Window punching
| Technique summary | |
| Technique | Window punching |
| Against | UI injections: Activity injections and View injections |
| Limitations | API Level ≤32 (Android ≤12) |
Cannot have INJECT_EVENTS permission |
|
| Does not detect non-touchable overlays | |
| Side effects | False positive on API Level ≤28(Android ≤9) when switching between apps while the protected activity is on screen |
| Recommendations | Recommended for use combined with other techniques |
Window punching is a defense technique used against activity and view injections.
This technique was proposed by AlJarrah et al.1 and endorsed by Kalysch et al.2. It relies on the possibility that the android.app.Instrumentation API provides a way to simulate touches on the screen. An application can generate touches only on views that belong to itself. In order to do that on external views, the INJECT_EVENTS permission is needed. Thus, an app can simulate touches ("punches") on specific areas of the screen and, if it touches a view that belongs to a different application, a SecurityException exception will be raised, indicating that injecting to another application requires INJECT_EVENTS permission.
That behavior is used to detect the presence of an overlay or injection. Thus, if we throw punches on, e.g., a password field, and we see an exception, we will know that there is an injection or overlay positioned over that field.
This code snippet would simulate one punch in specific coordinates:
And to trigger a burst of a specific number of touches on a specific area:
Bursts of touches can be launched at specific time intervals, and if an exception occurs, it will lead to a detection.
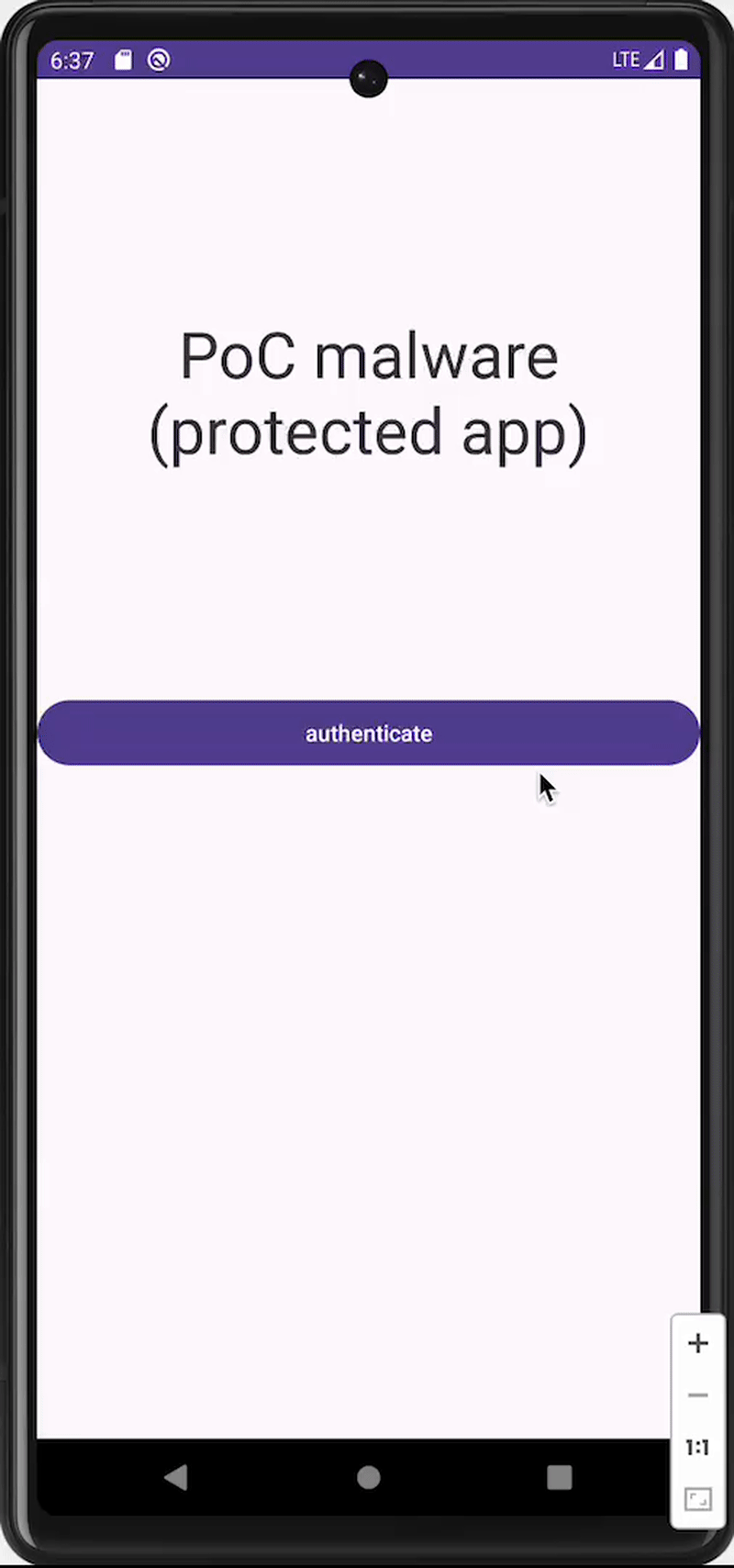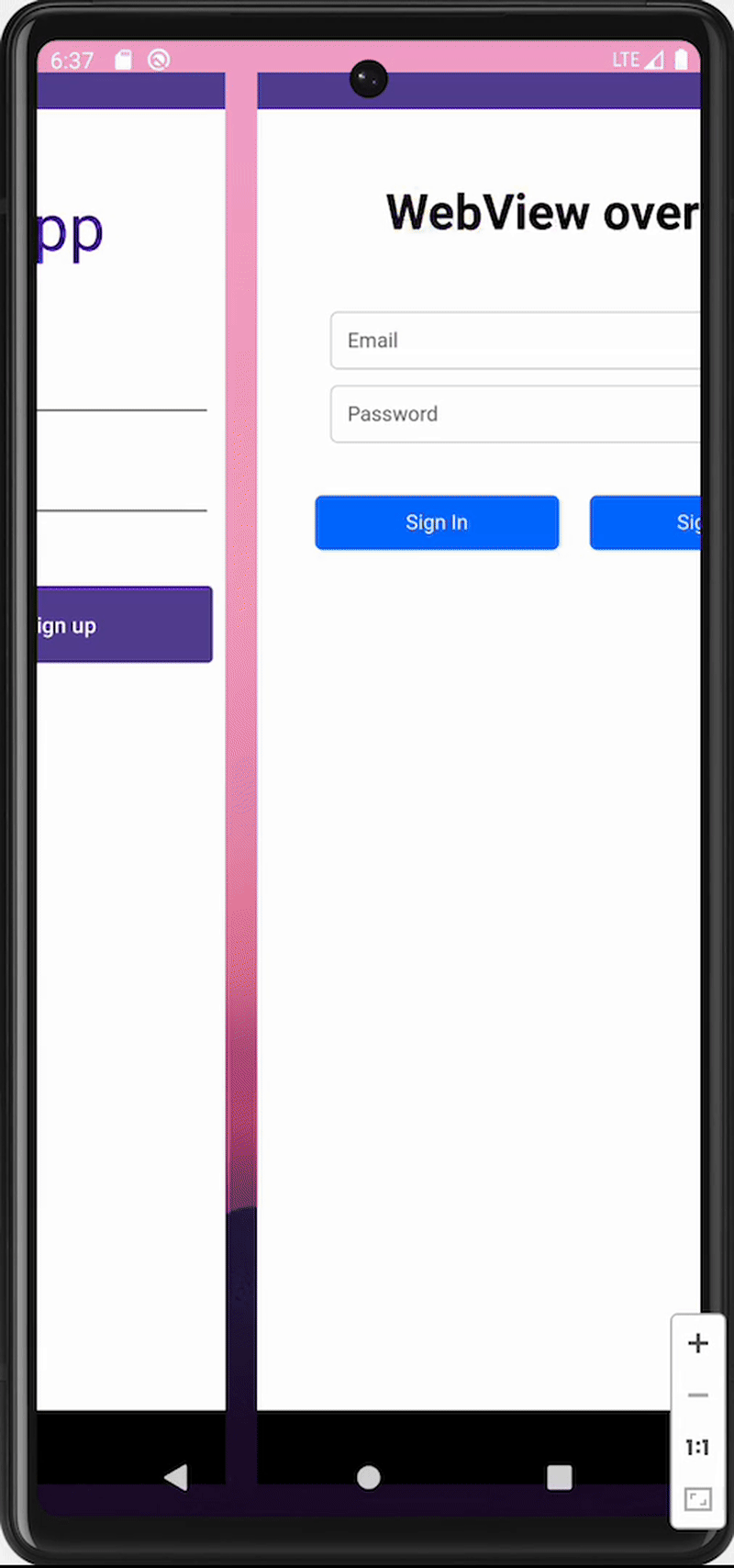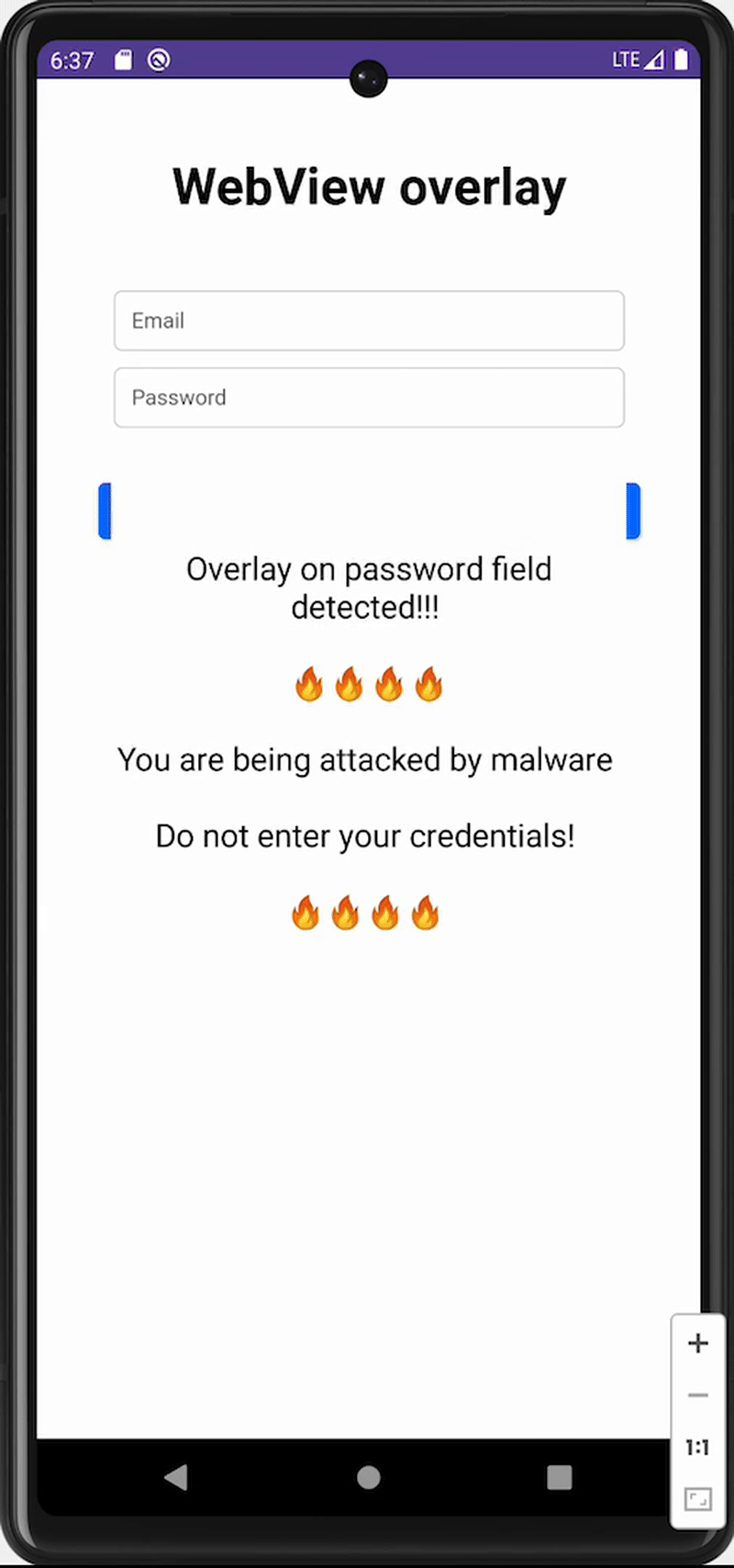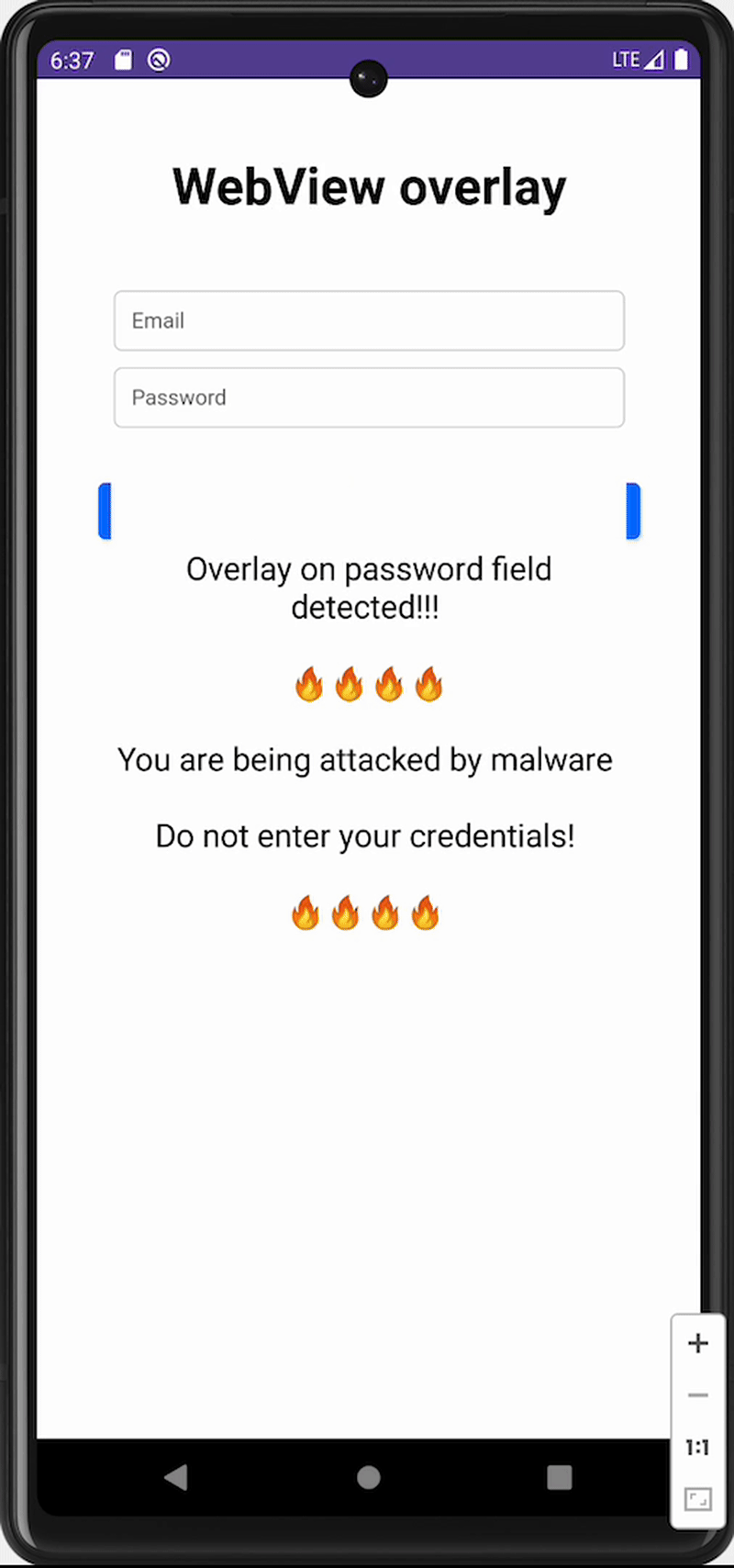
Example implementation of top package inspection defense
One limitation is that this mechanism does not work from API level 33 (Android 13) onward. In this case, the exception is generated even when trying to simulate touches on the same application.
1. AlJarrah, Abeer, and Mohamed Shehab. "Maintaining user interface integrity on Android". 2016 IEEE 40th Annual Computer Software and Applications Conference (COMPSAC). Vol. 1. IEEE, 2016.↩2. Kalysch, Anatoli, Davide Bove, and Tilo Müller. "How android's UI security is undermined by accessibility". Proceedings of the 2nd Reversing and Offensive-oriented Trends Symposium. 2018.↩




