Screen recording attacks
A feature commonly integrated into malware is the screen capture capability, which is used to steal sensitive data. The screen content can usually be streamed to the command-and-control server by the administrator commands from the admin panel.
One example of a real-world application of a screen recording attack is keylogging. Screenshots below demonstrate how the standard keyboard in Android ≤11 leaks information about the pressed keys.
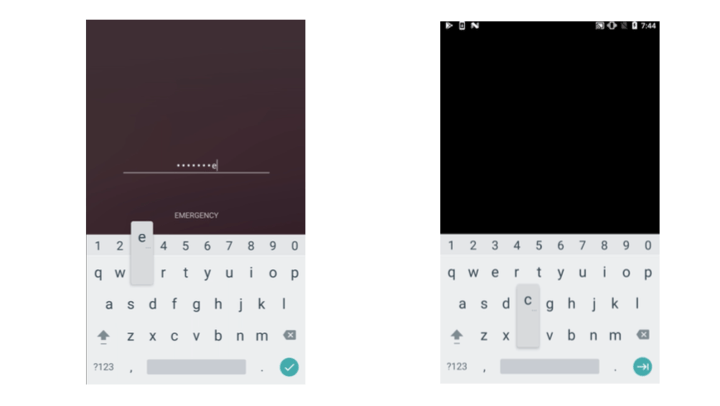
Left: Unprotected view. Right: Protected view leaking information through the keyboard.
Defense techniques overview
---
title: Spying on users' data with overlays
---
graph TD
all[All malware attacks] --> steal_screen
click all href "/mobile-app-security-research-center/malware/overview" "Malware overview"
steal_screen[Spy on users' screen]
steal_screen --> screen_rec[Screen recording]
screen_rec --> screen_rec_api31{API Level < 31?}
screen_rec --> flag_secure([FLAG_SECURE ⭐])
screen_rec_api31 -- Yes --> secure_keyboard([Secure in-app keyboard])
screen_rec --> screen_rec_api35{API Level ≥ 35?}
screen_rec_api35 -- Yes --> screen_rec_callback([Screen recording callback])
style flag_secure fill:lightgreen
style secure_keyboard fill:lightgreen
style screen_rec_callback fill:lightgreen
click screen_rec_callback href "/mobile-app-security-research-center/malware/screen-recording-callback" "Screen recording callback"
click flag_secure href "/mobile-app-security-research-center/malware/secure-flag" "Secure flag"
click secure_keyboard href "/mobile-app-security-research-center/malware/secure-in-app-keyboard" "Secure in-app keyboard"
Guardsquare
Connect with the author
Table of contents




