Malware behavior patterns overview
Many malware examples share a common pattern in deploying the malicious capabilities, which is based on acquiring accessibility capabilities as the initial step.
The strategy to achieve this is by bothering the user through continuous notifications and/or windows popping up, prompting the user to grant accessibility capabilities for the malicious application.

Malware using webviews, notifications, and toasts to prompt the user to grant accessibility capabilities
Once this first milestone has been reached, the malware will start abusing accessibility capabilities. On one side, clickers are used to self-grant permissions and become a device admin app, as well as to prevent the user from taking any action that could jeopardize the malware, such as: permission revocation, uninstallation, etc. For instance, if the user tries to access the malware application settings, the malware will click the “go backward” button. On the other side, keylogger mechanisms are activated.
Clicker behaviors are illustrated in the picture below.
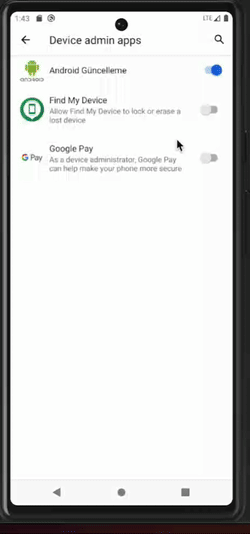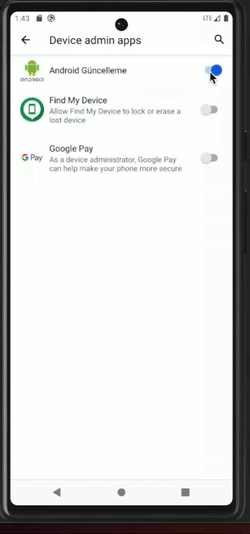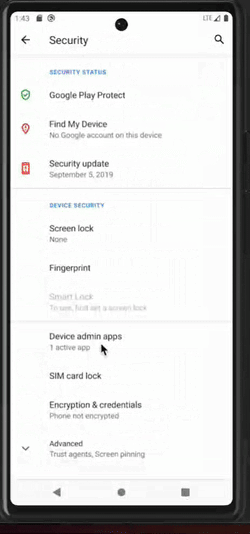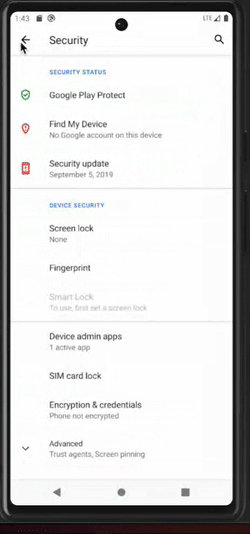
Malware clicker undoes the user's action to remove privileges
In parallel, the malware starts collecting information about the device and attempts to establish communication with its command and control (C&C) server. If this communication succeeds, the malware will send the collected information and the server will send new modules or “injections” (if any) for any identified target, such as a particular bank application.
Apps executing in the foreground are monitored via accessibility services and, whenever a target application appears, an "injection" will be overlaid at the right moment, e.g. mimicking the login screen.
All retrieved data is then sent to the server.




