Ensuring Security for High-Risk Mobile Apps in Singapore

Key takeaways
- The mobile app landscape faces ever-growing security threats. Authorities are responding by equipping developers with guidelines to ensure app safety.
- Singapore's Cyber Security Agency introduced the Safe App Standard, inspired by established frameworks like OWASP MASVS, MASTG, ENISA, and PCI DSS.
- The Safe App Standard focuses on high-risk mobile apps primarily dealing with financial transactions and sensitive personal data.
- The Safe App Standard offers developers a set of security controls to mitigate vulnerabilities, safeguard sensitive data, and provide implementation guidance.
- Here we explore the Safe App Standard framework, highlighting key security controls and provide recommendations to help developers best comply with the standard.
What is the Safe App Standard security framework?
What the goal of the standard is
The Safe App Standard, developed by Singapore's Cyber Security Agency (CSA), aims to strengthen the security of mobile applications that handle sensitive personal information and financial transactions such as personal identifiable information (PII), encryption keys and authentication credentials.
To whom the standard applies
This standard serves as a guide for mobile app developers in Singapore, equipping them with best practices. Organizations adhering to the guidelines benefit from protecting their app code and user data from threat actors. Additionally, they are able to demonstrate their commitment to mobile app security, enhancing app reputation and user trust. A well-protected app can lead to increased adoption and user engagement through increased security of their financial data and transactions, reduced risk of financial loss, and instilling confidence in mobile transactions.
What the standard recommends
The Safe App Standard focuses on security controls in four key critical areas for mobile apps:
- Anti-Tampering & Anti-Reversing: Safeguarding an app against unauthorized modifications and code manipulation; this includes security controls to check rooting/jailbroken devices, detecting emulators, hooking frameworks, malware using overlay attacks, screen recording or keylogger.
- Authentication: Ensuring there are strong user identification and access control mechanisms in place such as use of multi-factor authentication, use of location-based access control and protection against brute force attacks.
- Authorization: Defining and enforcing clear permissions for user actions within the app. For example, in this category the Standard recommends device binding to make sure that only authorized devices connect to a specific server.
- Data storage at rest: Implementing secure measures to protect sensitive data at rest such as the use of Trusted Execution Environments to store sensitive data on a phone, tokenization and data encryption are a few examples.
As the cyber threat landscape evolves, the CSA anticipated that the Standard will be continuously updated to reflect emerging risks and ensure ongoing protection.
Recommendations to comply with the Safe App Security standard
Anti-tampering and anti-reversing
To comply with the Safe App Standard's anti-tampering and anti-reversing requirements, it is recommended that runtime application self-protection (RASP) capabilities be combined with code obfuscation techniques. By following these recommendations, developers of apps can mitigate the risk of attackers:
- Decompiling the app to steal trade secrets, financial information, or other sensitive data.
- Tampering with the app during runtime to steal money during transactions or collect personal identifiable information.
Guardsquare’s DexGuard for Android and iXGuard for iOS provide developers with obfuscation and RASP capabilities to fulfill the Safe App Standard requirements of this category.
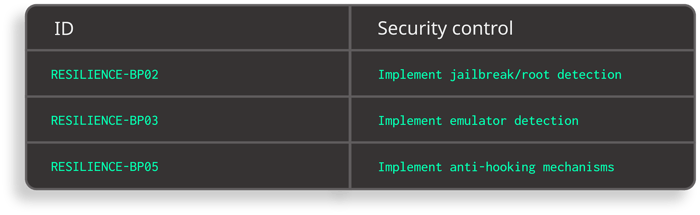 Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
In addition to that, another aspect of the Standard Guardsquare supports is related to preventing unauthorized app resign.
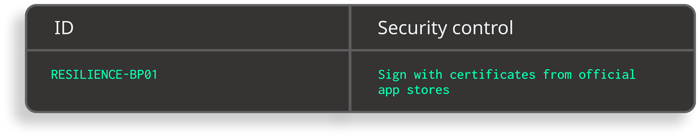 Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
Moreover, in this category, the Safe App standard recommends implementing measures against malware:
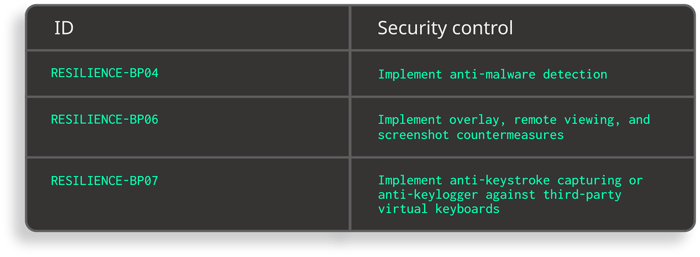 Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
Guardsquare's security research team provides developers with implementation guidelines to mitigate malware threats and a secure keyboard to use every time the user is asked to input sensitive data.
