patches to Your Code
Binary code patching
Binary code patching is a common and effective way attackers alter a specific part of a program’s code while keeping the rest of the code’s functionality intact. The program can be manipulated in place without requiring source code.
Common targets for binary patching include:
- Removing license checks from software
- Bypassing an application limitation
- Disabling ads
- Cheating in video games
Attackers may use well-known disassemblers or hooking tools to understand the code and implement binary patching. However, they can also use other non-standard techniques to implement binary patches, which may not be easily detectable.
Why hook detection techniques cannot detect all cases of binary patching
Binary patching is a rather overarching term and refers to altering compiled code. Its execution is broad and can be used in multiple contexts.
Hooking, on the other hand, is manipulating existing indirections to alter control flow in an application code. It is possible that a lot of hooks are executed through binary patching, depending on the indirection that is being abused in the code.
Only ensuring control flow integrity and preventing abuse of indirections is not enough. Developers need to verify the actual semantic integrity of pieces of code. Hence, the need for a technique that will enable you to detect if critical parts of your application code have been modified and enable the application to take appropriate action at runtime.
iXGuard, Guardsquare’s product for comprehensive mobile application protection, has a code checksumming feature specifically to address this.
What is code checksumming?
Code checksumming is a technique similar to application signing but can be used to detect changes made to the code at runtime, and it can be localized to specific sections of the software. It is based on calculating a hash of the code section you would like to protect and monitor. A simple explanation of how code checksumming works is:
- Calculate the checksum, or hash, of the compiled piece of code whose integrity you want to verify.
- Store the hash in the app package so it is available at runtime.
- At runtime, the checksum is automatically recalculated when it is checked for the same piece of code and compared with the expected value. Any changes to the code using binary patching will result in a different checksum.
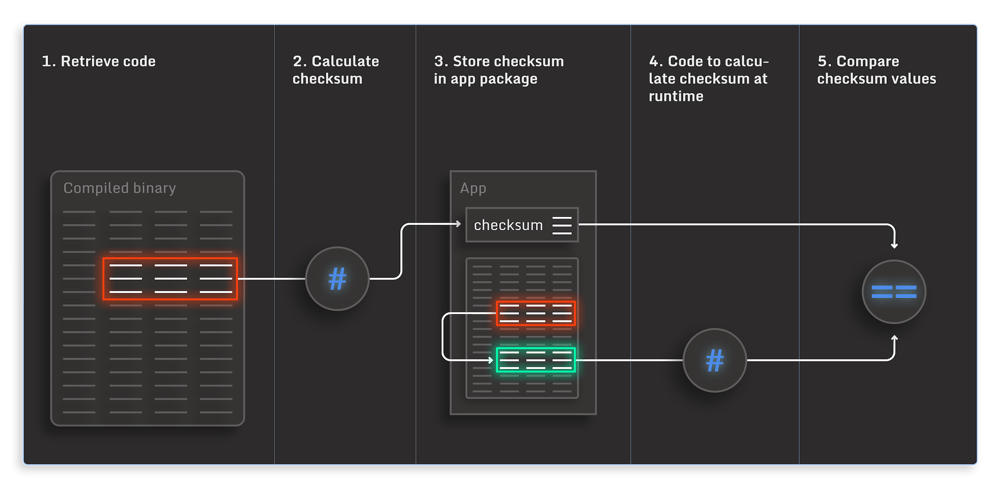
Thus, at runtime, this allows you to detect whether the part of the code in question was changed since it was compiled.
How can Guardsquare help?
Code checksumming is an essential capability for mobile app protection. As attackers are becoming more adept at understanding and modifying the code, even at runtime, code checksumming is critical in deploying a robust, multi-layer mobile application protection strategy.
A multi-layer approach consists of many different protections and checks executed in multiple places, so it’s harder for an attacker to work around all of them. Each of these different layers of protection reinforces each other. For example, a code checksumming verification is backed by hooking checks, tamper checks, and additional static protections. Code obfuscation makes it difficult for attackers to detect the checksumming checks and bypass them. This layered approach to security has proven to be most effective in protecting mobile apps against threats.
Guardsquare provides a comprehensive collection of products for protecting, testing, and monitoring mobile apps without significantly adding to a development team's work. The constant insights from our in-house security research team ensure our products and the protection of your mobile apps remain updated with the changing mobile app security landscape.
iXGuard enables mobile app developers to protect their applications against runtime binary patching through its code checksumming capability, among the rest of its rich set of other capabilities you can use to protect your app. Like the rest of iXGuard’s RASP capabilities, code checking will have minimal impact on your app’s performance because it requires very little compute resources and can be tuned by localizing them to specific code areas.
A more in-depth discussion of code checksumming and a lab can be accessed here.
Pro tip! Please note that code checksumming should not be misconstrued with code signing. Code signing is intended to verify the software publisher’s identity and certify that the software has not been changed since it was published. It cannot detect if the code has been modified at runtime. Code checksumming serves a similar purpose, also detecting runtime changes. Additionally, code checksumming enables app developers to specify a particular block of code over which we calculate the hash. Thus, developers can target specific areas of sensitive code and tune for any performance issues, making code checksumming manually configurable.





