Malware Dropper Applications
The main channel of malware dropper distribution is Google Play Store, where inconspicuous “dropper” apps are uploaded.
Threat actors often disguise these malicious apps as genuine apps, with functionalities such as calculators or QR code scanners.
Once a malware dropper app is downloaded and run by the unsuspecting user, the malware will be unpacked and loaded onto the device.
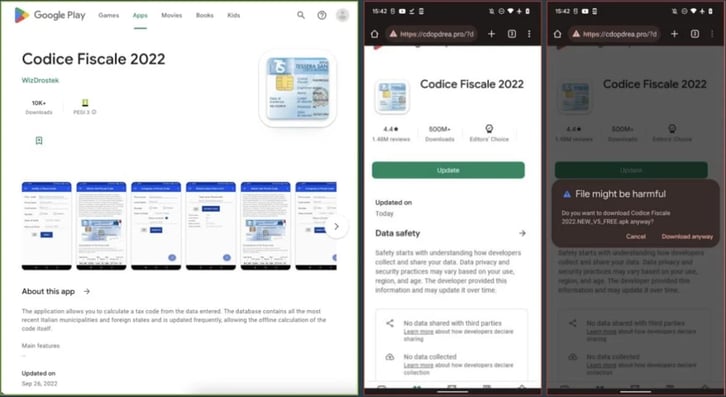
Dropper app example - Codice Fiscale, targeting users in Italy (source: ThreatFabric)
When malware is installed, it can exhibit more behavioral patterns, such as:
- Downloading modules from a C&C server
- Gain administrator privileges
The main purpose of malware on the device is to perform specific attacks (see the overview).
The proliferation of malware dropper applications is the primary reason why treating sideloaded apps as apriori malicious and Google Play apps as apriori safe is not a working approach.