Authentication and authorization
In these categories, the Safe App Standard provides developers with implementation guidelines, such as implementation of different factors for multi-factor authentication and authorization via device binding:
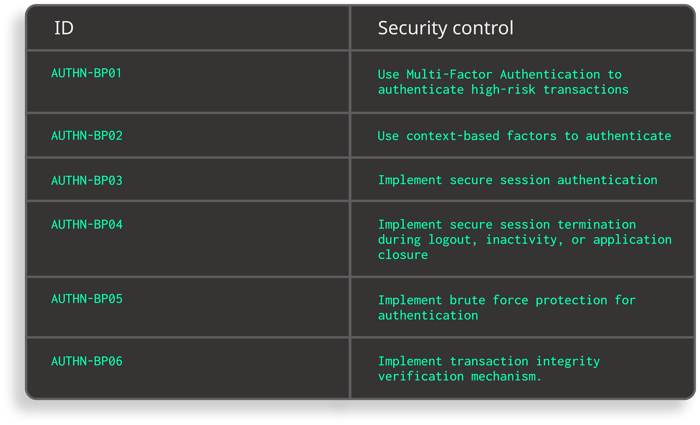 Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
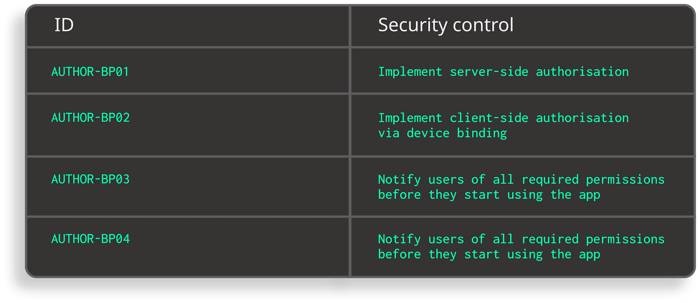 Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
The use of anti-tampering and anti-reversing mobile application protection solutions help developers safeguard their implementation of the requirements in these categories.
Data storage at rest
Since mobile apps are subject to Man-at-the-end attacks, the Safe App Standard recommends storing data on the server as a best practice:
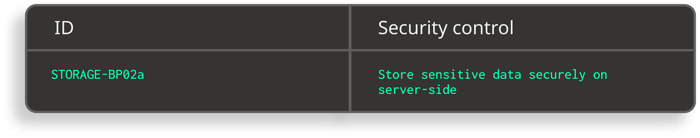 Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
If that is not possible, the standard suggests limiting the data stored locally and deleting it as soon as it is no longer necessary.
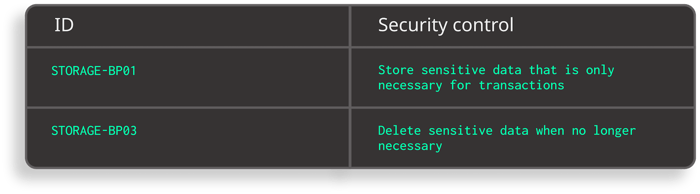 Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
When storing data locally, the Safe App Standard recommends using hardware-backed isolation which creates a secure enclave within the device where sensitive data can be stored and processed. Both Android and iOS provide a Trusted-execution environment to achieve that goal.
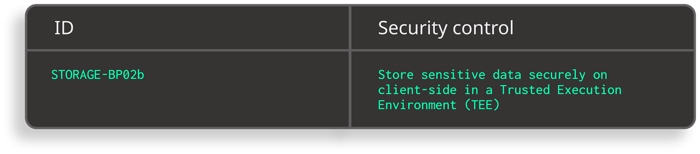 Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
To address all these requirements, a robust mobile application protection solution can further enhance data security by providing data encryption: this renders stored data unreadable even if attackers gain access to the device.
 Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
Excerpt from Safe App Standard - Anti-tampering and Anti-reversing requirements
Proactively identifying and addressing security issues related to the Safe App Standard's critical areas is crucial for building secure apps. This can be effectively achieved by integrating mobile app security testing (MAST) throughout the entire development lifecycle. MAST involves analyzing mobile app's code and dependencies to uncover vulnerabilities early on when they're easier and cheaper to fix. This prevents them from evolving into major problems later, such as:
- Costly remediations: Rushing to patch critical issues after a failed audit can be expensive and time-consuming.
- Real-world exploits: Unidentified vulnerabilities are like open doors for attackers, potentially leading to data breaches or financial losses.
Benefits of incorporating MAST throughout the development process include:
- Early detection and prevention: Detect vulnerabilities early and fix them before they become exploitable.
- Reduced costs: Proactive fixes are significantly cheaper than reactive remediations.
- Enhanced security posture: A secure app fosters trust and protects user data and financial information.
Remember, integrating MAST from the start isn't just a best practice, it's a cornerstone of building secure and compliant apps under the Safe App Standard.
Conclusions
Developing high-risk mobile apps, like those under the Safe App Standard, demand robust security to safeguard sensitive information. Make sure you have a comprehensive strategy with the right tools and expertise needed to build trust and comply with regulations. An example of these tools include:
- Mobile application protection
DexGuard and iXGuard, built respectively for Android and iOS, protect mobile apps against reverse engineering, tempering and other threats.
- Free mobile app security testing
AppSweep scans apps’ code and dependencies early in development, uncovering vulnerabilities before they become costly problems. Actionable recommendations help developers fix the discovered vulnerabilities quickly and efficiently.
By combining these tools with expert guidance, developers can confidently meet the requirements of the Safe App Standard and adhere to global best practices like OWASP MAS.




